Key Points
- Incorrect formatting or encoding of the SAN and CN fields can cause SCEP requests to fail silently.
- SCEP deployment fails if the SCEP profile and the Trusted Root CA profile are not assigned to the same user or device groups.
- Delays are common as MDMs use staggered rollouts and load balancing to prevent network congestion, which can cause SCEP profile deployment to take a significant amount of time.
You’re not alone if you have ever hit “Push” on the Simple Certificate Enrollment Protocol (SCEP) profile in your Mobile Device Management (MDM) only to find that nothing immediately happens. It’s a frustrating experience, especially when everything seems correctly configured. Whether you’re using Intune, JAMF, or another MDM, certificate-based authentication using SCEP can feel tedious at times.
Let’s dive into why this happens and how to resolve it.
Understanding the Basics: MDM Profile and SCEP Profile
An MDM profile is a set of configuration files in a device management solution used within an organization to secure endpoints such as Wi-Fi settings, VPN connections, security parameters, application installation, and the deployment of digital certificates. It is one of the key components of an MDM solution, like Intune and Jamf, and is widely used across various operating systems.
A SCEP profile is a configuration used in MDMs that automates the certificate issuance process using the SCEP protocol from a Certificate Authority (CA). The SCEP profiles allow you to define the various certificate management properties for certificates before issuing them to the endpoint devices.
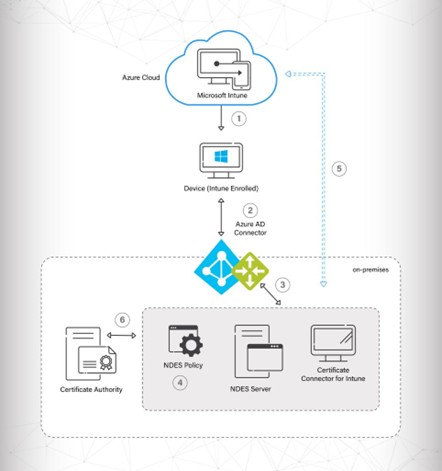
A MDM solution uses SCEP for its managed devices to push the payload with the SCEP URL and shared secret. The SCEP URL allows the devices to communicate with the Dynamic PKI using the Gateway PKI URL, and the shared secret is the case-sensitive password shared between the SCEP server and the CA.
Common SCEP Configuration Issues
Now, before diving deep into troubleshooting, let’s look at some common SCEP misconfigurations that users usually face while deploying SCEP certificates in Intune and JAMF.
1. Attribute Encoding
SCEP Profiles depend heavily on correctly encoded attributes such as Subject Name (CN), Subject Alternative Name (SAN), Key storage provider (KSP), and so on. If somehow these fields are misconfigured, the SCEP certificate request may silently fail. Make sure to cross-verify these variables and their formatting before coming to any conclusion.
2. Audit the Error Logs
Your MDM must provide error codes or detailed logs for any failed deployment. Let’s analyze these codes for Intune and Jamf:
a. Microsoft Intune
While using Intune and your management portal, you might encounter error messages such as “Device Creation Failed” and “SCEP enrollment failed”. You can resolve these issues by following these steps:
- Ensure the SCEP profile in the Intune Portal is configured to send values in the SAN attribute using Email address (RFC822). The common attributes configured are DeviceName and AAD_Device_ID.
- Confirm if the Policy Engine Workflow is mapped to the Intune API Token as an Identity Provider. Similarly, ensure the Enrollment Policy is mapped to the User Role and default Device Role.
- Verify whether the Trusted Root CA of the RADIUS server certificate is mapped to the Wi-Fi profile.
- Remove the SCEP profile and push any other profile, like the Trusted Root CA profile, to confirm if the user has successfully configured.
b. JAMF
JAMF has an option to enable debug logging, which could be handy for troubleshooting JAMF-related issues. However, JAMF recommends that it affect the performance of JAMF Pro.
To enable Debug Mode, navigate to Settings –> JAMF Pro Information -> Jamf Pro Server Logs -> Edit -> check the box for Enable Debug Mode.
You can disable this option once you’re done troubleshooting an issue.
3. Enable Troubleshooting Mode
In SCEP certificate deployment in Intune, the SCEP certificate profile and the trusted certificate profile must be assigned to a user or a device in the same order. The table below shows the outcome of a misassignment of the SCEP and the trusted certificate profiles.
| Trusted certificate profile assignment includes the User | Trusted certificate profile assignment includes User | Trusted certificate profile assignment includes Device | Trusted certificate profile assignment includes User and Device |
| SCEP certificate profile assignment includes the User | Success | Failure | Success |
| SCEP certificate profile assignment includes the Device | Failure | Success | Success |
| SCEP certificate profile assignment includes User and Device | Success | Success | Success |
To troubleshoot profile assignment issues, (Note: The troubleshooting employs the same method for Android and iOS. )
- On the Microsoft Intune Admin Center, go to Troubleshooting + Support > Troubleshoot.
- On the Troubleshoot option, set the Assignments to Configuration profiles and validate:
After that, the user should receive the SCEP profile. The user must review the user’s network group and ensure that the user intends to receive the SCEP profile. The user must also examine the last checked device with Intune.
The Hidden Culprit: Lag Time
Even after trying everything and troubleshooting in every way possible, you still might face delays in pushing the SCEP profile. This is mainly caused by the propagation delay in the MDMs due to their inherent nature. For example, in Microsoft Intune, SCEP certificate profiles can take several minutes or even longer to apply fully, especially when it is pushed through a large number of devices. Similarly, when pushing to multiple macOS devices in JAMF, the propagation can also vary depending on how the push settings are configured and the frequency at which devices sign in.
Similarly, when using Google Workspace or managed Google accounts, pushing an SCEP profile configuration to a large number of devices will not result in immediate deployment. Instead, Google intentionally follows a load-balancing mechanism and staggers the rollout to avoid network congestion and server overload. The more devices you configure, the more likely Google is to “spread out” deployments over time.
So be patient and do not panic if you notice devices roll out incrementally.
Streamline SCEP Profile with SecureW2
We have observed that troubleshooting some common misconfigurations in the SCEP profile can be easier than it might initially seem. You can start by validating certificate attributes, reviewing the MDM error codes, and double-checking the documentation. Most of the time, we find that just waiting a day or two can help, since MDMs, like Intune, can often take over 24 hours to push out profiles. But sometimes the issue cannot be fixed by yourself, and you need reliable onboarding support.
This is where SecureW2’s solutions make a difference. Our Dynamic PKI integrates seamlessly with leading MDMs like Intune and Jamf, simplifying the entire certificate lifecycle. It was built on thousands of deployments’ worth of best practices, so it can be set up securely in a day. Backed by our top-rated white-glove support, we resolve SCEP Profile issues in no time. If you are having issues with your SCEP setup, let us know, and we’d be happy to give you a demo of SecureW2.