Key Points
- A Certificate Authority (CA) is an entity that distributes digital certificates to devices, ensuring secure network communication.
- Managing a CA requires expertise in Public Key Infrastructure (PKI), which can be complex and resource-intensive.
- Utilize tools like Microsoft Certificate Authority or OpenSSL to establish and manage your own CA, providing greater control over your network's security.
What is a Certificate Authority?
A certificate authority (CA) is an entity that distributes digital certificates to devices. A digital certificate certifies the ownership of a public key by tying it cryptographically to the subject it is administered to. Certificate authorities are essential for running a PKI and thus essential for having a secure network.
SecureW2 Cloud PKI service allows you to create CAs and distribute certificates with ease. It’s also cheaper than on-premise alternatives as maintaining a cloud PKI costs ⅓ of the price of an on-prem PKI, see how we helped one of our customers here.
It is important to be aware that there are two different kinds of CA’s; a public CA and a private CA. While both certificate authorities, their practical uses differ and are used for different purposes. You can even import CA’s from other management services like AWS or AD CS and issue client certificates from our management portal.
A Microsoft Certificate Authority is about the same as a private CA except that it uses Microsoft’s Azure AD Domain Services (AD DS) used for Microsoft-based environments can implement a Public Key Infrastructure (PKI) with AD CS.
In this article, we will highlight when to use a private CA and how to go about creating one.
Why Use A Private Certificate Authority?
Private CAs, also known as Enterprise CAs, are self-hosted certificate authorities usually meant for internal use only. They are most commonly used by large companies or universities and for applications such as Wi-Fi, VPN, or Web Application authentication.
While there is little benefit from a software perspective, the benefit that comes from using a private CA is that it limits trust to devices within a given organization. This reduces the potential for a breach because fewer devices means access points for security breaches.
To enhance your security further, you can set policies that will help reinforce your network against would-be attackers.
If you foresee needing to issue a high volume of certificates, either because your organization is massive or your certs will need to be reissued frequently, it can be cheaper to run your own CA than to pay for every certificate issued by a public CA.
Private CAs can also be significantly more secure than their public counterparts. Where a public CA hands out certificates to anyone who pays, private CAs restrict their certificates to specific people or devices (usually those within the organization).
Generating Certificate Authorities Without A Service
It is possible to create a private certificate authority without soliciting help from outside services, but the process isn’t as straightforward as one would hope. It also differs depending on which operating system you are using. For example, for macOS:
- Open a Command Console
- Enter openssl genrsa -des3 -out myCA.key 2048
- When prompted, enter your passphrase
- Generate a Root CA by entering openssl req -x509 -new -nodes -key myCA.key -sha256 -days 1825 -out myCA.pem
- Enter in answers regarding Name, Location, State, Organization, etc.
The easy stuff is done; now you have to install your Root CA on the devices in your network. To add the Root CA for macOS:
- Open the macOS Keychain app
- Go to File > Import Items…
- Select your root certificate file
- Search for whatever your CA name
- Double click on your root certificate in the list
- Expand the Trust section
- Change the When using this certificate: select box to “Always Trust”
- Close the certificate window
- Enter your password
While the actual generation of root CA seems simple enough; the challenge comes from installing the root to all the devices in your network. For an enterprise company, this could mean thousands of devices need to be manually fitted for certification. This solution also offers no mechanisms for certificate revocation and management. With the average number of certificates an organization manages growing 43 percent in 2020 this simply isn’t a cost-effective solution for larger companies.
Luckily, SecureW2 offers an alternative solution that you can use to create and deploy a private CA in minutes. SecureW2’s system also comes with a full suite of management options that allow you to fully control your network.
Managing your Private CAs and Client Certificates
SecureW2’s Managed PKI solution simplifies the way you manage your CAs. We provide you with an easy-to-use graphical interface that allows you to view and manage your certificates in a simple way. You can see when a certificate was issued, what device it’s attached to, and even revoke the certificate with a push of a button.
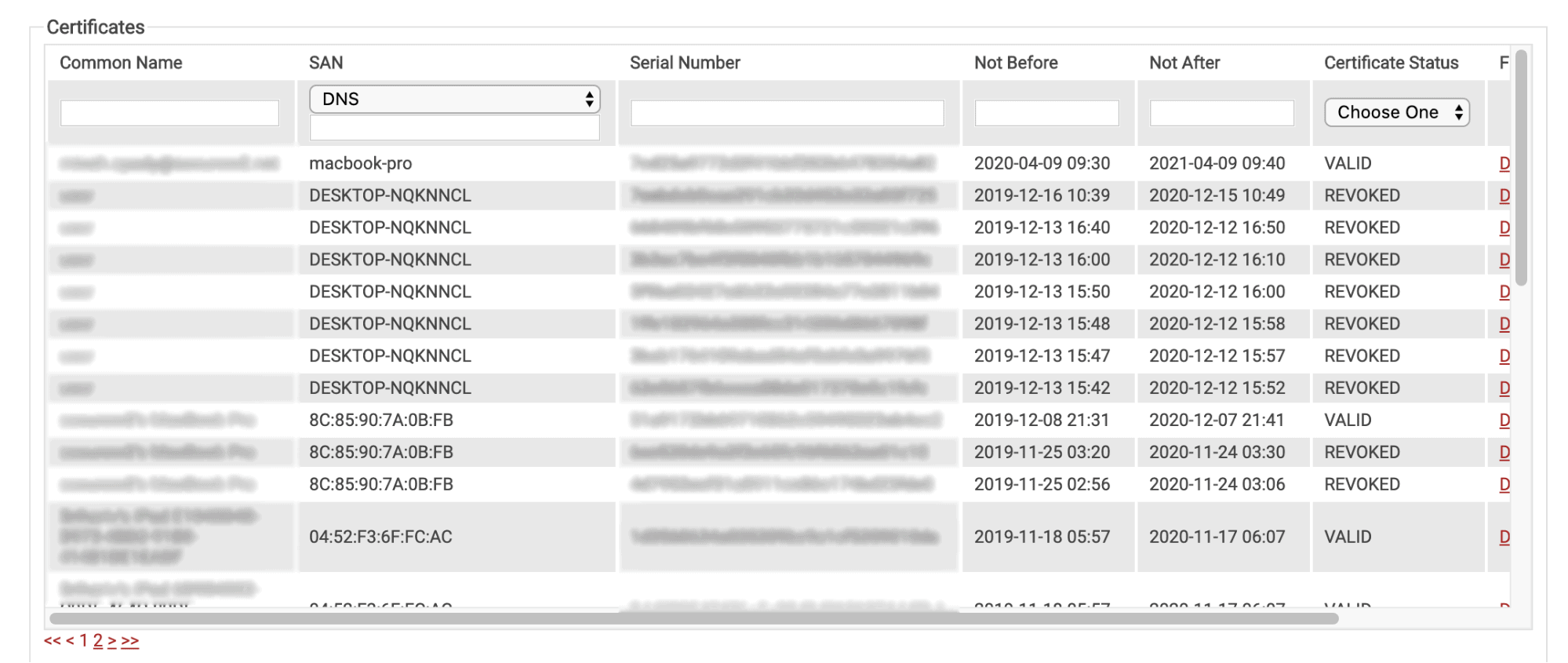
Each certificate you revoke will be added to a Certificate Revocation List (CRL) that was automatically generated with SecureW2. This gives you complete managerial control of your certificates.
SecureW2 also offers industry-exclusive Identity Lookup with LDAP & SAML Identity Providers, allowing our Dynamic Cloud RADIUS server to look up the identity of a user in real-time during the authentication process. You can create policies and issue custom templates based on user groups that have been established in your directory. This is a huge departure from the traditional RADIUS which simply confirmed the legitimacy of a certificate. Now it’s much easier to enforce group policy and user segmentation without having to go through the usual certificate management cycle.
The Most Reliable Certificate Deployment Available
The JoinNow solution from SecureW2 comes with a powerful certificate enrollment gateway enabling MDMs (Workspace One, JAMF, Intune, MobileIron, etc.) to push out configuration profiles that will allow devices to auto-enroll for certificates. In one fell swoop, all your managed devices will be set up for certificate-based authentication to Wi-Fi, Web Apps, VPN, and more.
If you’re working in a BYOD environment, SecureW2 offers a #1 rated onboarding client that enables easy WPA2-Enterprise self-configuration. JoinNow was built with the end-user experience in mind and is carefully crafted to make the onboarding process as easy and painless as possible. The simple, easy-to-follow prompts make getting configured and connected to secure wireless a snap.
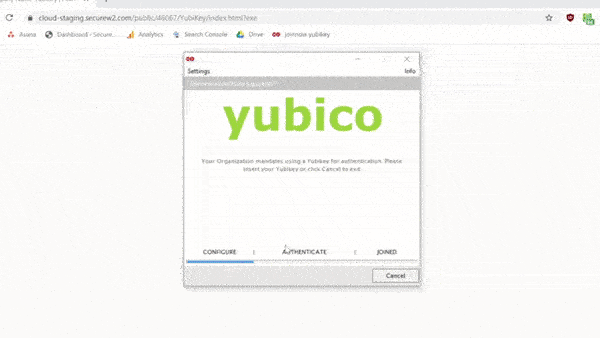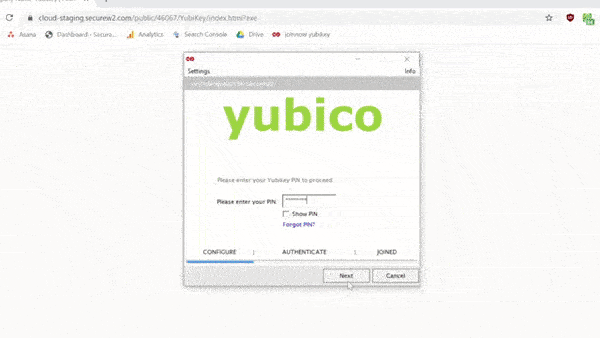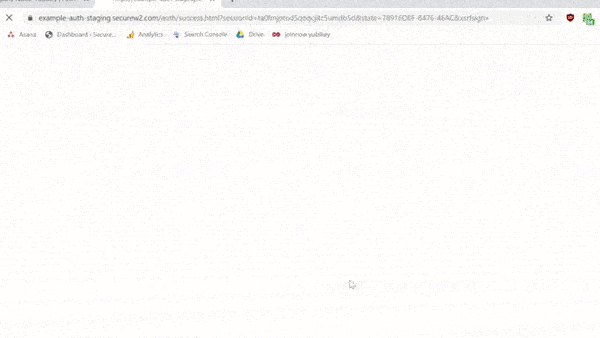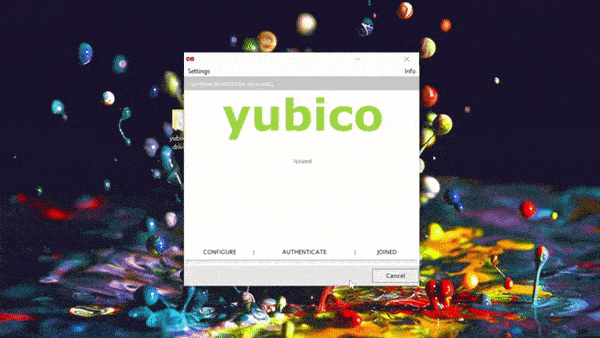
IT organizations that want to take advantage of PIV technology are also in luck with SecureW2. Configuring Yubikeys for certificates is simple with SecureW2. With just a few clicks in our world-class management portal, you can create a custom client that will configure your Yubikey for certificate enrollment.
Here’s a GIF of the process:
SecureW2 offers a complete package with everything you need to run a powerful PKI. This includes a private CA custom-tailored to your needs. Check out our PKI solutions page to see how we can help your organization stay safe and secure.