1. Introduction
JoinNow’s Lookup Provider feature offers dynamic validation of user and device accounts during certificate issuance and WiFi connection. Seamlessly integrating with Google Identity Providers, this feature enables account checks to inform critical decisions and apply dynamic policies for network configuration on devices.
This new solution replaces the previous integration model, where Google Lookup Provider required regular maintenance and attention for account authorization, creating an administrative burden. SecureW2 has improved the solution to eliminate this manual dependency, migrating to a one-time configuration process. This enhancement ensures a more reliable and sustainable integration, reducing administrative effort and improving overall system resilience.
2. Prerequisites
- An active subscription to Google Admin Console with Admin privileges.
- Access to create a Google Service Account
- An active subscription to JoinNow Management Portal and JoinNow Cloud Connector.
3. Configuring Google IAM & Admin Portal
The following are the high-level steps required to configure Google IAM & Admin console for dynamic lookup with JoinNow:
3.1 Creating a New Project
The Google Service Account must be created in the IAM & Admin console. Log into the Google IAM & Admin console with the link here.
To create a new project in Google service account:
- Log in to Google Service Account.
- Click the Project drop-down at the top of the page.
- Click NEW PROJECT.
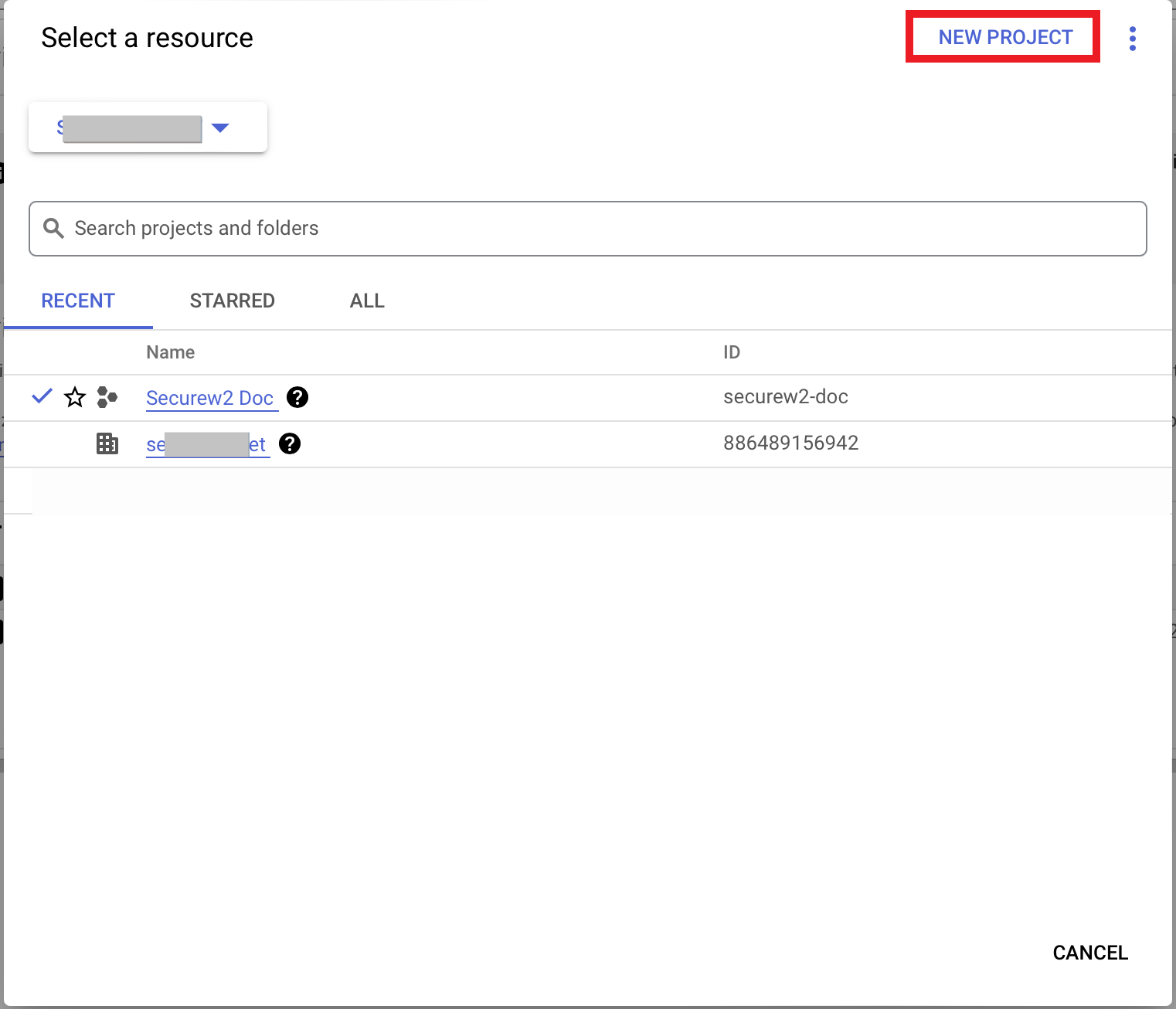
- In the New Project page, enter a name for the project in the Project name field.
- From the Organization drop-down, select the required organization for the project.
- From the Location drop-down, select the parent organization.
- Click Create.
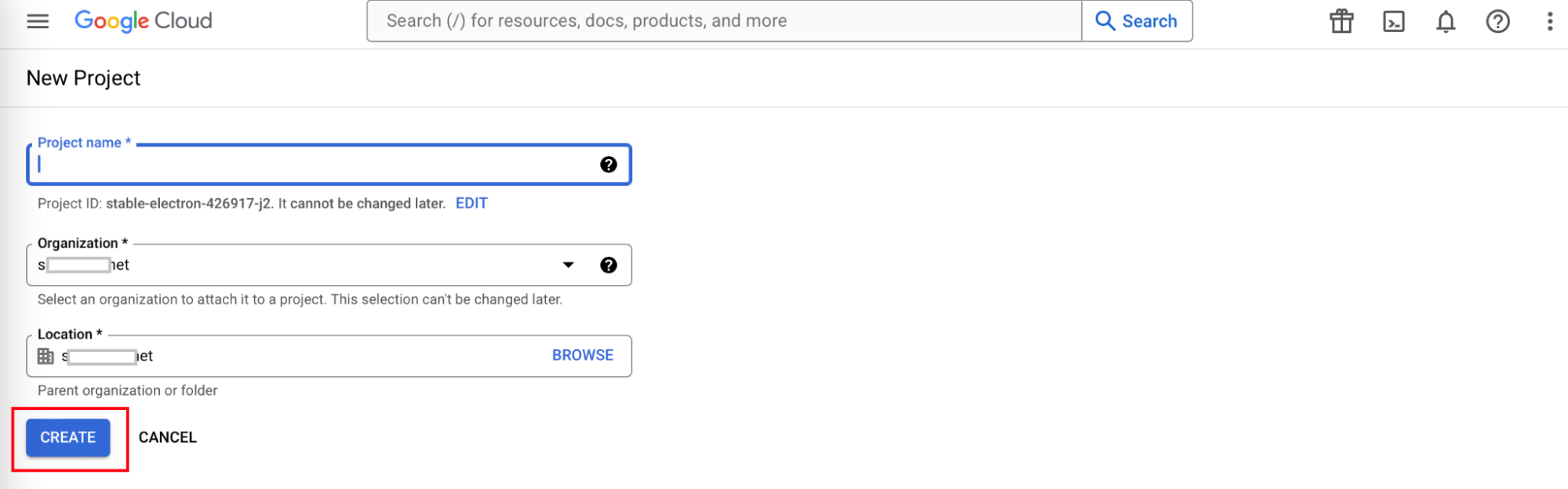
3.2 Enabling Admin SDK API Privileges
The Google Admin SDK API must be enabled to view and manage users, groups and devices present in the organization’s project.
To enable Admin SDK API:
- From the Projects menu, select the project created in the previous section: 3.1 Creating a New Project.
- From the side menu, navigate to API & Services > Enabled API & Services.
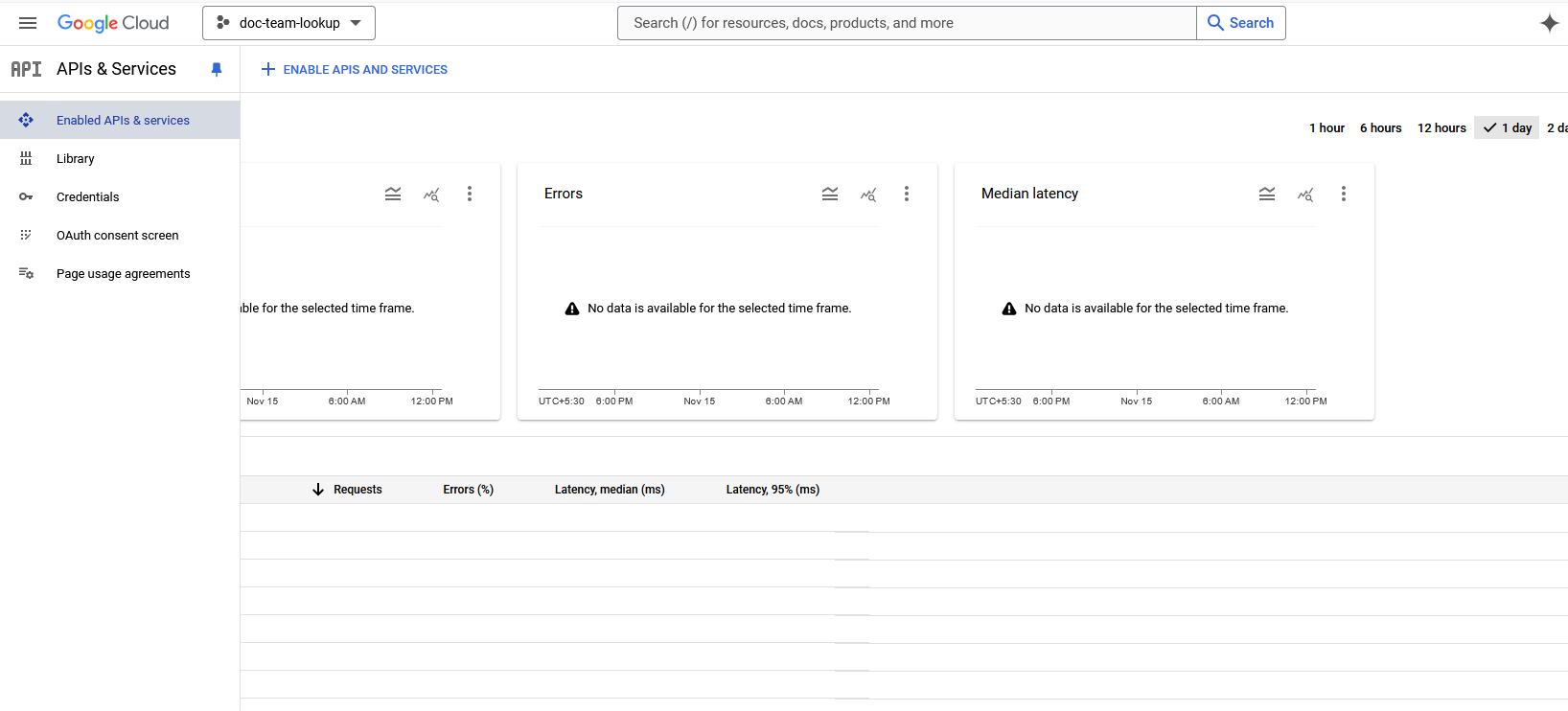
- In the API Library page, in the search box, enter Admin SDK API.
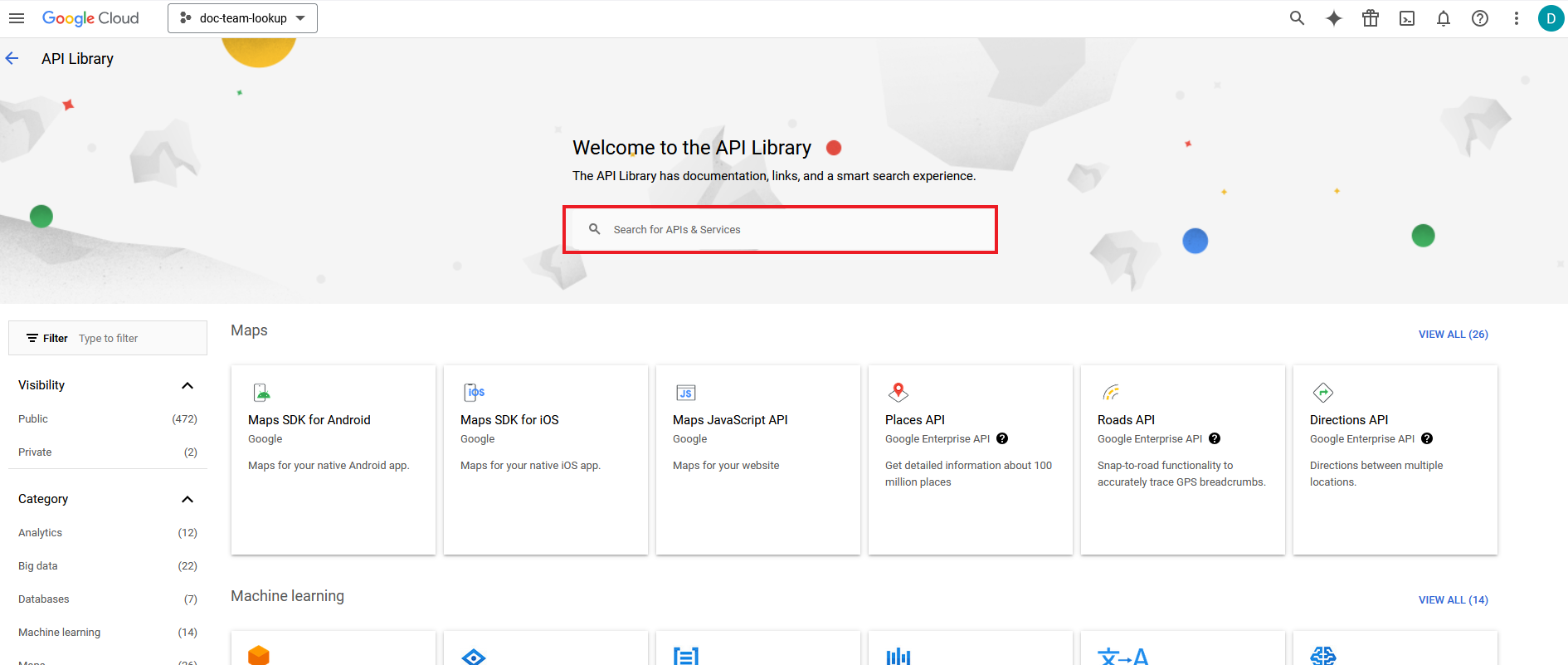
- Click on Admin SDK API.
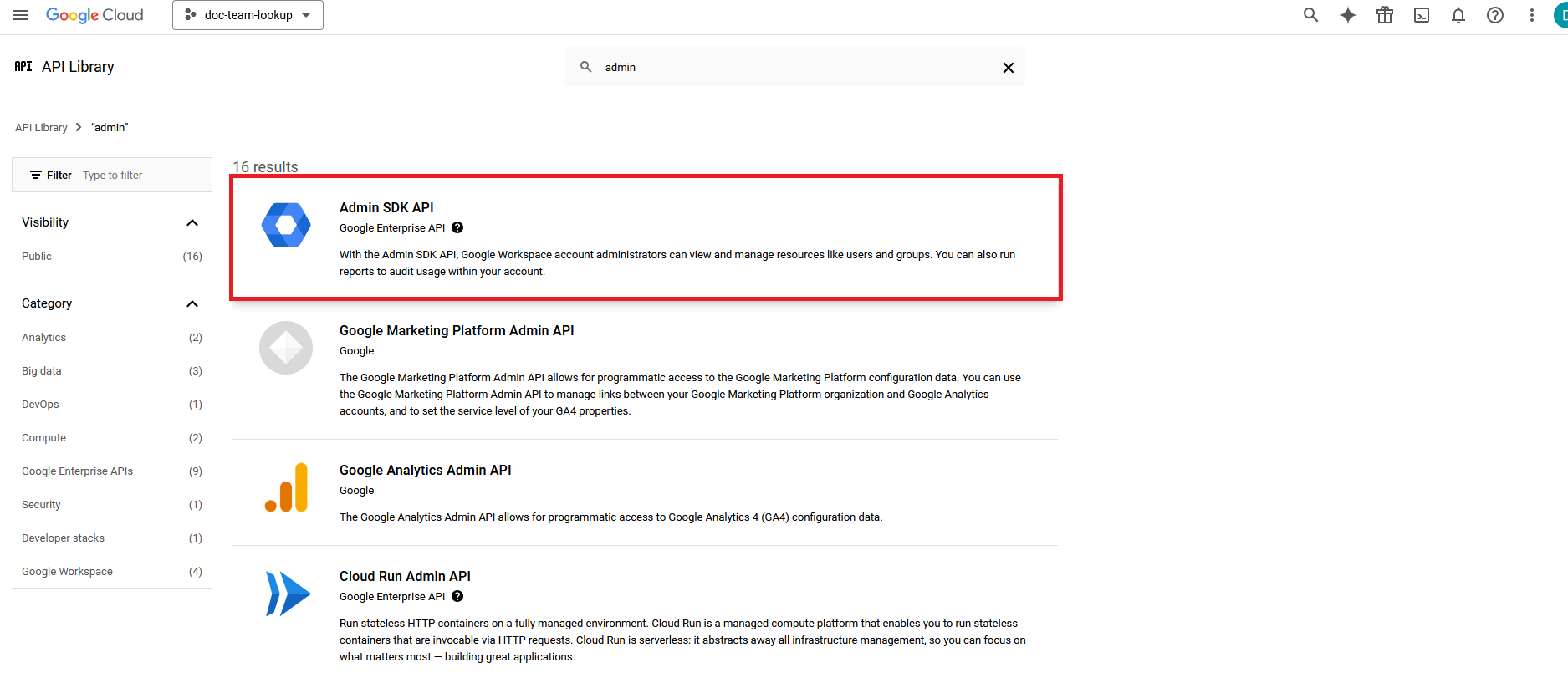
- Click Enable.
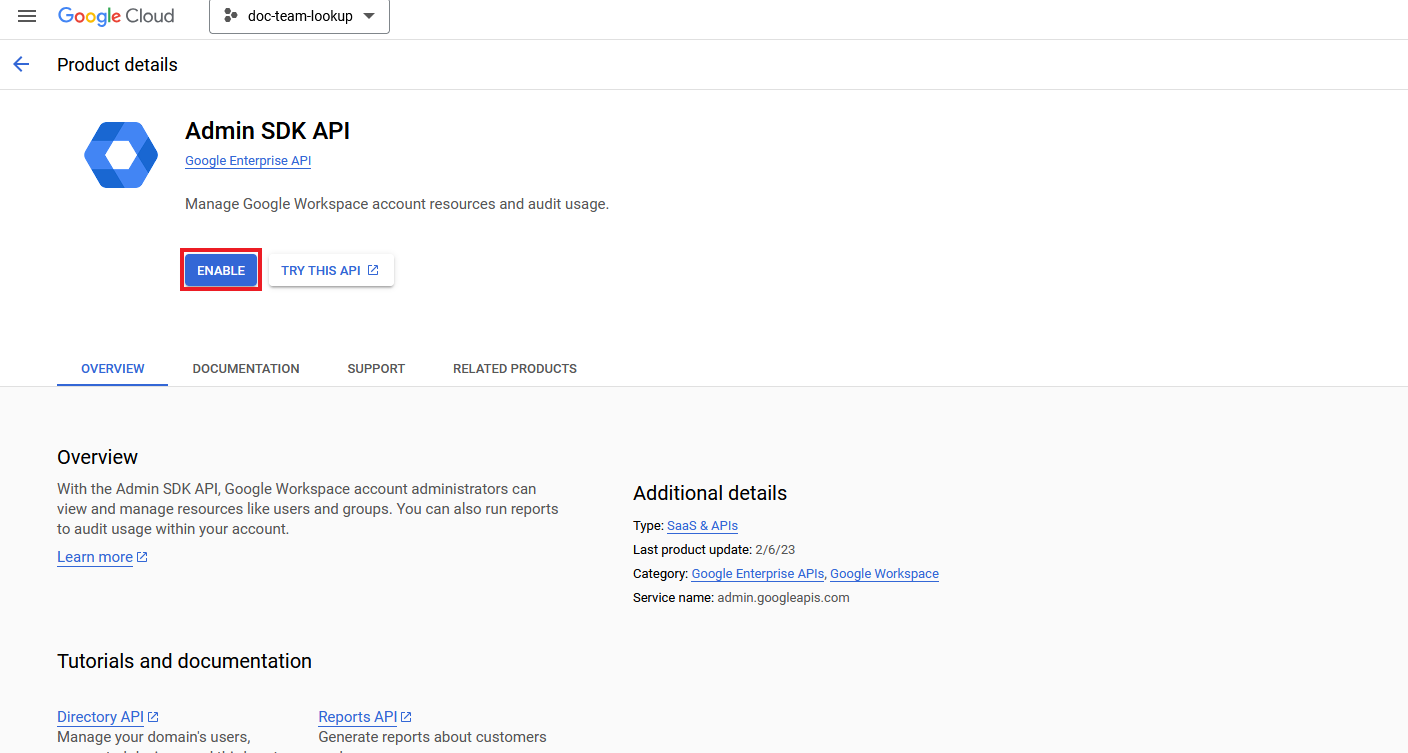
3.3 Creating A Service Account and a JSON Key File
JoinNow needs a Google Service Account to authorize communication with Google to do a lookup operation on behalf of the service account. To create a Service Account in Google:
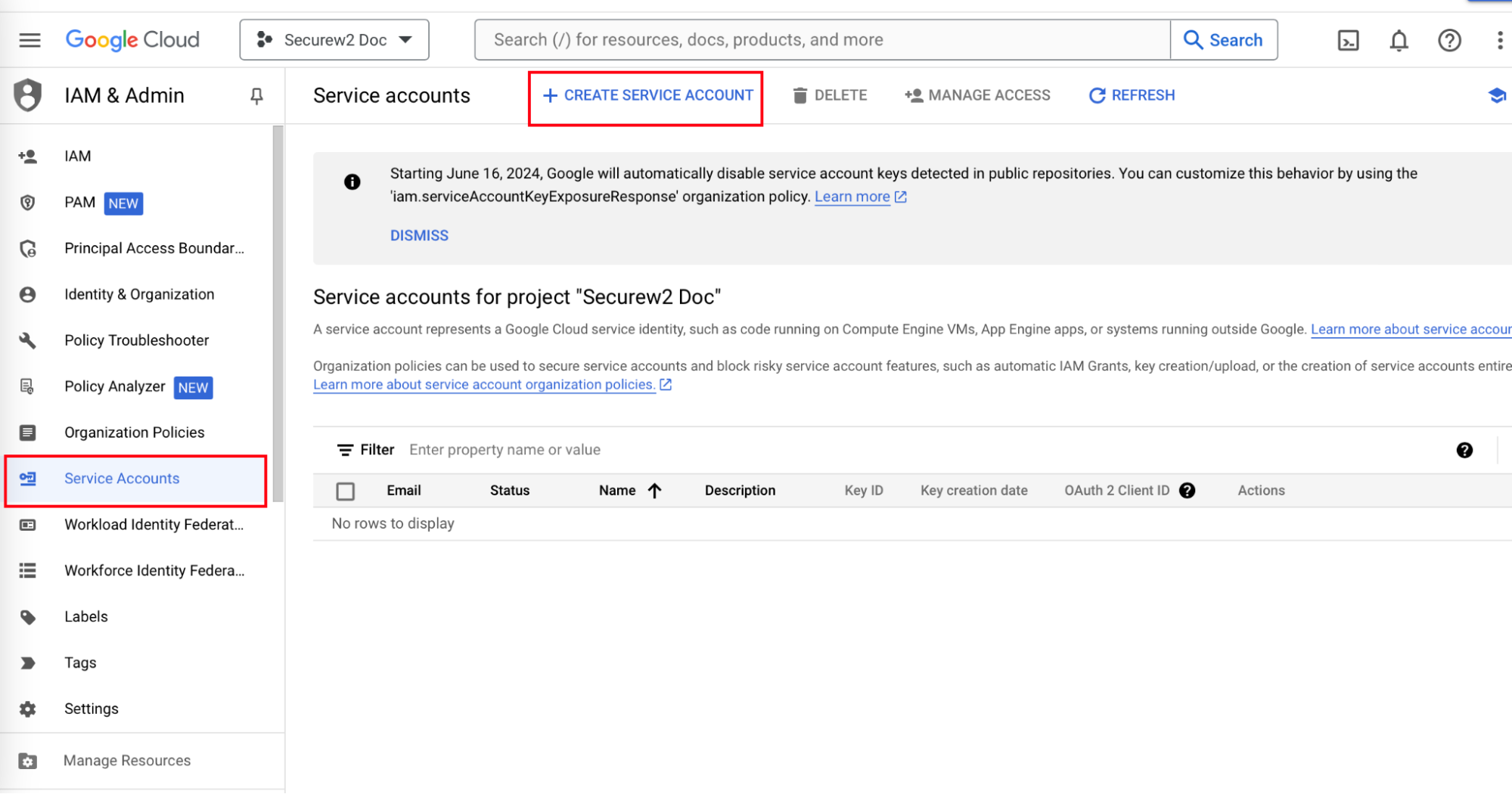
- Navigate to the IAM & Admin menu.
- From the left menu pane, click Service Accounts.
- Click + CREATE SERVICE ACCOUNT.
- In the Service account name field, enter a name for your service account.
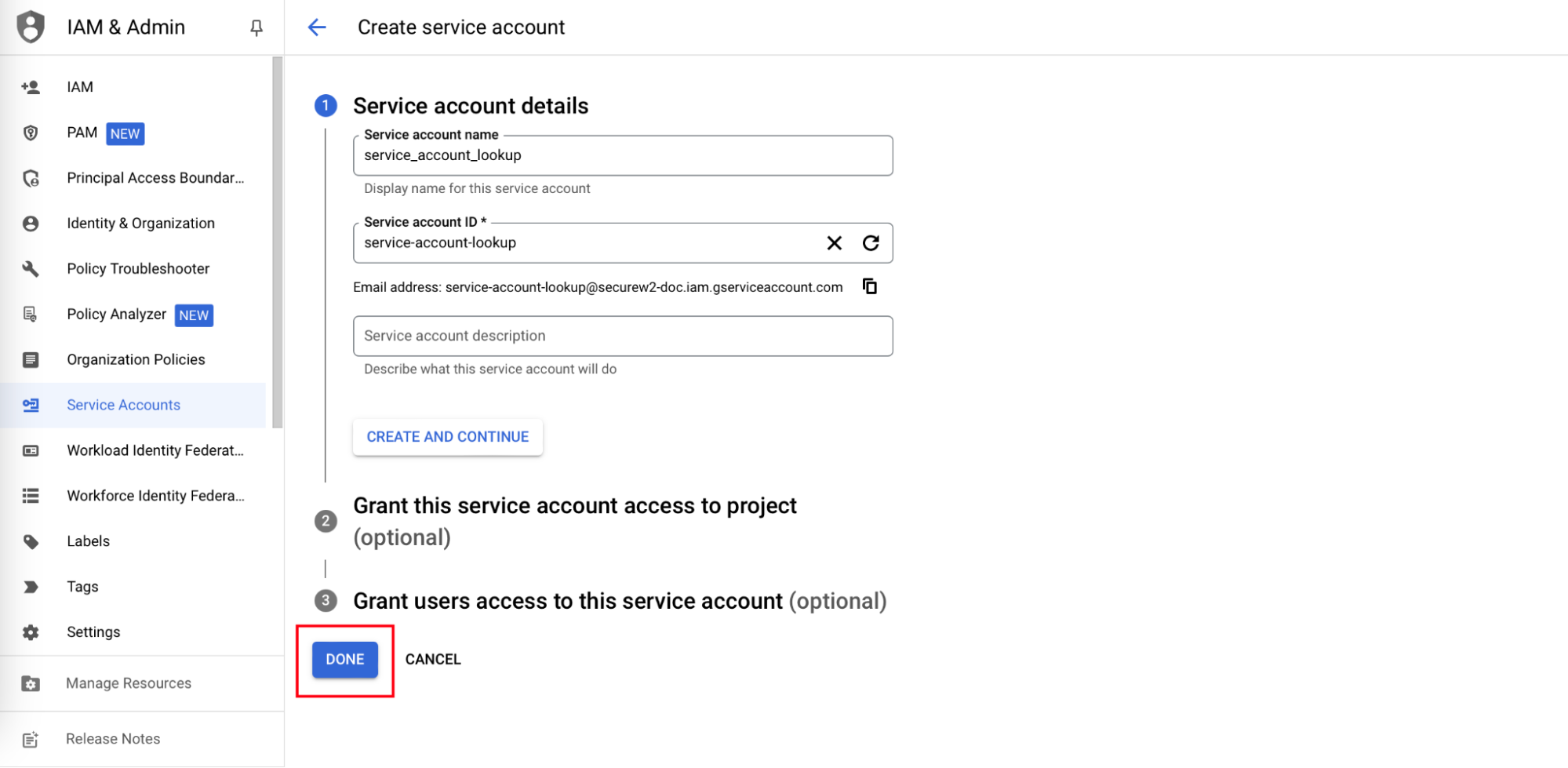
- In the Service account ID field, enter an ID for the service account.
- Click CREATE AND CONTINUE.
- Click DONE. The required service account will be created. Click on the service account link.
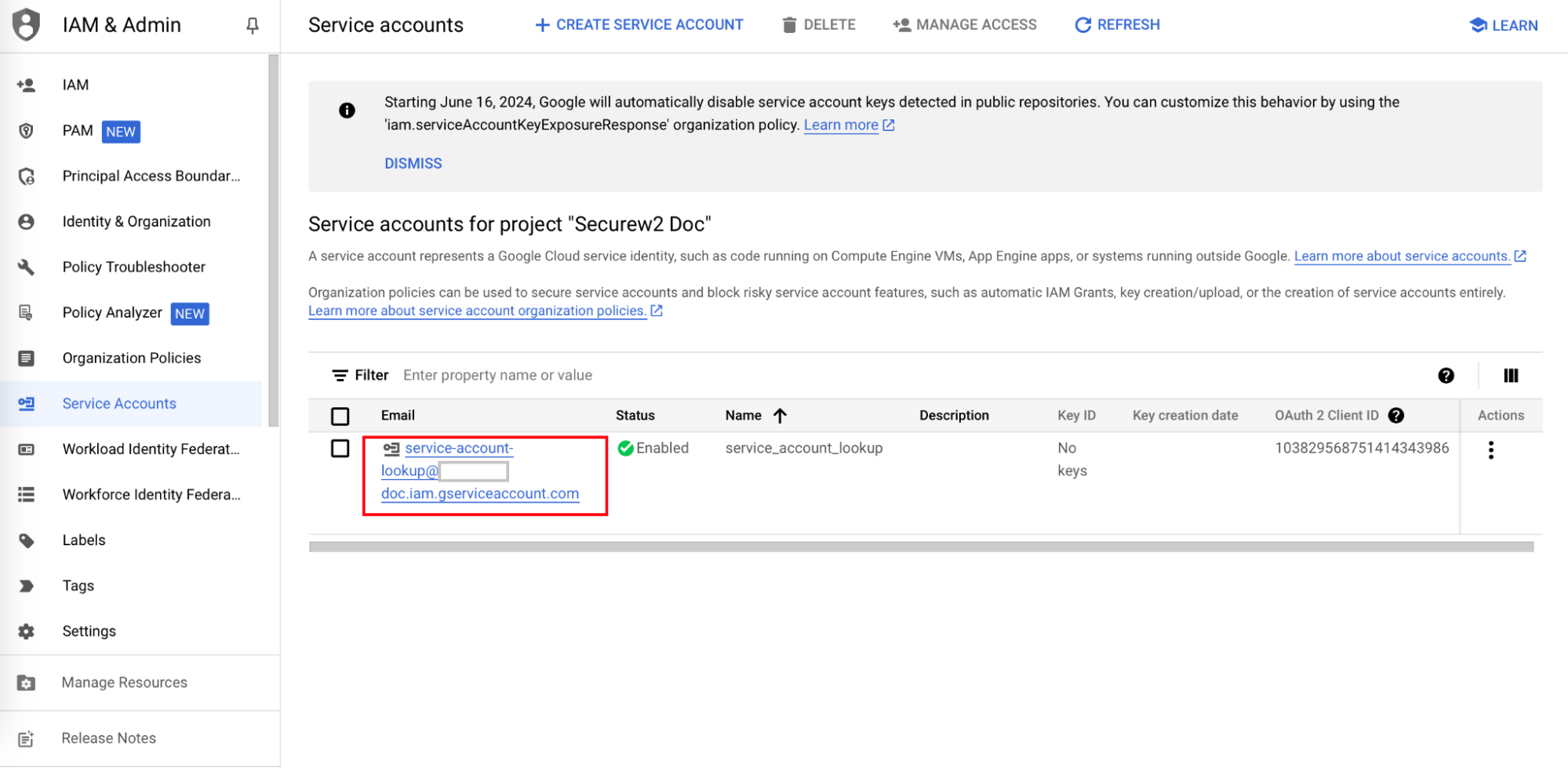
- In the service account page, click on the KEYS tab.
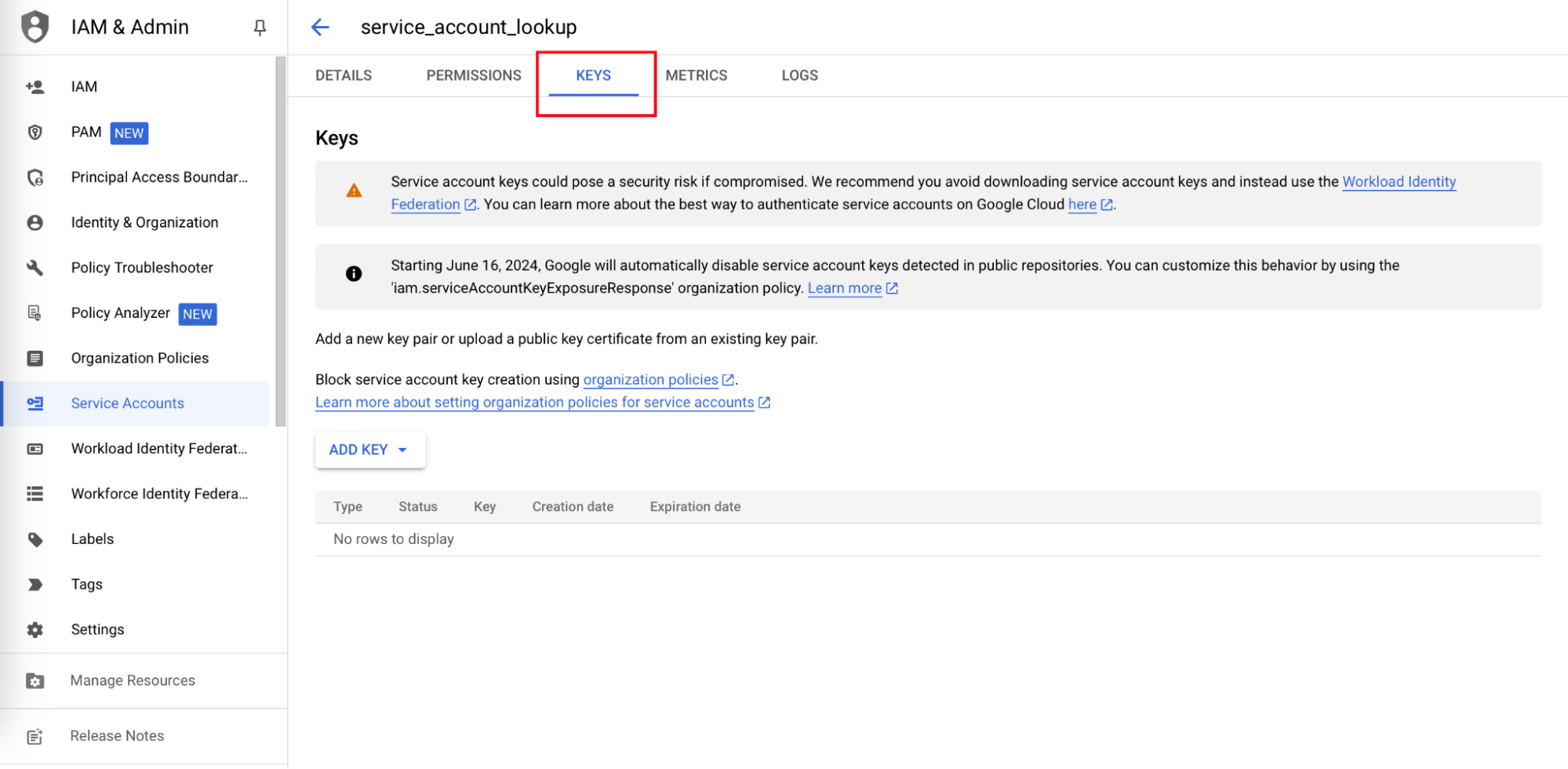
- From the ADD KEY drop-down, select Create new Key.
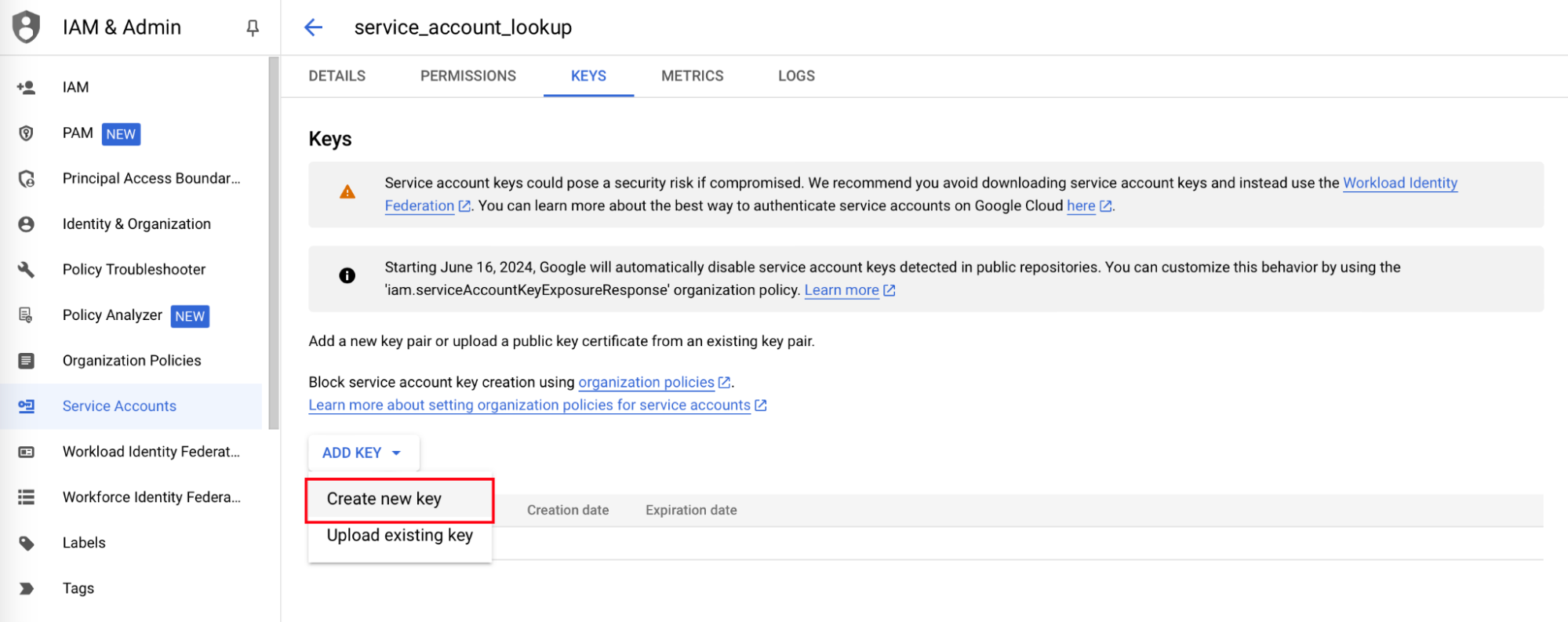
- In the Create private key pop-up, select Key type as JSON.
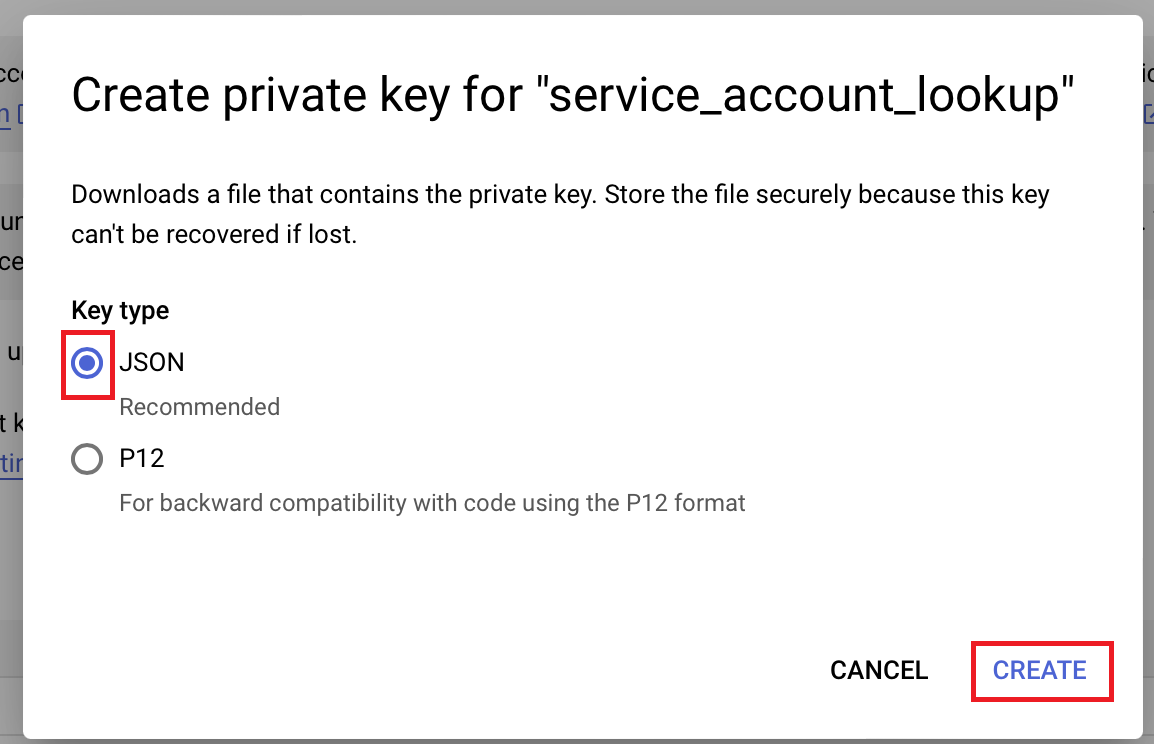
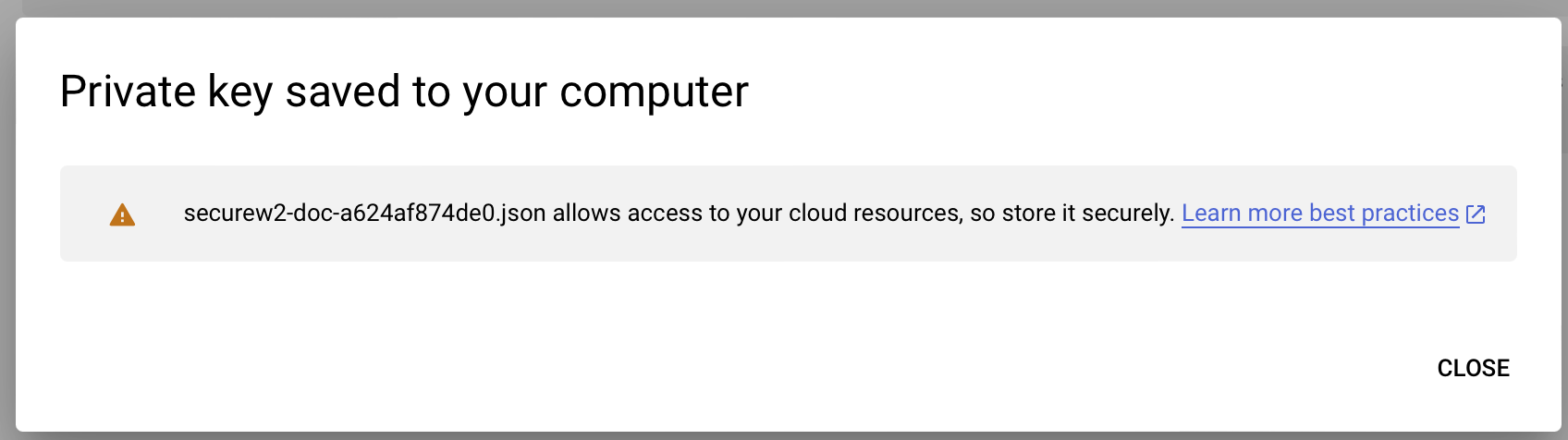
- Click CREATE. The JSON file will be downloaded to the device. Click CLOSE.
4. Configuring Google Admin Console
The following are the high-level steps to be configured in the Google Admin Console:
4.1 Delegating Domain Wide Authority to Service Account from Google Admin Console
Delegating domain wide authority helps administrators of the organization to authorize the service account to access user data required for lookup. Admins can delegate access to a service account from their Google Admin console.
To delegate domain wide authority:
- Log in to the Google admin console
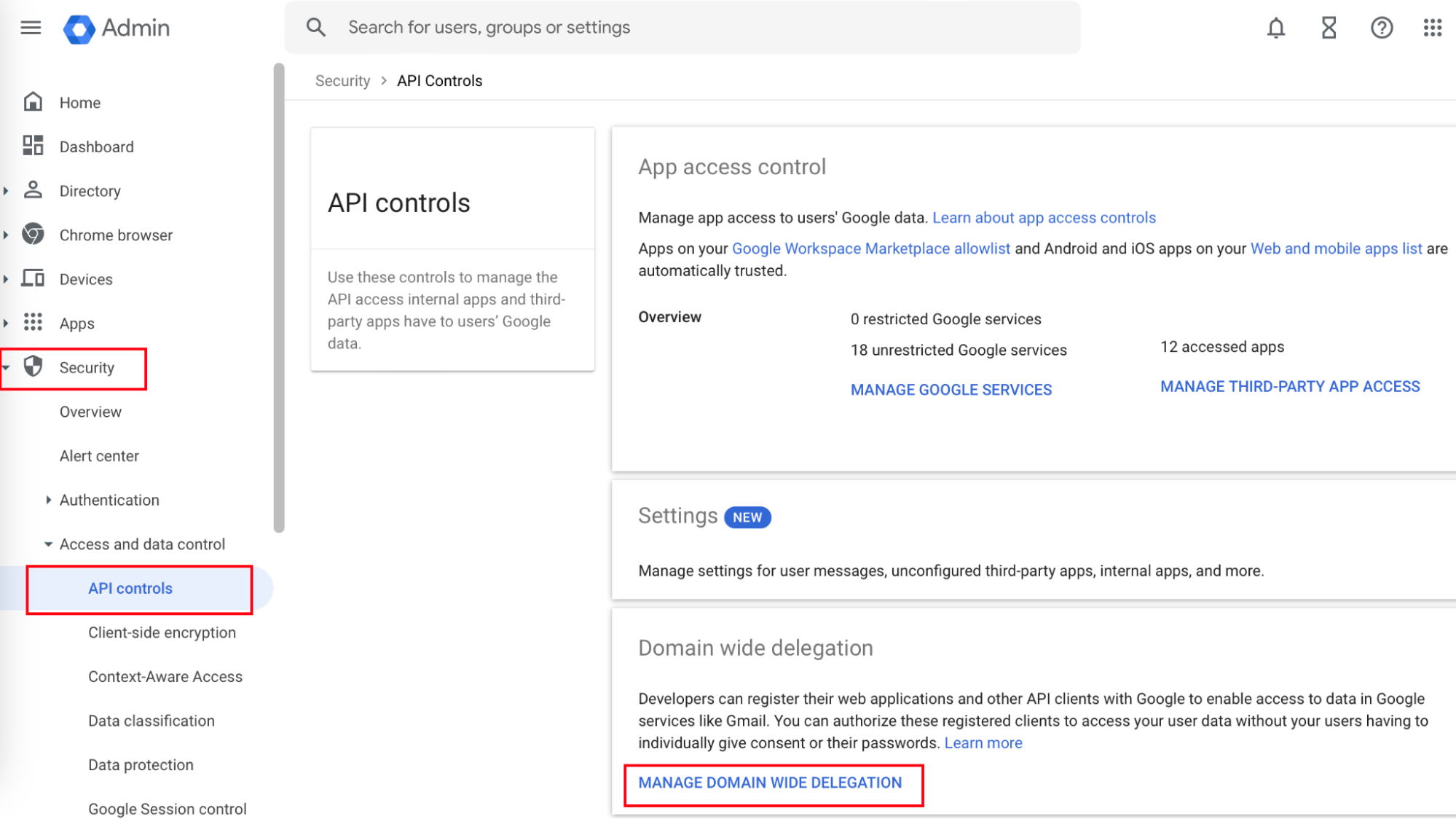
- Navigate to Security > Access and data controls > API controls.
- In the Domain wide delegation section, click MANAGE DOMAIN WIDE DELEGATION.
- Click Add new. A pop-up to add client ID will appear.
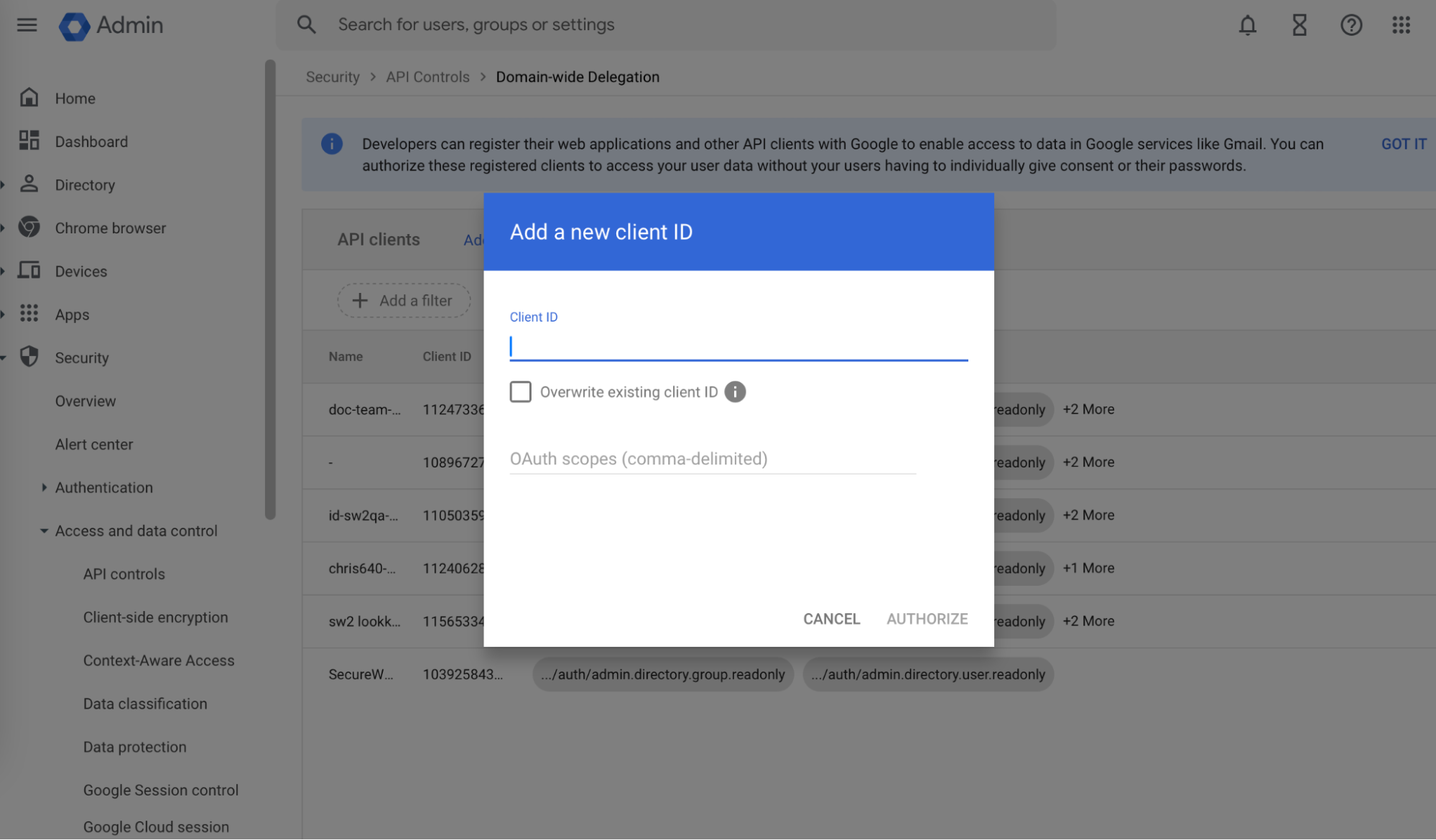
- Navigate back to your Google Service Account. Go to the Service Accounts tab and click on the service account created in Creating A Service Account and a JSON Key File section. Copy the Unique ID displayed in the Details tab. Paste the value in the Client ID field.
- In the OAuth scopes field, enter
“https://www.googleapis.com/auth/admin.directory.user.readonly,https://www.googleapis.com/auth/admin.directory.group.readonly,https://www.googleapis.com/auth/admin.directory.device.chromeos.readonly,openid”. - Click Authorize.
4.2 Creating a User in Google Admin Console
Google mandates the creation of a user for the access of information from the service account. To create a user in the Google Admin console:
- Navigate to Directory > Users.
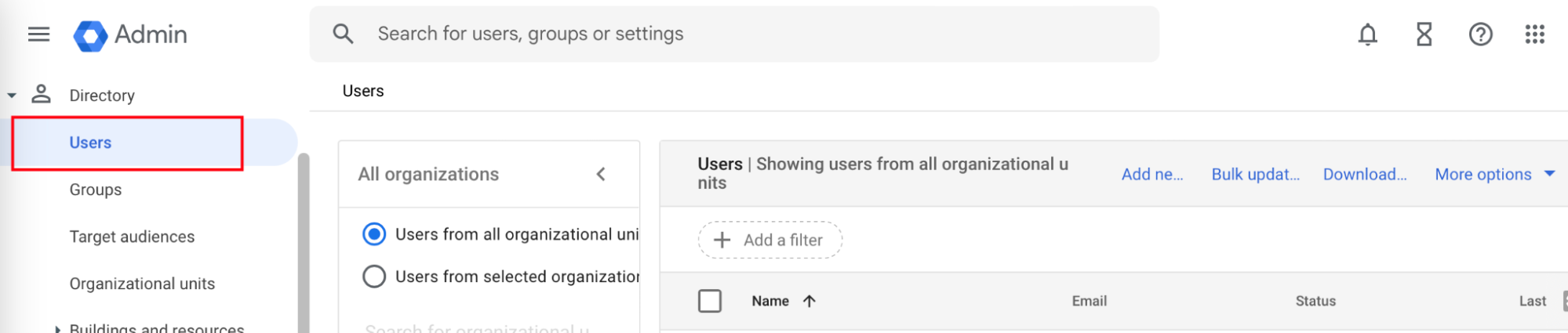
- Click Add new user. The Add new user form opens.
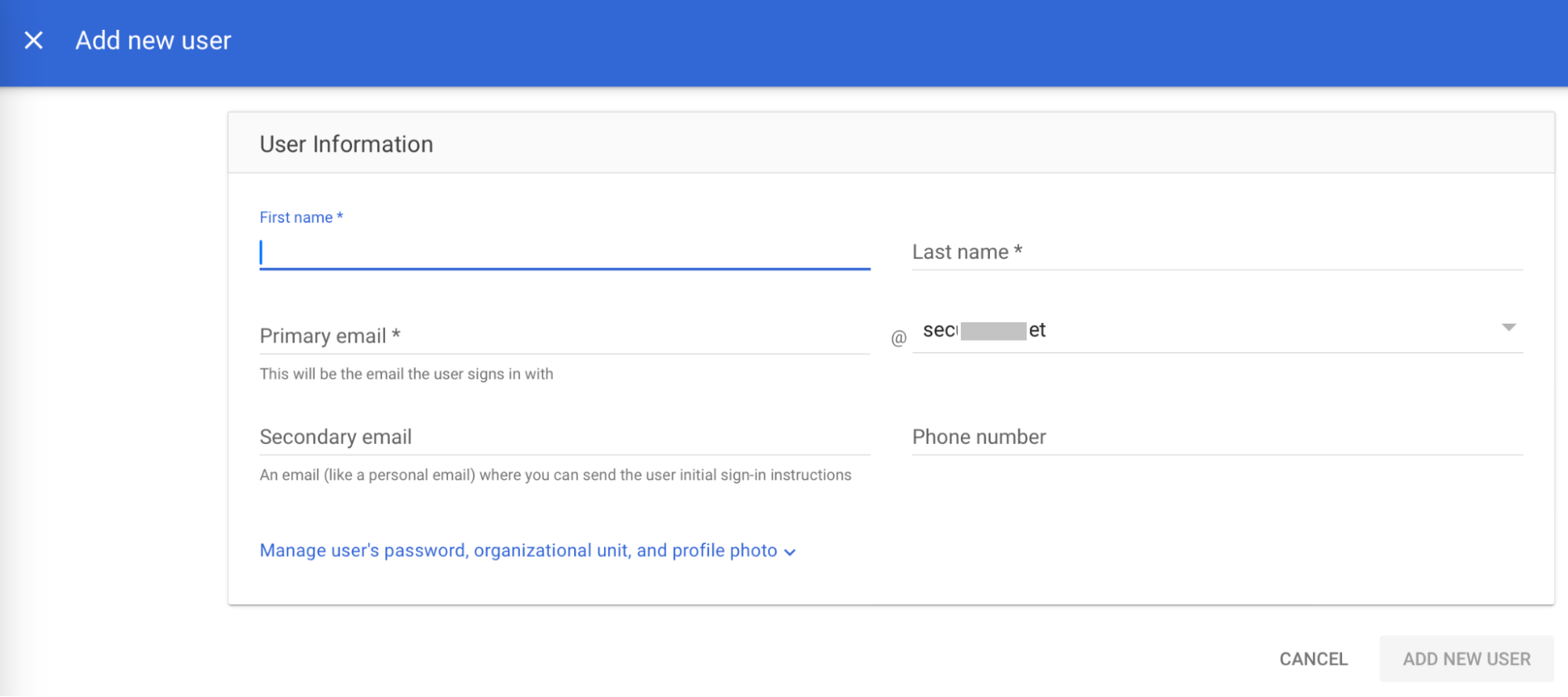
- In the First name field, enter a first name for the user.
- In the Last name field, enter a last name for the user.
- In the Primary email field, enter the organizational email of the user.
- Click ADD NEW USER.
4.3 Creating a Role with Read-only Access
A role with the read-only access privileges should be assigned to the created user. To create role:
- Navigate to Accounts > Admin Roles.
- Click Create new role. The Create role page opens.
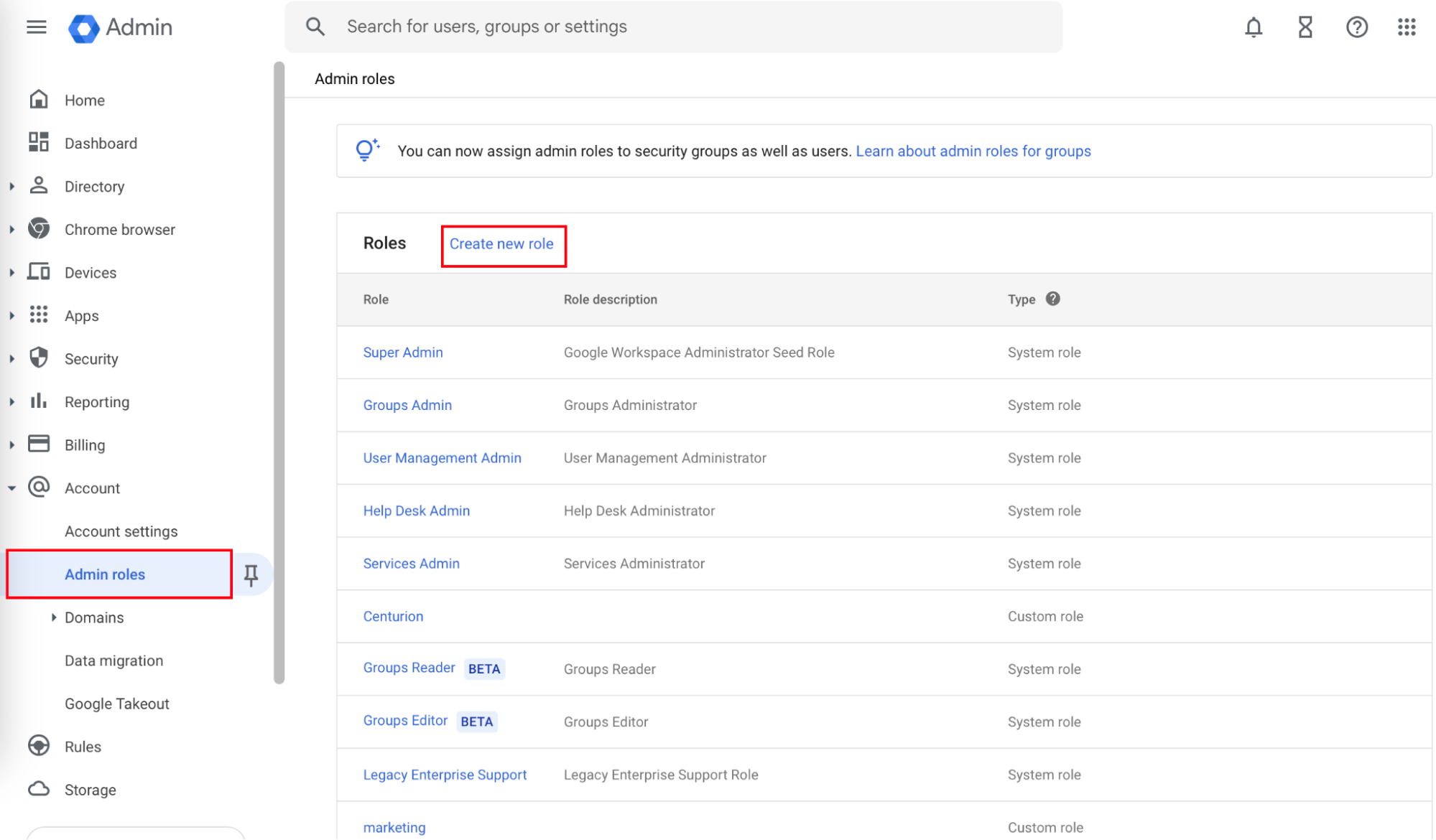
- In the Role info section, for the Name field, enter a name for the role.
- In the Description field, enter a description for the role.
- Click Continue.
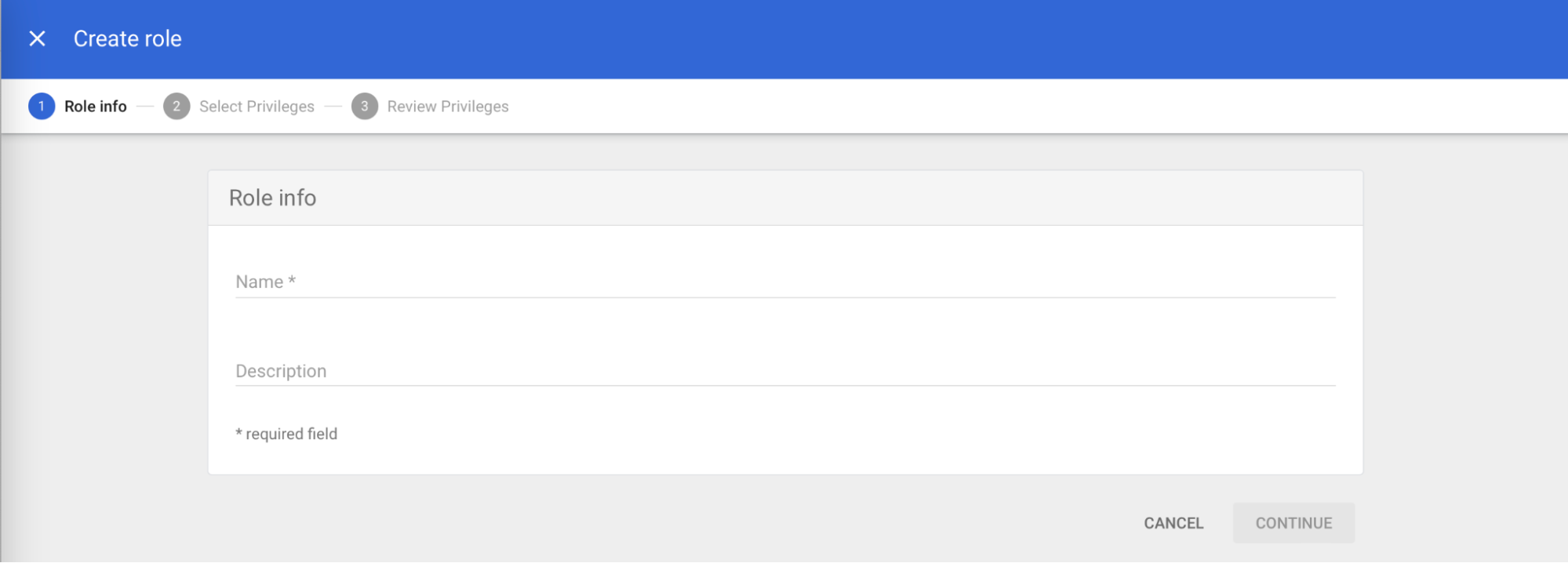
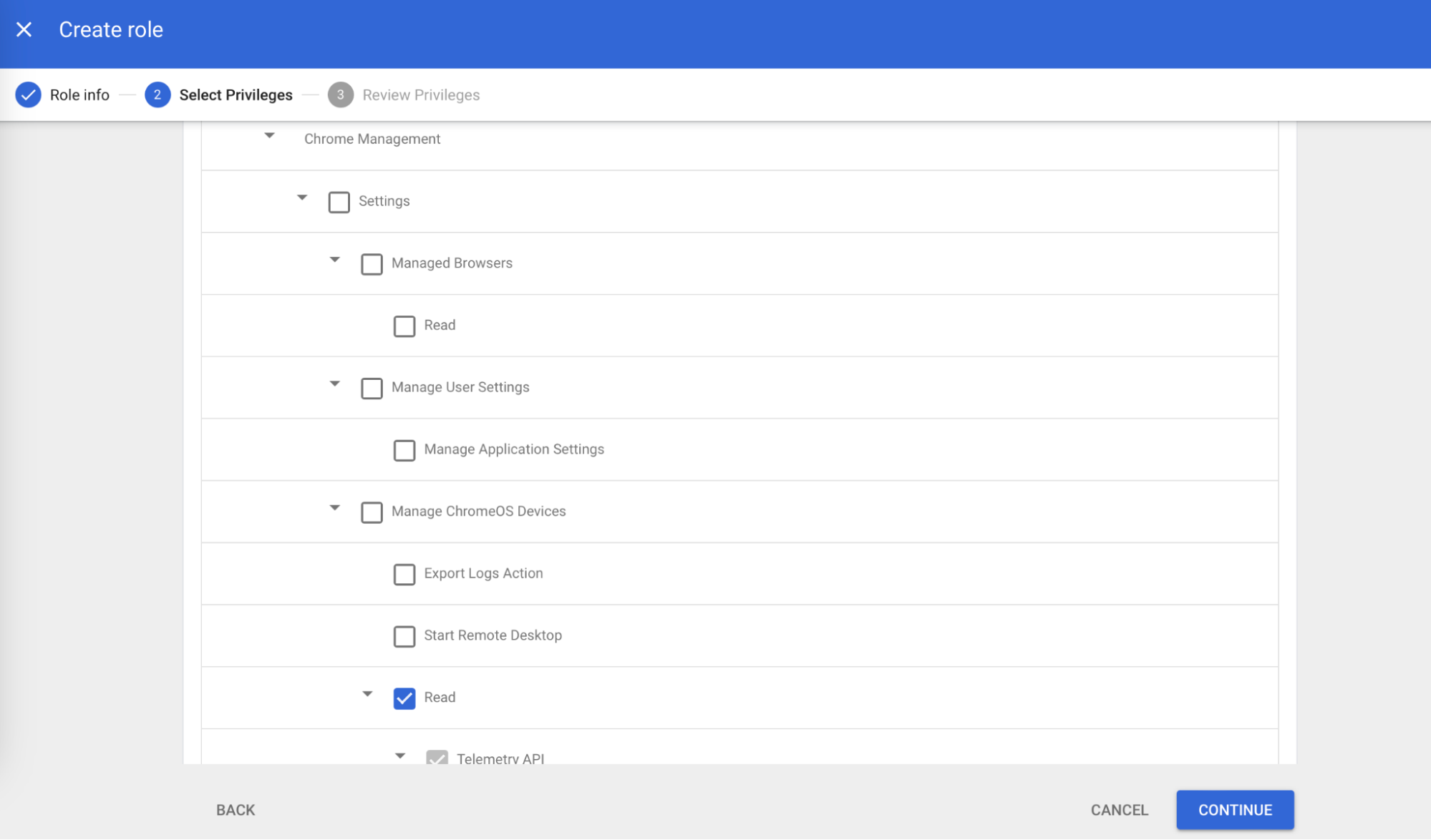
- In the Select Privileges tab, select the following access privileges:
- Admin console privileges:
Chrome Management > Settings > Manage ChromeOS Devices > Read - Admin API privileges:
- Users > Read
- Groups > Read
- Admin console privileges:
- Click CONTINUE. Review the privileges assigned and click DONE.
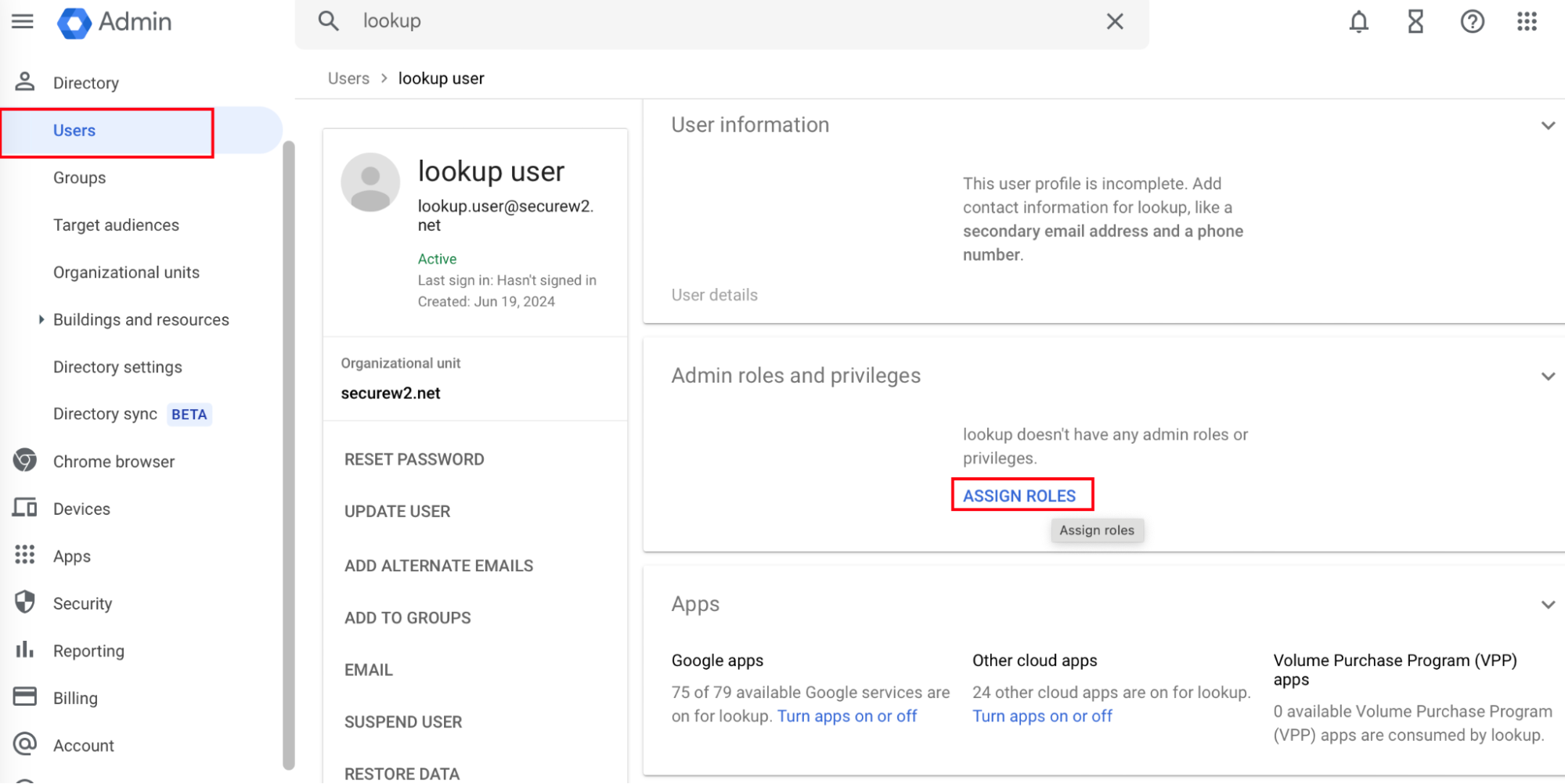
- Navigate to Users and select the user created in 4.2 Creating a User in Google Admin Console section.
- Click ASSIGN ROLES.
- Assign the created role with read only privileges to the user.
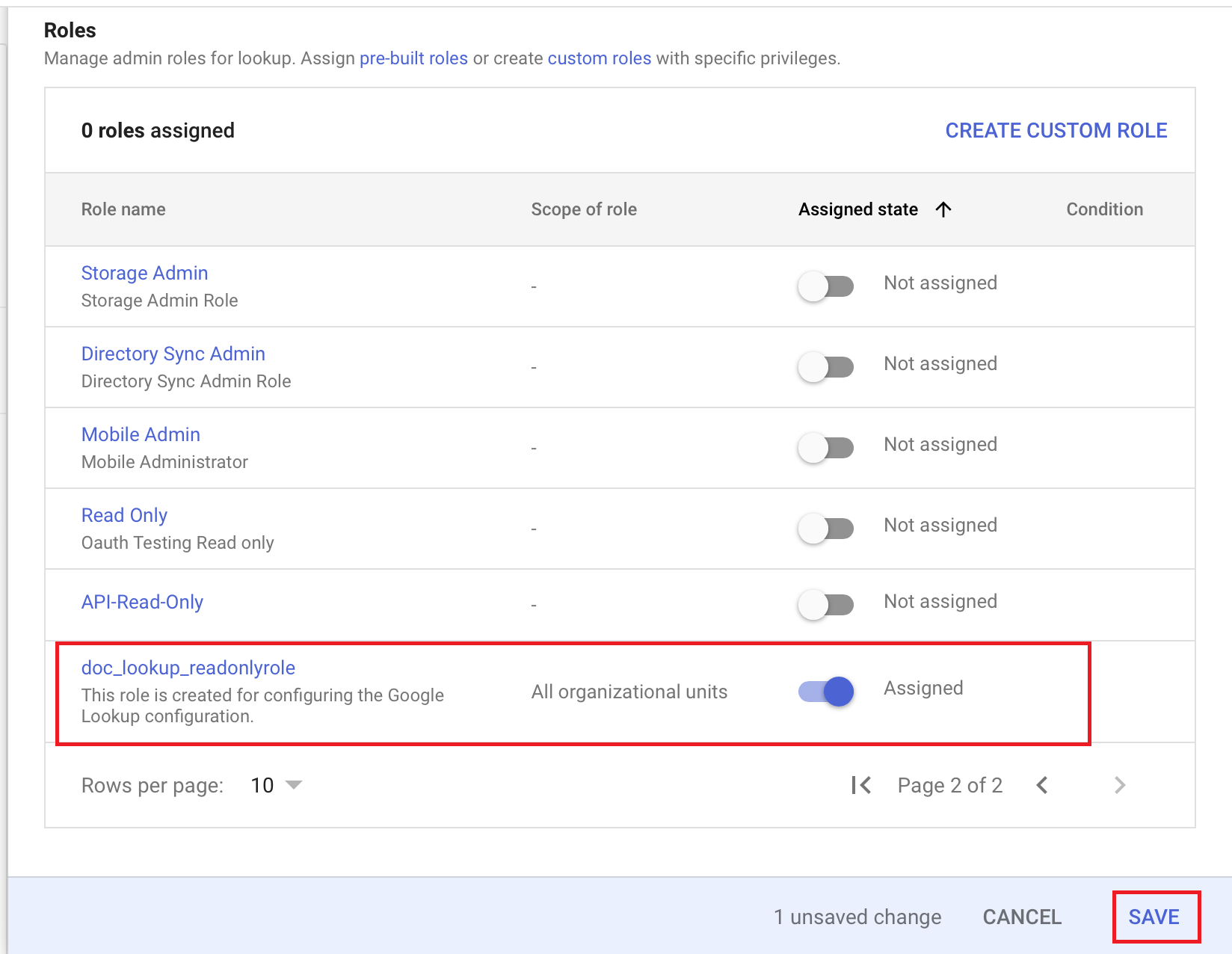
- Click SAVE.
5. Configuring JoinNow
The following are the high level steps to configure JoinNow for Google Identity Lookup
5.1 Creating a Certificate Template for Google Lookup
A certificate template determines how information is encoded in the certificate to be issued by the Certificate Authority. It will consist of a list of certificate attributes and how the information must be encoded in the attribute values. This information is provided by the organization administrator using the JoinNow Management Portal.
SecureW2 recommends creating a separate template for each MDM platform for easier identification of different values being passed. To create an Certificate Template for Google lookup:
- Navigate to Dynamic PKI > Certificate Authorities.
- Click Add Certificate Template.
- In the Basic section, for the Name field, enter the name of the certificate template.
- In the Subject field, retain the default values hardcoded in the certificate template.
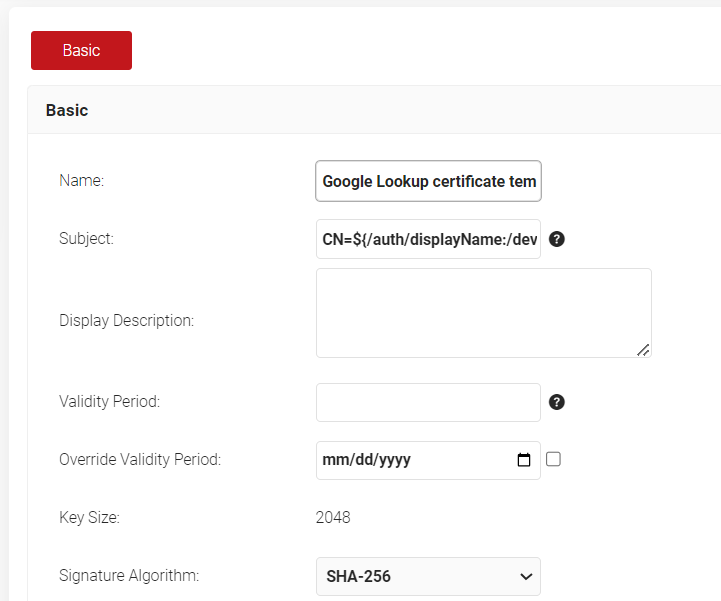
- In the Display Description field, enter a suitable description for the certificate template.
- In the Validity Period field, type the validity period of the certificate (based on the requirement).
- From the Signature Algorithm drop-down list, select the signature algorithm for the certificate signing request. The option available is SHA-256.
- In the SAN section, for Other Name, RFC822, DNS, and URI fields, retain the default values provided in the certificate.
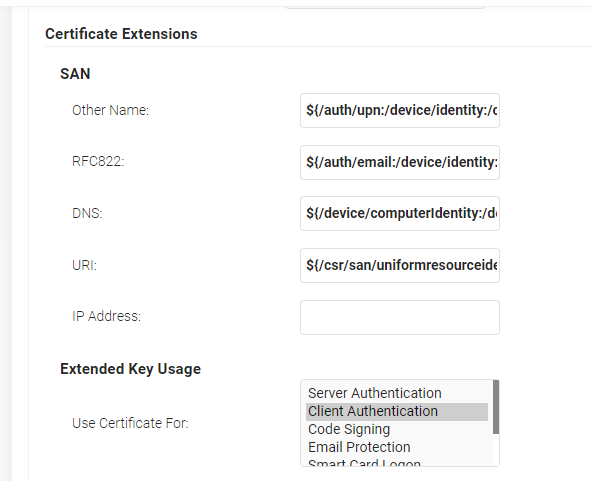
- Click Save.
5.2 Creating a Google Workspace Identity Lookup Provider
Before the certificate issuance and during the RADIUS authentication process, Identity Lookup feature validates that a device/user is active within the organization by checking the identifying information against the existing accounts in the Identity Provider.
To create an Identity Lookup Provider:
- Navigate to Integrations Hub > Core Platforms.
- Click Add.
- On the displayed screen, enter a Name and Description of the Identity Provider.
- From the Type drop-down list, select Google Workspace .
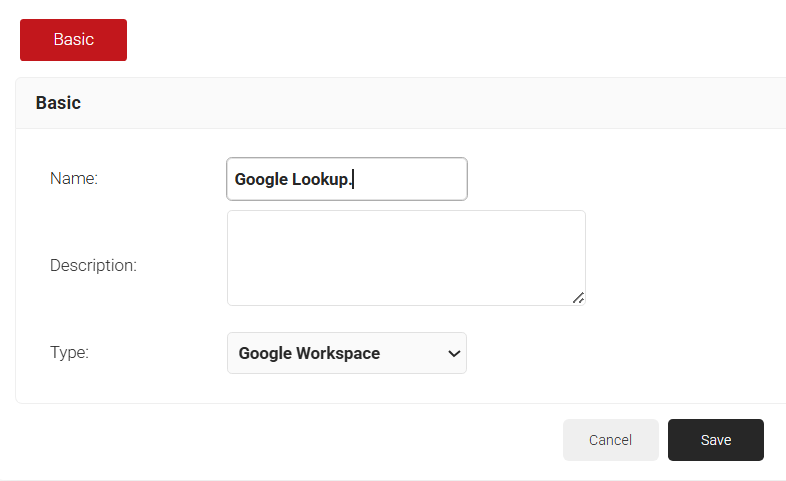
- Click Save. The page refreshes and the Configuration, Attribute Mapping, and Groups tabs appear.
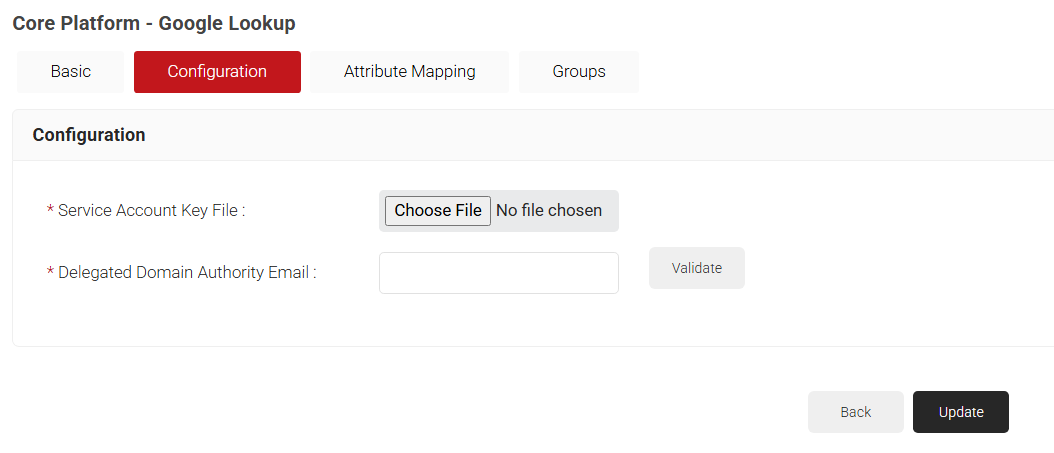
- Under the Configuration tab, provide the following information:
- In the Service Account Key File field, click Choose File. Select the JSON Key file created in 3.3 Creating A Service Account and a JSON Key File section. Upload the file.
- In the Delegated Domain Authority Email field, enter the Primary email entered for the user in 4.2 Creating a User in Google Admin Console section.
- Click Validate to check the validity of the primary email entered.
- Click Update.
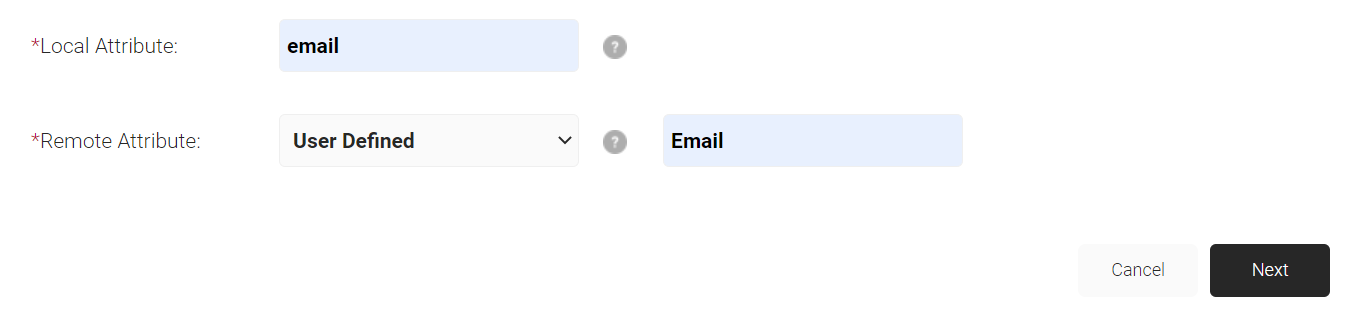
- In the Attribute Mapping tab, In the Local Attribute field, enter a name for the attribute.
- In the Remote Attribute field, select the attribute to be mapped to the Local Attribute. If your preferred attribute is unavailable in the drop-down, select User Defined and enter the value to be mapped.
- Click Next to add more attributes.
- Navigate to the Groups tab.
- Click Add.
a. In the Local Group field, enter a name for the group. This name will be displayed as your ‘Group‘ in the JoinNow Management Portal when you configure policies.
b. In the Remote Group field, enter the name of your group as it is configured in the Google Workspace. - Click Create.
- Repeat as necessary for any Group you wish to create Network Policies around.
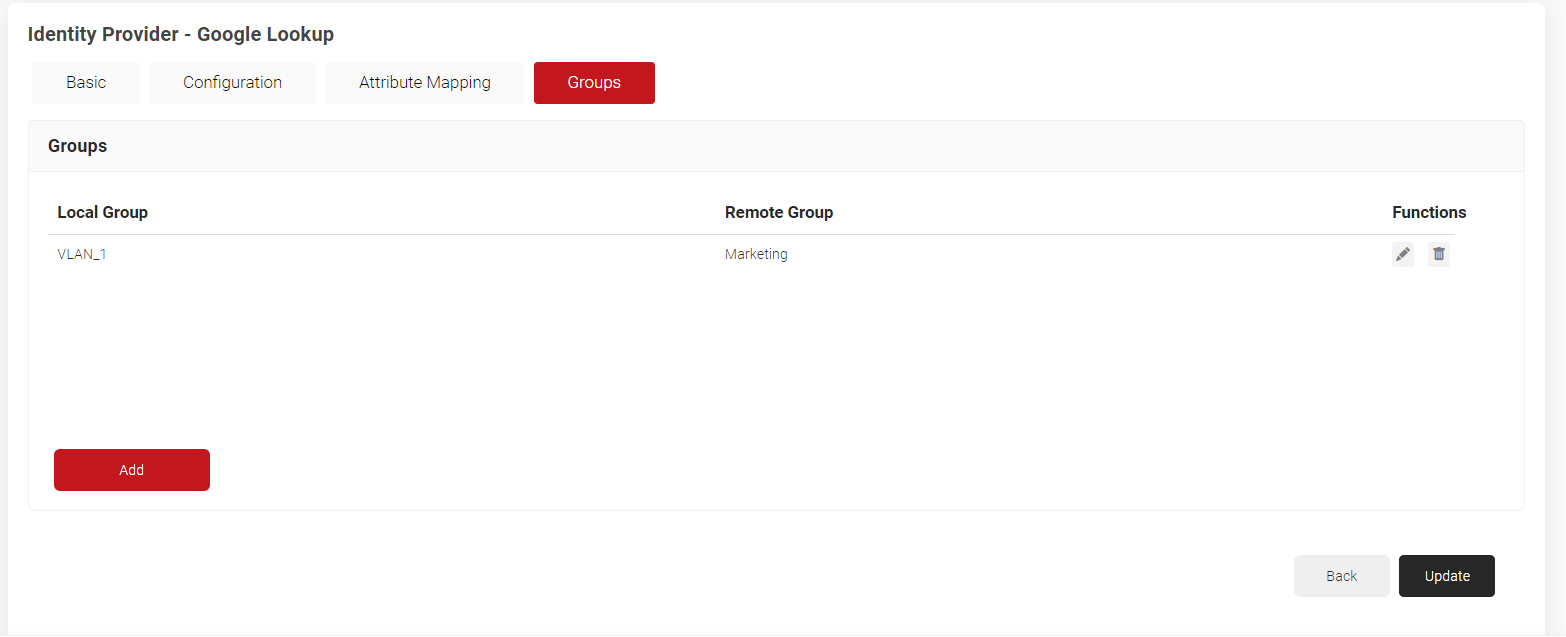
- Click Update.
5.3 Configuring Policies
SecureW2 policies allow the organization administrators to segment users and restrict/allow resources based on information stored in their directory entry. Since enforcement occurs at runtime, changes made to a user’s permissions are propagated immediately rather than a day or two later, as is typical with most RADIUS servers.
5.3.1 Creating a Security Signal Source
Lookup Policies are how we tie the new Identity Lookup Provider to domains. Here you create a condition that ties your domain to the new Identity Lookup Provider you just created in the previous section.
- Navigate to Policy Management > Security Signal Sources.
- Click Add Security Signal Source.
- On the displayed screen, enter a Name and Display Description of the Security Signal Source.
- Lookup Purpose – Purpose of Account Lookup
a. Certificate Issuance – To lookup user/device account during Enrollment.
b. RADIUS Authentication – To lookup user/device account during RADIUS Authentication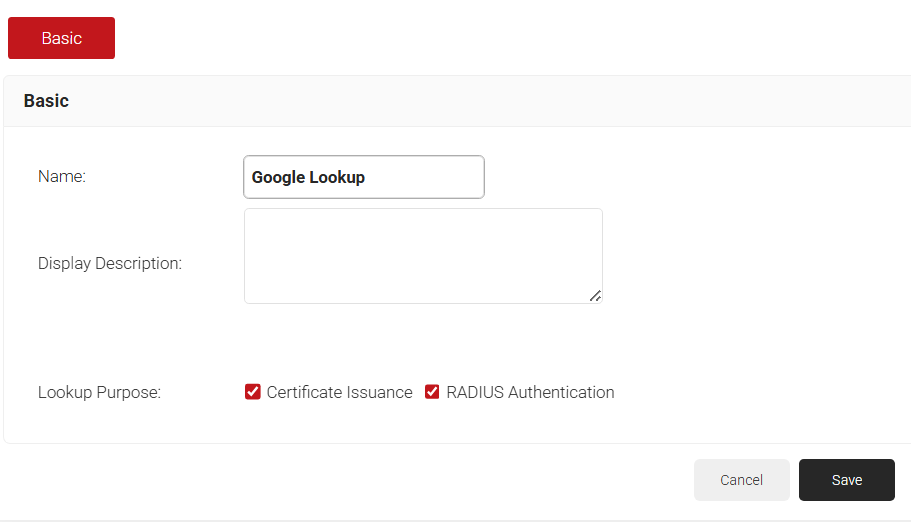
- Click Save. The Conditions and Settings tabs appear.
- Click the Conditions tab.
- From the Identity drop-down list, select the required identity attribute for lookup.
- In the Regex field, enter the value you want to match.
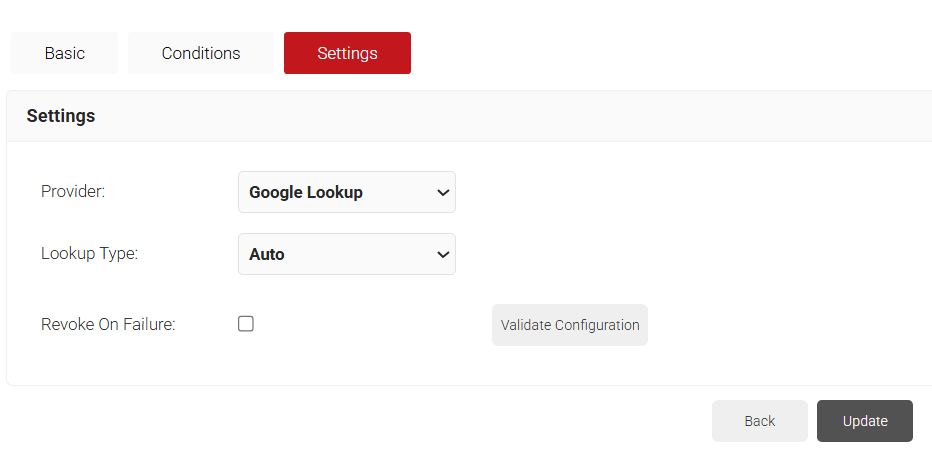
- Under the Settings tab, from the Provider drop-down list, select the Google Workspace Identity Lookup you created in the 5.2 Creating a Google Workspace Identity Lookup Provider section.
- From the Lookup Type drop-down, select:
- Auto – The system automatically uses identity as the Lookup attribute.
- Device – The Identity drop-down list is displayed. Select a device identity required for lookup.
- User – The Identity drop-down list is displayed. Select a user identity required for lookup.
- Click Update.
5.3.2 Policy Workflows
To create a policy engine workflow:
- Navigate to Policy Management > Policy Workflows.
- Click Add Policy Workflow.
- On the displayed screen, enter a Name and Display Description for the policy workflow.
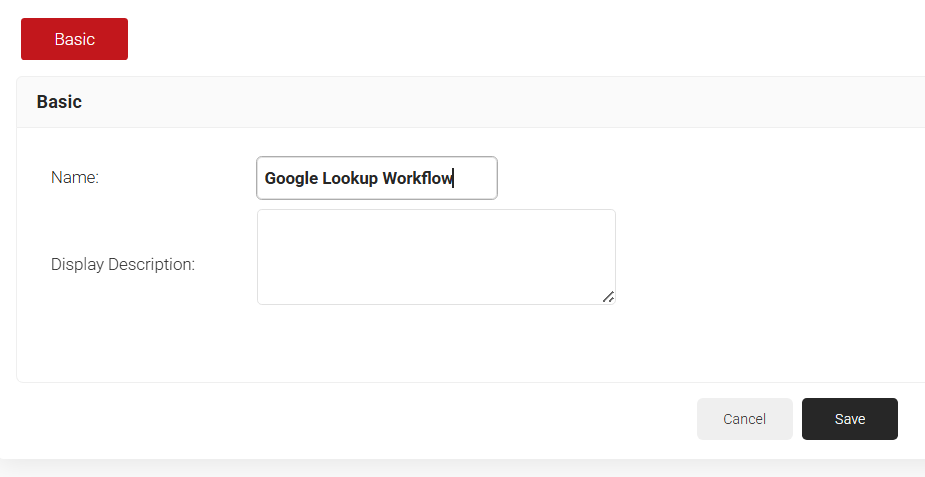
- Click Save.
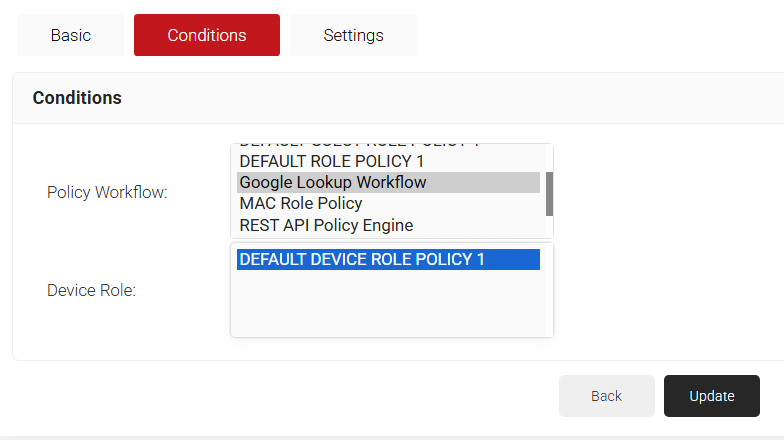
- Navigate to Conditions.
- From the Identity Provider drop-down list, select the Identity Provider you created in 5.2 Creating Identity Lookup Provider section.
- Click Update.
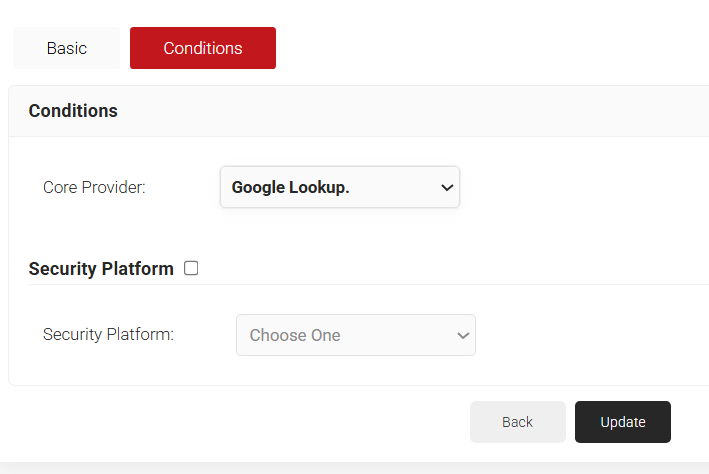
5.3.3 Enrollment Policy
Now, the lookup can be used before the certificate issuance as a dynamic check. To trigger the lookup during the certificate issuance, map the policy engine workflow created in section 5.3.2 Policy Workflows in the enrollment policy created below:
- Navigate to Policy Management > Enrollment Policies.
- Click Add Enrollment Policy.
- Under the Basic section, in the Name field, enter the name of the enrollment policy.
- In the Display Description field, enter a suitable description for the enrollment policy.
- Click Save.
- The page refreshes, and the Conditions and Settings tabs are displayed.
- Select the Conditions tab.
- In the Conditions section, from the Role drop-down list, select the role policy you created earlier (see the 5.3.2 Policy Engine Workflow section).
- From the Device Role drop-down list, select DEFAULT DEVICE ROLE POLICY.
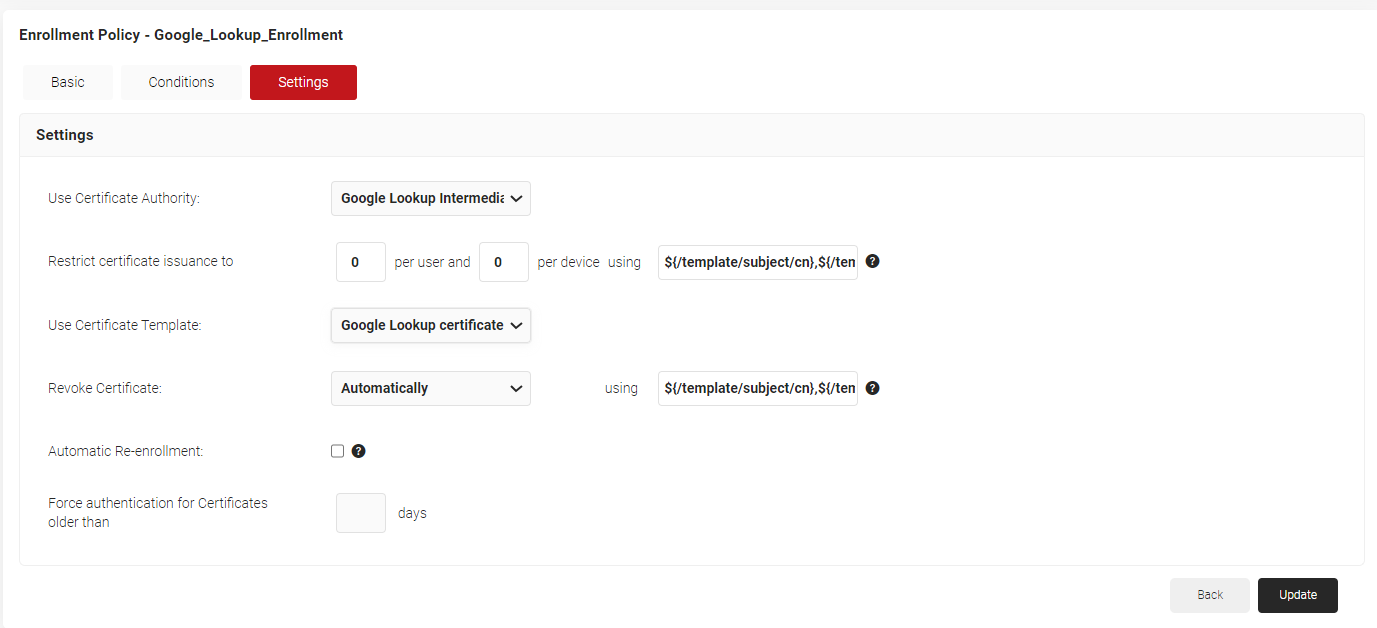
- Select the Settings tab.
- In the Settings section, from the Use Certificate Authority drop-down list, select the intermediate CA you created earlier.
- From the Use Certificate Template drop-down list, select the certificate template created for Google SCEP in 5.1 Creating a Certificate Template for Google Lookup section.
- In the other settings, retain the default values.
- Click Update.
5.3.4 Network Policy
Similar to the check during certificate issuance, Lookup can be used before the RADIUS Authentication as a dynamic check. To trigger the lookup during the RADIUS Authentication, map the policy engine workflow created in section 5.3.2 Policy Workflows in the Network Policy created below:
- Navigate to Policy Management > Network.
- On the Network Policies page, click Add Network Policy.
- On the displayed screen, enter a Name and Displayed Description for the network policy in the corresponding fields.
- Click Save.
- Click the Conditions tab.
- Click Add rule and select the user role you want to assign to this network policy.
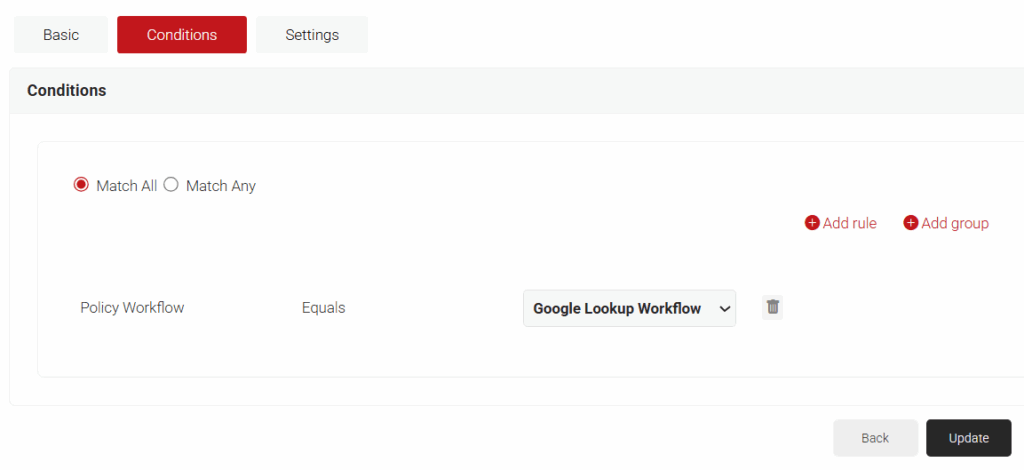
NOTE: You can assign a network policy to multiple user roles. - Click the Settings tab.
- Click Add Attribute.
- From the Dictionary drop-down-list, select an option: Radius:IETF or Custom.
- From the Attribute drop-down-list, select an option.
- In the Value field, enter the appropriate value for the attribute.
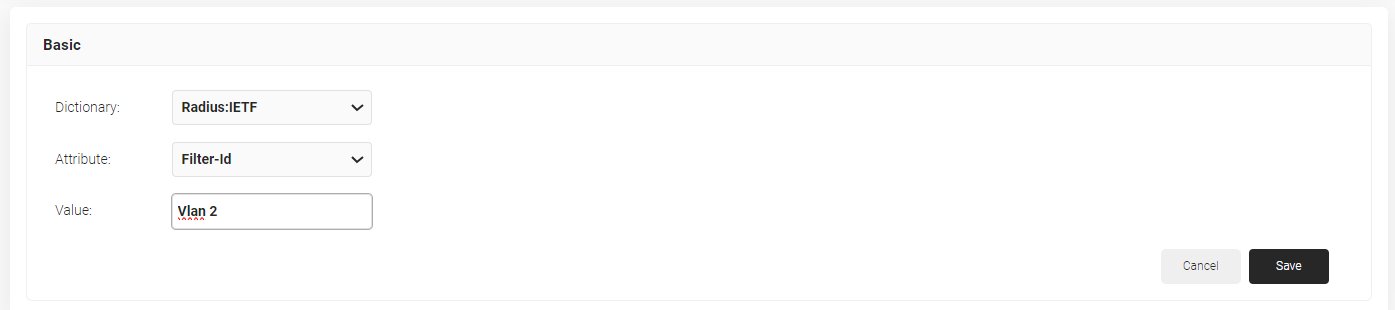
- Click Save.
- Click Update.
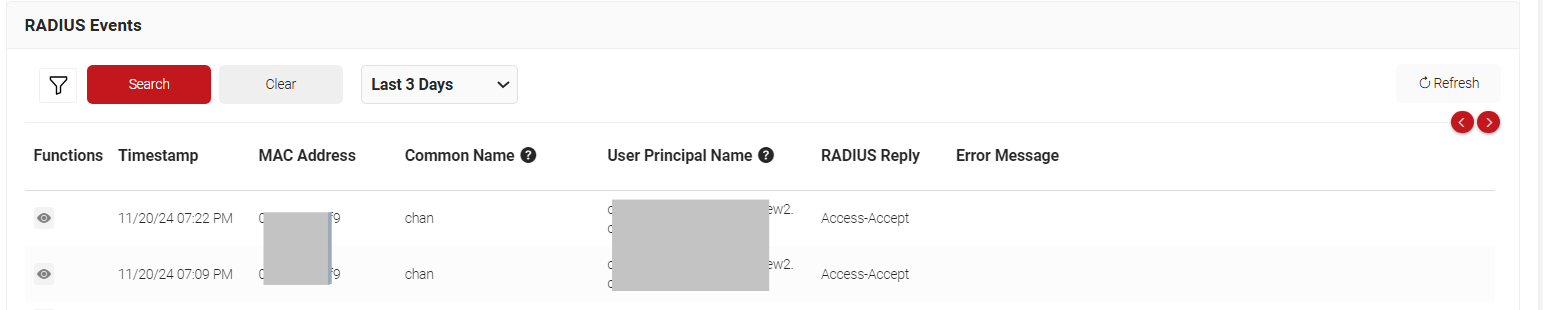
Conclusion
Post successful configuration, admins can check for successful RADIUS Authentication under Data and Monitoring > RADIUS Events. In case of Certificate Issuance, a message would be displayed for the device enrolled under Data and Monitoring > General Events