Key Points
- PKI delivers cryptographic assurance of identity, enabling secure certificate-based authentication across users, devices, and applications.
- Identity-based attacks bypass weak credentials, exposing organizations attempting Zero Trust without PKI.
- Deploying PKI ensures continuous authentication and strong identity assurance for a true Zero Trust framework.
The IT industry is evolving rapidly, with new technologies, devices, and systems introduced regularly. Organizations are regularly having to update and upgrade their environments regularly to keep up with the modern IT landscape. Organizations today are tasked with managing and authorizing hundreds of thousands of devices, machines, systems, and applications.
Managing an enormous amount of entities means organizations need to prioritize network security as hundreds of thousands of devices means hundreds of thousands of opportunities for exploiting vulnerabilities. A report shows that 85% of organizations say network security is harder to manage network security than it was two years ago.
The recommended security practice is following the Zero Trust philosophy. In its simplest form, Zero Trust means not trusting anything. Along with the outer network perimeter, Zero Trust includes putting up barriers on around every internal network resource. This article delves more into Zero Trust and how organizations can implement it quite easily with a Public Key Infrastructure (PKI).
SecureW2’s turnkey Cloud PKI and RADIUS services are perfect for Zero Trust as network admins can accurately identify all their users and devices, manage who has access to which resources, and easily segment their network. Read about how easy it was for our customers to configure SecureW2 PKI.
What is Zero Trust?
The Zero Trust approach is a network security practice that treats all users, devices, and systems as inherently untrustworthy and one-time validation is not good enough. Organizations must constantly validate that a user or device has the appropriate access levels and permissions. The Zero Trust method challenges the idea that establishing a network perimeter with a firewall is secure enough. Is it safe to assume everything inside your network can be trusted?
The introduction of cloud computing created a need for solutions like Zero Trust because network infrastructures are shifting away from legacy on-premise systems with a giant firewall perimeter. Cloud technologies have made it easy for users to access resources from anywhere, so systems need to be isolated with micro-perimeters, sectioning off smaller sections of alike entities instead of relying on one network-wide perimeter. This way, applications and assets are kept from public view and isolated from the rest of the network.
Firewalls are still viable sources of security, but Zero Trust just adds that there needs to be more and concentrated perimeters that allows access to as few users as possible. Nowadays, simply residing on the network no longer ensures that an entity can be trusted. However, managing thousands of micro-perimeters and segmenting tens of thousands of users, devices, workstations, VMs, systems, and applications into those micro-parameters can heavily burden IT admins. Luckily, there are several micro-segmentation and automation tools to use.
Identity and Automation are Key for Zero Trust
With the Zero Trust approach, identity serves as the perimeter. This means that instead of basing identification on the IP address, like the traditional approach, it’s based on verifying the end user’s identity with secure mechanisms like IAM, Multi-Factor Authentication (MFA), Biometrics, and Public Key Cryptography. This authentication process must be dynamic and verify the user’s identity on a regular basis to maintain the Zero Trust model.
Automation is also key for the Zero Trust model because applications are constantly being updated and users are constantly being onboarded, offloaded, and laterally moved. To keep up with this rapid change, access controls need to be automatically provisioned and user and group policies need to be applied.
With automated software, networks can easily implement Zero Trust through Micro-segmentation, dynamically segmenting applications, systems, and devices in protected groups based on customized access levels.
Using Certificates and TLS Encryption for Zero Trust
Identity is central to the Zero Trust approach, making TLS encryption vital for complete Zero Trust implementation. TLS leverages digital certificates, using them to identity servers and clients. Certificates are made up of two mathematically-linked cryptographic keys, which are exchanged among server and the client during the authentication process, establishing trusted identities.
Certificates are commonly used for secure device authentication, but can be issued to all kinds of network entities, including network devices, web servers, applications, VMs, workstations and more. Admins can configure a Certificate Authority (CA) which digitally signs certificates, verifying their legitimacy. With Digital Certificates and Private Key Attestation, networks can link identities with IP addresses with relatively high assurance.
MFA and Single-Sign-On (SSO) are commonly used tools to implement zero trust because they can easily and accurately verify end users without too much burden on their part. However, the recent SolarWinds attack proved that MFA can be bypassed, so organizations need to use certificates as one of the authentication factors. Certificates strengthen the verification of digital identities because they are locked onto devices and encrypted.
Configure a PKI to Implement Zero Trust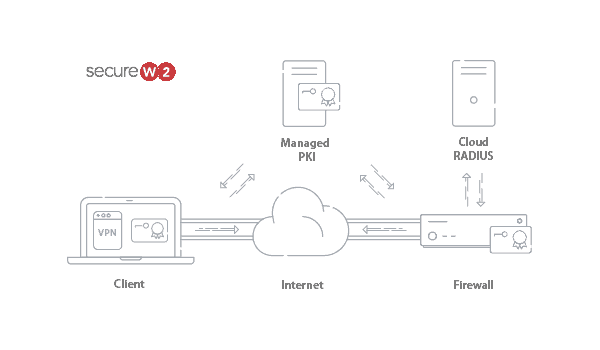
Configuring a private PKI is critical for implementing Zero Trust because it allows organizations to establish trusted machine identity, encrypt communications across the network, and is required for certificates.
However, certificates have lifespans and require constant management; it can be challenging to keep up with the life cycles of hundreds of thousands of certificates. Luckily, there are managed PKI solutions that take away the heavy workload from the admins, like SecureW2’s Cloud PKI.
SecureW2’s PKI is a turnkey PKI solution built with certificate-based EAP-TLS authentication which eliminates over-the-air credential theft, something that plagues credential-based authentication protocols like EAP-TTLS/PAP or PEAP-MSCHAPv2. With SecureW2, admins can customize, issue, enroll, revoke, and manage all issued certificates from an easy-to-use GUI.
Our PKI solution also includes CloudRADIUS, SecureW2’s dynamic RADIUS solution in the cloud. CloudRADIUS is powered by a Dynamic Policy Engine that allows RADIUS to directly reference a user’s entry in the network directory (Google, Okta, Azure) and determine access levels based on policies attributed to that user. Even further, the RADIUS can perform runtime-level policy decisions and changes made to a user’s permissions will reflect on the network immediately.
Enabling Zero Trust with a Managed Cloud PKI
SecureW2’s PKI and CloudRADIUS are integral to a Zero Trust framework because our technology leverages digital certificates for secure network authentication. Admins can configure certificates to authenticate users for Wi-Fi, VPN, web applications, and much more. Our software can be set up in a matter of hours, doesn’t require any forklift upgrades, and comes at an affordable price.