Key Points
- NPS with Azure AD (Microsoft Entra ID) has limits in scalability and security, particularly for modern networks.
- Cloud RADIUS provides a simpler, more secure authentication solution that works perfectly with Azure AD.
- Improve your network security by switching to a cloud-based RADIUS solution for greater scalability and administrative simplicity.
Since cloud-based solutions are becoming the norm today, knowing how different identity and access management tools work together and what they do is important. This article details Microsoft NPS (Network Policy Server) and Azure AD (Entra ID), two infrastructure elements important to secure networking.
Microsoft’s RADIUS server, NPS, has been an important part of on-premise setups for a long time. On the other hand, Azure AD, Microsoft’s cloud-based identity provider (IDP), is the successor to Active Directory and provides identity infrastructure for the cloud.
While Azure AD and Microsoft NPS can potentially integrate, problems and risks are involved — especially the need for NPS extensions for Azure MFA — to make this change possible. As we travel through the complex terrain of this integration, we will discover different weaknesses and problems that organizations must manage, making it necessary to critically examine whether this route is appropriate for your digital infrastructure.
NPS and Azure AD: A Blend of Traditions and Innovation
NPS in Traditional On-Premise Environments
In standard on-premise IT setups, NPS, or Network Policy Server, has been the trusted RADIUS solution for many years. Think of it as a virtual doorman who checks to see who can come in and who can’t. NPS was the best way to track who could get into the network and what they could do once they did.
Traditionally, Microsoft NPS operated with Active Directory, forming a strong partnership that permitted on-premise 802.1X security. This dynamic pair guaranteed that only authorized people and devices could connect to the network, providing an important layer of protection.
However, given the developing world of modern network security, the conventional on-premise configuration faces new issues, particularly as organizations consider moving to cloud-centric identity solutions like Azure AD . This transformation necessitates a more in-depth examination of Microsoft NPS and its significance in modern network systems.
Click here to learn more about NPS and the issues associated with it.
Transitioning to Cloud-Centric Azure AD
The cloud has recently been a popular topic of conversation, altering how businesses handle identity management. Microsoft Azure AD addresses the cloud-based paradigm change. Microsoft announced Azure AD as a future-proof, cloud-based replacement for the more established Active Directory (AD), designed mainly for on-premise usage. This transition indicates a fundamental shift in how identity and access management functions.
Azure AD was developed from the ground up to function in the cloud so anyone can use it anywhere. In contrast to its on-premises analog, Azure AD is based on the principle that users should be able to access resources from any location. However, when businesses transition to the cloud, they frequently encounter complex hurdles when integrating Azure AD with legacy systems like NPS.
NPS’s on-premises 802.1X security model isn’t a good fit with Azure AD’s cloud-based infrastructure. Businesses often use extensions as the connecting link between NPS and Azure AD. As we will see in the next section, this is not a simple path.
Migrating to a cloud-based architecture requires more than merely incorporating Azure Active Directory. It’s difficult to strike the right balance when deploying an on-premise, self-managed RADIUS server like Microsoft NPS in a cloud-first infrastructure.
Managing the interaction between on-premises components and a cloud-facing configuration can be challenging. To better understand the challenges businesses encounter when bridging the gap between on-premise and cloud-centric identity management, we will discuss the specifics of NPS extensions for Azure MFA in the next section.
What On-Premise NPS with Cloud-Facing Architecture Looks Like
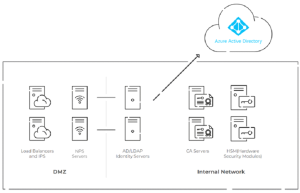
In the diagram above, you can see one possibility for the overall layout of your authentication infrastructure if you’re using on-premise NPS with cloud-based Azure AD and digital certificates for passwordless authentication. The self-managed RADIUS architecture shown above requires hosting infrastructure in local data centers or cloud providers, using a DMZ for security, PKI/CAs, and HSMs for passwordless authentication — all of which may become difficult and expensive to operate. The setup for this type of infrastructure is costly and complex, and using a managed cloud-based RADIUS solution like Cloud RADIUS makes the transition to the cloud simpler.
The Role of NPS Extensions in Making the Switch
So, what about organizations that have used Microsoft NPS for years but now want to move to the cloud-based world of Azure AD as smoothly as possible? Here is where NPS extensions come into play. NPS extensions are very useful add-ons that help bridge the gap between NPS and Azure AD so that they can work well together.
Making NPS extensions more compatible and useful is key to making the switch to Azure AD easier. These extensions are meant to make NPS more powerful and work well with Azure AD based on different rules. They act as interpreters and help NPS understand and speak Azure AD’s language. This ensures that the login and authorization processes work together smoothly. Some extensions worth mentioning are those for Multi-Factor Authentication (MFA), which improves security in a cloud-based setting.
But, like any change, the move from on-premise to cloud comes with challenges. NPS extensions open up a world of options, but they can also make things more complicated. In the following sections, we’ll discuss the technical details and risks of integrating NPS and Azure AD, illuminating the complexities organizations must deal with when starting this transformative journey.
The following diagram illustrates the high-level authentication request flow:
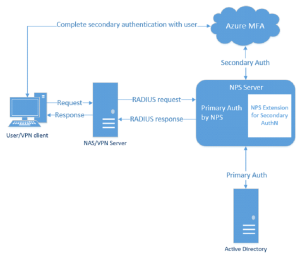
The Technical Challenge of NPS Extensions
Integrating Azure Active Directory with NPS extensions is a complex technical task that requires more than just an awareness of the underlying technology. Compatibility considerations between NPS and Azure AD must be well understood.
When connecting Azure Active Directory with NPS extensions, it’s important to consider that NPS depends on Active Directory and cannot interact directly with Azure AD. Common challenges include resolving device identification difficulties, facilitating communication across varied devices like Chromebooks and Macs, and managing the complicated rule sets and login mechanisms inside NPS. Even tiny configuration errors might make a system susceptible to devastating security threats.
Additionally, authentication failures and associated security breaches may be avoided with careful attention to attribute mapping, network connection, certificate management, and efficient error handling. Not only do administrators tasked with this integration need technical skills, but they must also keep up with the latest threat landscape of their infrastructure and take a preventative approach to monitoring and troubleshooting.
Implementing NPS extensions for Azure MFA integration successfully requires a comprehensive strategy to overcome these technological hurdles. To ensure safe communication, administrators must carefully establish attribute mappings, keep networks running, and keep certificates current. They need to deal with the complexities of numerous devices and have error management and monitoring systems in place.
Setting up a reliable test environment before releasing updates into production may help discover and fix problems before they affect users’ ability to log in without trouble. While technical expertise is key, avoiding and fixing these frequent problems is just as important for a smooth integration of NPS and Azure AD.
If you need to create High Availability on your network, you can create as many Microsoft Entra multifactor authentication-enabled NPS servers as you need. But more servers means multiplied efforts of the above-mentioned activities. For example, if you install multiple servers, you should use a different client certificate for each one.
The Drawbacks of NPS Extensions for Azure AD
While NPS extensions seek to streamline the move to Azure AD, they are not without limitations. The integration procedure can rapidly become painful if authentication fails and there are problems with the user experience. Imagine users being denied access to crucial resources or delayed due to compatibility issues.
There could be the possibility that some RADIUS attributes configured in Network Access Policy do not flow properly to RADIUS Clients like VPN Gateway. This may result in users either having more access, less access or no access to corporate resources at all. In such situations, you’ll have to run a script as directed by Microsoft for MFA to work smoothly, which is yet another overhead on admins.
Regardless of the authentication protocol (PAP, CHAP, or EAP), if your MFA method is text-based (SMS, mobile app verification code, or OATH hardware token) and requires the user to enter a code or text in the VPN client UI input box, authentication may be unsuccessful. Any RADIUS characteristics set in the Network Access Policy, on the other hand, are not transmitted to the RADIUS client (the Network Access Device, such as the VPN gateway). Consequently, the VPN client may have more access than you wish, or less access, or none at all.
As a workaround, run the CrpUsernameStuffing script to forward RADIUS attributes configured in the Network Access Policy and enable MFA when the user’s authentication method requires the use of an OTP, such as SMS, a Microsoft Authenticator passcode or a hardware FOB.
If you want to enable MFA for some RADIUS clients but not others, one needs to configure two NPS servers and install the extension on only one of them. This is an extra burden on administrators.
Furthermore, to enable a plethora of MFA methods (phone call, one-way text message, mobile app notification, OATH hardware tokens, and mobile app verification code), one needs to choose PAP in their NPS configuration. PAP is a well-known legacy authentication protocol that sends all the authentication information in plain text — and needlessly exposes your network to the possibility of MITM attacks which could easily occur.
Additional Vulnerabilities Associated with NPS and Azure AD Integration
Integrating on-premises infrastructure with cloud services like Azure AD might provide certain security problems due to variations in design and authentication processes. Microsoft NPS was built for on-premise deployment, making it incompatible with Azure AD’s cloud-based architecture.
Attempting to authenticate and authorize using two completely separate systems is like trying to unlock a safe with two separate sets of keys. This may lead to a disjointed security environment, making it harder for businesses to manage who has access to what. Attribute mapping problems, protocol incompatibilities, and the necessity for encrypted data transfer between on-premises and cloud-based systems all fall under the category of often-encountered authentication challenges.
To overcome these obstacles, businesses must often introduce intricate infrastructure solutions to close the gap between their current on-premises systems and cloud-based alternatives. To guarantee safe and reliable data transfer between NPS and Azure AD, it may be necessary to use specialized technologies and protocols.
In addition, businesses need to be watchful in maintaining modernized security measures and adjusting to the changing dynamics of the cloud. As the threat continuously evolves, organizations may be exposed to new and emergent security risks if they rely solely on the convenience of conventional on-premises infrastructure. Maintaining a strong security posture in today’s hybrid IT settings, therefore, requires a proactive approach to security and a comprehensive awareness of the complexities of combining on-premise and cloud-based systems.
Understanding NPS Authentication Methods
The password encryption is used between the RADIUS client (VPN, Netscaler server, or other) and the NPS servers.
- PAP supports all Microsoft Entra multifactor authentication in the cloud authentication methods: phone calls, one-way text messages, mobile app notifications, OATH hardware tokens, and mobile app verification codes.
- CHAPV2 and EAP support phone calls and mobile app notifications.
It may also be difficult to provide a consistent user experience across all users’ devices, such as Chromebooks, due to NPS extensions’ limited support for different operating systems. Compatibility concerns, like Chromebook’s binding to the active directory, might throw a wrench into the works, creating friction in the login procedure.
Challenges of NPS Authentication on MacOS and Chrome
Testing Procedure for MacOS Version 12 – Monterey
The MacOS version 12 testing technique, codenamed Monterey, found issues with NPS authentication. Despite the easy integration of a MacOS device into AD (JNOW), efforts to authenticate by the user ‘TestMacOS’ were unsuccessful.
Potential Keychain Issue
Internal research revealed that there might be a problem with the way the Monterey OS version stores keychain data, which is slowing the NPS authentication process. However, further study into the core cause was impossible due to restricted access to OEM resources.
Compatibility Concerns with MacOS Versions
Testing the authentication on an older MacOS version, Sierra, was effective as a workaround, as evidenced in the video below. Administrators must extensively test for compatibility before introducing NPS authentication for Mac devices.
ChromeOS Version 110 and AD Management
According to Google’s latest statement, ChromeOS device management using Microsoft Active Directory (AD) will be discontinued beginning with ChromeOS version 110. As a result, users can no longer enroll devices in AD mode or log into their AD-managed ChromeOS devices.
Migration to Cloud-based Chrome Management
To guarantee continuing operation, organizations that use AD-managed Chromebooks should immediately move to cloud-based Chrome management and upgrade all devices to ChromeOS version 110.
Navigating the Dependency on Active Directory
Organizations must deal with a major dilemma in their effort to fully use the potential of Azure AD and NPS integration: their continuous reliance on Active Directory (AD). Traditionally, NPS and Active Directory have been used together to achieve 802.1X because they are on-premise Microsoft products designed to work well together. But in a modern, cloud-based world, on-premise infrastructure such as Active Directory has its drawbacks.
Active Directory and other on-premises servers need specialized hardware, software, and a substantial investment in time and money from IT staff. High availability and security are an organization’s duty and are not easy to achieve.
In addition, downtime and productivity losses might come from infrastructure failures or attacks on the premises. On the other hand, Azure Active Directory is a cloud-native option that may do away with costly and time-consuming on-premise hardware and maintenance.
Scalability, high availability, and automated upgrades are just some of the problems that cloud computing solves, eliminating the need for on-premise computers. To successfully integrate NPS in the contemporary cloud environment, businesses must take an introspective look at Active Directory, acknowledging its value and possible limits.
Azure AD promises modern identity and access control in the cloud, but organizations that still use AD may be stuck between two worlds with hybrid on-premise and cloud environments. This mixed method can complicate operations, especially if on-premise operations need to be kept up. This adds another layer of complexity to an organization’s IT environment missing the common security best practice of keeping things simple.
Transitioning from NPS to Implement RADIUS Authentication in the Cloud
Moving from a conventional NPS (Network Policy Server) to a cloud-centric authentication solution, such as SecureW2’s Cloud RADIUS, necessitates fundamental modifications in strategy. Instead of merely being a connection tool, Cloud RADIUS is a complete replacement for NPS.
Using digital certificates for further security, it works on the same idea as passwordless authentication. These certificates adhere precisely to the Zero Trust Network Security principles since they only broadcast their public keys, which makes them immune to credential theft.
Cloud RADIUS’s connectivity with Azure AD is a major benefit. It integrates seamlessly with Azure Active Directory, enhancing security and the user experience, using existing policies. The real-time user lookup tool against Azure AD ensures that only the right people can log in, making the system safer overall.
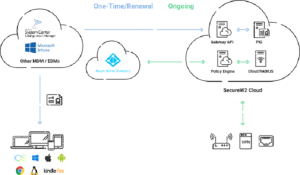
Cloud RADIUS integrates Mobile Device Management (MDM) gateways and a powerful access policy engine made specifically for Azure Active Directory into its authentication features. This all-encompassing method aligns with current best practices for network security and makes it easier to deploy certificate-based security, allowing for a safe and secure move to the cloud.
SecureW2’s Cloud RADIUS provides the necessary Public Key Infrastructure (PKI) components, onboarding solutions for mobile device management (MDM) and BYOD, and a fully working RADIUS server for implementing certificate-based authentication. This method ensures that your move to the cloud is safe and compliant with current standards for network security while also making the implementation of certificate-based security easier.
Navigating the Path to Secure Cloud-Centric Authentication
Our exploration into integrating NPS with Azure AD has shown some risks and problems organizations may face during this critical transition. We’ve peeled back the layers to reveal how hard it is to connect standard on-premise setups to Azure AD’s cloud-based world. Many things could go wrong, from technical issues to security risks. The most important thing is to make this change safely.
Moving to the cloud is unavoidable; the key is ensuring the move is safe. Deciding too quickly can leave you open to risks you didn’t expect. As stated, Cloud RADIUS by SecureW2 emerges as a strong ally, streamlining the changeover while boosting security. It’s the key to a safe and smooth trip to the cloud.
Contact our experts if you need help making your network more secure and switching to the latest, safe authentication.