As cyber security risks increase and secure access to network resources is required, organizations are adopting different authentication methods. RADIUS certificate-based authentication is one of those methods that increase the security level of the RADIUS protocol. 80% of breaches in 2020 involved lost or stolen credentials or brute force.
Using RADIUS is an effective way to improve network security and visibility, especially considering that every organization has two RADIUS options to choose from: On-Premises RADIUS or Cloud RADIUS. This organization decided to use SecureW2’s Cloud RADIUS because they wanted to get rid of all their on-premise servers.
In this article, we will cover RADIUS certificate-based authentication and explain how it works.
Overview of Certificate-Based Authentication
Vulnerable data protection is crucial in today’s digital world. Because they are so simple to guess or steal, passwords are no longer thought to be a safe method of authentication. This is where authentication via certificates is useful.
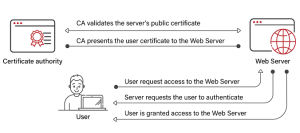
Certificate-based authentication makes use of digital certificates. A “digital certificate” is a digital file that comprises information about the true identity of an entity and the public key connected to that entity. The Certificate Authority (CA), an acknowledged third party, signs the certificate.
What Is the RADIUS Protocol, and How Does it Work?
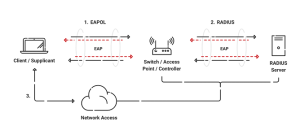
Remote access to network resources is accomplished through the Remote Authentication Dial-In User Service (RADIUS) protocol. It enables centralized authentication, authorization, and accounting (AAA) management for people or connected devices.
The RADIUS protocol has a client-server architecture, where the server is located centrally and the client usually appears on the access device, such as a router or switch. A user’s credentials are sent to the RADIUS server by the access device whenever a device or user attempts to get connected to the network. After confirming the user’s credentials, the RADIUS server communicates to the access device by approving or rejecting connection to network resources.
RADIUS’ centralized control makes it simpler for network administrators to monitor and secure network access. Because authentication is centralized, network administrators may quickly add and remove users from the network, change user rights, and manage network resource access. RADIUS also has an administration and accounting system that enables network managers to monitor consumption and activities.
The RADIUS protocol, when used in combination with certificate-based authentication, improves network security. RADIUS certificate-based authorization ensures that only authorized parties may access network resources by utilizing digital certificates to authenticate the identify of users or devices.
RADIUS Certificate-Based Authentication
RADIUS certificate-based authentication is a method for employing digital certificates to confirm the identification of users or devices connecting to a network through RADIUS. The authentication procedure is made more secure by the use of digital certificates to demonstrate the identity of people or devices.
Digital certificates provide information about the entity’s verification, such as the user’s name or the kind of device. Only the RADIUS server employing the public key of the CA may decrypt this data because it is encrypted. The RADIUS server may be certain that an individual or device connected to the network is authorised if their certificate is valid.
Since it verifies the true identity of an entity joined the network, the digital certificate is crucial to certificate-based authentication. A user and device provides the RADIUS server with its digital certificate upon joining the network. The certificate is then verified by the RADIUS server employing the public key of the CA. The RADIUS server gives connection to network resources if the certificate is legitimate.
For certificate-based authentication, it’s is necessary to use a reputable third-party organization, like a Certificate Authority. The digital certificates must be issued and their legitimacy must be verified by the CA. The CA only issues the certificate after it is confident in the entity’s identification that is making the request for it. Furthermore, to help stop unauthorized network access, the CA also maintains a record of certificates that were lately revoked.
Drawbacks of On-Premise RADIUS Servers
On-premise RADIUS servers, although being a common option for network verification, have an array of problems that could jeopardise the safety and efficacy of the method of authentication. In this part, we’ll go over a few of the key drawbacks of an on-premise RADIUS server.
⦁ Cost and Maintenance
⦁ Scalability and Flexibility
⦁ Security Concerns
Cost and Maintenance
Installing and maintaining an on-premises RADIUS server can be costly and time-consuming. Network administrators must invest in equipment, software licences, and regular upkeep to maintain the server running well. The demand for space, power, and cooling for on-premise servers can increase the overall cost of ownership.
Scalability and Flexibility
On-premise RADIUS servers’ versatility and scalability may be limited. To support more people or gadgets on the network, more hardware and software adjustments may be required, that can be laborious and challenging to administer. In order to grow up the server to cope with larger networks, fresh equipment may need to be purchased or current hardware may need to be upgraded.
Security Concerns
RADIUS servers installed on-site could also be a safety issue. To stay updated with the security threats and flaws, they must be continually updated and managed. In addition, physical safety concerns like loss or destruction could be present on on-premise servers, compromising the safety of the authentication procedure.
One might be questioning how to get rid of or reduce the potential risks connected with on-premise RADIUS servers now that we’ve discussed their downsides. We’ll examine the numerous long-term advantages of moving RADIUS servers to the cloud in the section after this.
Advantages of Cloud RADIUS
In comparison to RADIUS servers installed on-premise, cloud-based RADIUS servers, like SecureW2’s Cloud RADIUS, are more effective and safe. In this part, we’ll go over few of the primary advantages associated with employing Cloud RADIUS.
⦁ Cost-effective and easy to maintain
⦁ Scalable and flexible
⦁ Enhanced security
Cost-Effective and Easy to Maintain
There is no longer a requirement for on-premise devices and software thanks to the affordable, simple-to-manage alternative known as cloud RADIUS. Administrators of networks can concentrate on other tasks because the Cloud RADIUS provider handles all hardware and software upkeep and upgrades.
Scalable and Flexible
Cloud RADIUS also provides enhanced capacity and adaptability. Additional devices or users can be added to the network quickly and easily, and the capacity of the server can be easily increased to support bigger networks.
In addition, Cloud RADIUS provides more adaptability in terms of authentication methods and techniques, allowing organizations to utilize extra authentication protocols and techniques, like certificate-based authentication.
Enhanced Security
Additional safety features are available with cloud RADIUS as well. Advanced security methods, such as multi-factor authentication and the use of encryption, are used by cloud RADIUS carriers to protect the authentication process.
Additionally, it is common practice to keep cloud RADIUS servers in highly secure data centers that provide both physical safety and defense against damage and loss.
The Role of CBA in Ensuring the Security of Your Organization
Certificate-based authentication (CBA) offers a variety of security advantages over conventional password-based authentication methods. This section will discuss how CBA reduces certain disadvantages of password-based authentication while also enhancing authentication reliability.
Stronger Authentication
Digital certificates are much more safe than traditional passwords when used in CBA. Digital certificates are keys with cryptography that are produced and verified by trustworthy independent Certificate Authorities (CAs). Since they are uniquely associated with the person or device and are consequently difficult to copy or fabricate, they provide an additional level of authentication over passwords.
Password Elimination
By removing the need for users to keep track of complicated passwords, CBA also reduces the danger of breaches of security associated to passwords. Passwords are typically the most vulnerable point in the authentication process since they can be so easily cracked, taken away, or assumed. CBA simplifies the authentication procedure and gets away with the need for users to keep track of passwords, which makes it simpler for people and safer for businesses.
Reduced Risk of Credential Stuffing
Using usernames and passwords stolen from one website to gain unauthorized access to another website is known as credential stuffing. The prevalence of this type of assault is rising as more and more people reuse their passwords on several websites. CBA reduces the danger of credential stuffing and makes it far more difficult for attackers to access the network by employing unique digital certificates for each user or device.
Cloud RADIUS: The Key to Secure and Flexible Certificate-Based Authentication
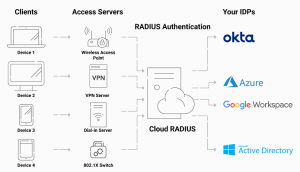
The Cloud RADIUS server from SecureW2 provides organizations wanting to use certificate-based authentication with a number of advantages. The Cloud RADIUS server from SecureW2 provides organizations wanting to use certificate-based authentication with a number of advantages. In addition to providing a safe and scalable solution, our Cloud RADIUS server enables organizations to verify certificates and authenticate user, group, and device data in any Identity Provider (IDP) at the moment of authentication. This indicates that organizations don’t need additional infrastructure or management burden to authenticate individuals and devices using their current identity management solutions.
Our cloud-based RADIUS server enables organizations to benefit from real-time access control and policy enforcement. Organizations can use the server to build access limits based on user, group, or device data, and the server will automatically enforce those limitations during authentication. This makes it possible for businesses to lower the danger of unauthorized access while still adhering to security guidelines and rules.
Contact us today to learn more about how our Cloud RADIUS can improve your organization’s network security.