Key Points
- Traditional password-based authentication is highly vulnerable to security breaches and phishing attacks, making it inadequate for protecting sensitive information.
- PKI tokens provide a robust solution by serving as a secure hardware device that stores cryptographic keys and digital certificates
- SecureW2s Managed PKI solution automates the entire lifecycle of the digital certificates they store.
Today’s world relies heavily on online interactions, such as collaborating with family, friends, and colleagues on social media or checking our bank accounts. However, this ease of use raises security concerns. We need a way to ensure that only authorized people have access to our sensitive information online, similar to how you lock your door every night.
This is where PKI (Public Key Infrastructure) comes in. PKI, or Public Key Infrastructure, refers to a collection of tools and standards that are employed to establish a secure online communication environment. Consider it an effective lock and key system for the digital world.
The PKI token is an essential tool in the PKI toolbox. Consider a PKI token to be a secure keychain containing a unique key that allows you to verify your identity online. In this article, we will look at what PKI tokens are, how they work, and why they are becoming more important for strong online security.
What is a PKI Token?
Imagine carrying a small digital vault in your pocket. That is essentially what a PKI token is! Unlike typical keys, PKI tokens have distinct digital keys that allow access to secure online environments. These tokens are small hardware devices that often resemble USB sticks or key chains.
Most people log in to websites with usernames and passwords, but hackers and phishers can get that information and use them to attack. PKI tokens add an extra layer of security. They store safely two important parts for strong authentication:
- Digital Certificates: A digital certificate is like an ID card. It has information about the person who owns the token, like how your driver’s license does. This certificate comes from a reputable source
- Cryptographic Keys: These are complex mathematical codes that come in pairs: public and private keys. The public key is freely available, but the private keys are kept secure within the PKI token. This key pair works together to provide secure communication and verification.
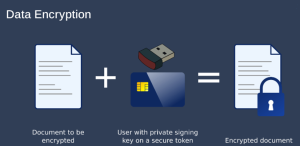
Figure: Thanks to Microcosm
How Does a PKI Token Work?
Let’s say you’re entering a high-security building and a security guard asks you to provide you additional identity rather than asking for your name. For safe online access, PKI tokens work in the same way. This is how the magic works:
- Digital Certificates and Public Keys: When you try to access a secure online resource, the system will first verify your digital certificate. This certificate, which is stored within your PKI token, serves as your online identification and verifies your legitimacy.
- Public Key and Private Key: The system then issues a unique challenge, such as a random number. Your PKI token encrypts this challenge using the secure hardware inside, which contains your private keys. Remember that your private key is like a secret signature; only you and the token have access to it.
- Verification and Access: The encrypted message is transmitted back to the system. The system then decrypts the challenge using the public key from your key pair. If the decryption matches the original challenge, it means you have a valid private key associated with the digital certificate. This successful verification validates your identity and allows you to access the secure resource.
This two-key system provides a significant security advantage over usernames and passwords. Hackers cannot access the private keys stored within the PKI token, making it much more difficult to impersonate you and gain unauthorized access.
Why Do You Need a PKI Token?
In the digital world, we live in now, security breaches and data leaks are all too common. PKI tokens are a great way to add an extra layer of protection. Many people are turning to PKI tokens as a security measure because of these reasons:
Enhanced Security for Sensitive Information
PKI tokens are especially useful for getting into sensitive locations. Imagine financial institutions, government agencies, or healthcare providers. These organizations deal with a lot of private information, and PKI tokens are an important security measure for getting into these systems.
Two-Factor Authentication (2FA)
Many online services now provide two-factor authentication, which requires more than just a username and password to prove your identity. As that second factor, PKI tokens are great at this job. Since the private keys are stored in the physical token, you need to have it to log in. This makes it much less likely that someone will get in without your permission, even if your password is stolen.
Reduced Risk of Phishing Attacks
Phishing scams try to get people to provide their credentials to login on to fake websites. Phishing attacks are much less likely to happen with PKI tokens because they use cryptographic verification and don’t require entering passwords on websites that aren’t trusted.
While PKI tokens offer enhanced security benefits, it’s important to consider potential drawbacks. For example, PKI tokens can be lost or stolen, and some users may find them less convenient than traditional password-based logins.
Hardware PKI Tokens: Ensuring Secure Access Control
Physical PKI tokens serve as the main tools for ensuring secure online authentication. Unlike traditional authentication methods such as usernames and passwords, the use of physical devices adds an extra layer of security that requires the presence of the device along with a PIN or other credentials. Let’s explore the key features that make hardware PKI tokens so effective:
Physical Security
Hardware PKI tokens are enclosed in a customized housing built to resist tampering attempts. This presents a challenge for potential attackers who want to breach the token’s security and pilfer the cryptographic keys that are stored inside.
Technology for Ensuring Security
The core component of every PKI token is a secure element, which is a specialized chip specifically designed for cryptographic operations. The secure element ensures the cryptographic keys are separated from the token’s operating system, rendering them nearly impossible to access by malware or unauthorized individuals.
Multi-Factor Authentication
PKI tokens are highly effective in two-factor authentication (2FA), as they require the use of both the physical token and a PIN for login. Certain advanced tokens provide multi-factor authentication that goes beyond 2FA, which improves security with an additional layer of protection.
There are multiple PKI token options available on the market today. Examples include things such as Yubikeys.
PKI Token FAQs
What is a PKI Token?
A PKI token is secure hardware like a USB drive or keychain fob and is used to store digital certificates. The foundation of asymmetric encryption that makes certificates possible allows for the use of secure access to private resources and the generation of digital signatures.
What Does PKI Card Stand For?
PKI card is another term sometimes used interchangeably with PKI token. Both terms refer to the physical hardware that stores cryptographic keys and digital certificates.
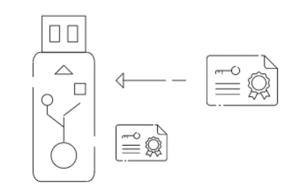
How Do You Use PKI Authentication?
PKI token authentication typically involves inserting the token into a computer and entering a PIN. The token then uses cryptography to verify your identity and grant access to the secure resource.
What is a Token in PKI?
In PKI, the token refers to the physical hardware device (e.g., USB drive, key fob) that stores digital certificates and cryptographic keys used for authentication.
What is the DoD PKI token?
DoD PKI tokens are purpose-built for secure authentication and authorization to U.S. Department of Defense networks and resources. These tokens comply with strict security standards and protocols required by the Department of Defense (DoD).
What is a PKI and How Does It Work?
Public Key Infrastructure or PKI is a system that utilizes digital certificates and public/private key cryptography to establish trust and secure online interactions. Consider PKI a digital lock and key system. PKI tokens hold secure keys, allowing authorized users to access resources through cryptography.
Simplify PKI Token Management with SecureW2’s Cloud PKI Service
While SecureW2 does not offer PKI tokens, our managed, cloud-based PKI solution connects perfectly with these devices to improve security and management. Our system automates the issuance, renewal, and revocation of digital certificates, ensuring that your PKI tokens such as Yubikeys are always current and safe. SecureW2 makes deploying PKI tokens across your organization easier by automating procedures and integrating real-time data from your Cloud Identity. This allows for passwordless access to Wi-Fi, VPNs, and other essential resources such as desktop logon with little effort and maximum security. By utilizing SecureW2’s powerful infrastructure, you can decrease the complexities and expenses associated with standard PKI configurations while maintaining high security.
SecureW2’s cloud PKI solution is intended to give a user-friendly experience while reducing the technical strain on your IT staff. Our platform includes a centralized dashboard for handling certificates, allowing you to monitor and handle authentication events throughout your network easily. Whether you work with managed or BYOD devices, our API-driven solution enables smooth certificate enrollment and lifetime management. This complete solution enables you to focus on your main business operations while we handle the complexities of PKI administration, improving your organization’s security posture and operational efficiency.
Contact us to learn how SecureW2 can help you with your smart card management and leverage the security of digital certificates.