Implementing WPA2-Enterprise with Dynamic RADIUS and Okta
Digital certificates have proven that networks can bolster their security without sacrificing user experience. Though many have dismissed certificate-based authentication in the past, it has become a gold standard for wireless security.
SecureW2 provides a Managed Cloud PKI solution allowing Okta customers to implement 802.1x and certificate-based authentication. This setup makes it easier to configure WPA2-Enterprise Wi-Fi and user authentication for Wi-Fi, VPN, Web Apps, Desktop Logon, etc. Check out our setup guide on how to configure WPA2-Enterprise with Okta.
SecureW2’s PKI is built with a Dynamic RADIUS server that can be configured to communicate with your directory and enforce user policies at the time of authentication. Cloud RADIUS empowers organizations with certificates because it’s the only RADIUS server that can securely communicate with Cloud Identity Providers (IDP). Admins no longer have to reissue brand new certificates in case a user’s policy changes and the system will update immediately.
Below, we lay out how you can integrate SecureW2’s Dynamic RADIUS with your Okta setup.
Creating API Token
- Log in to the Okta Portal.
- On the left pane, from the Security menu, select API.
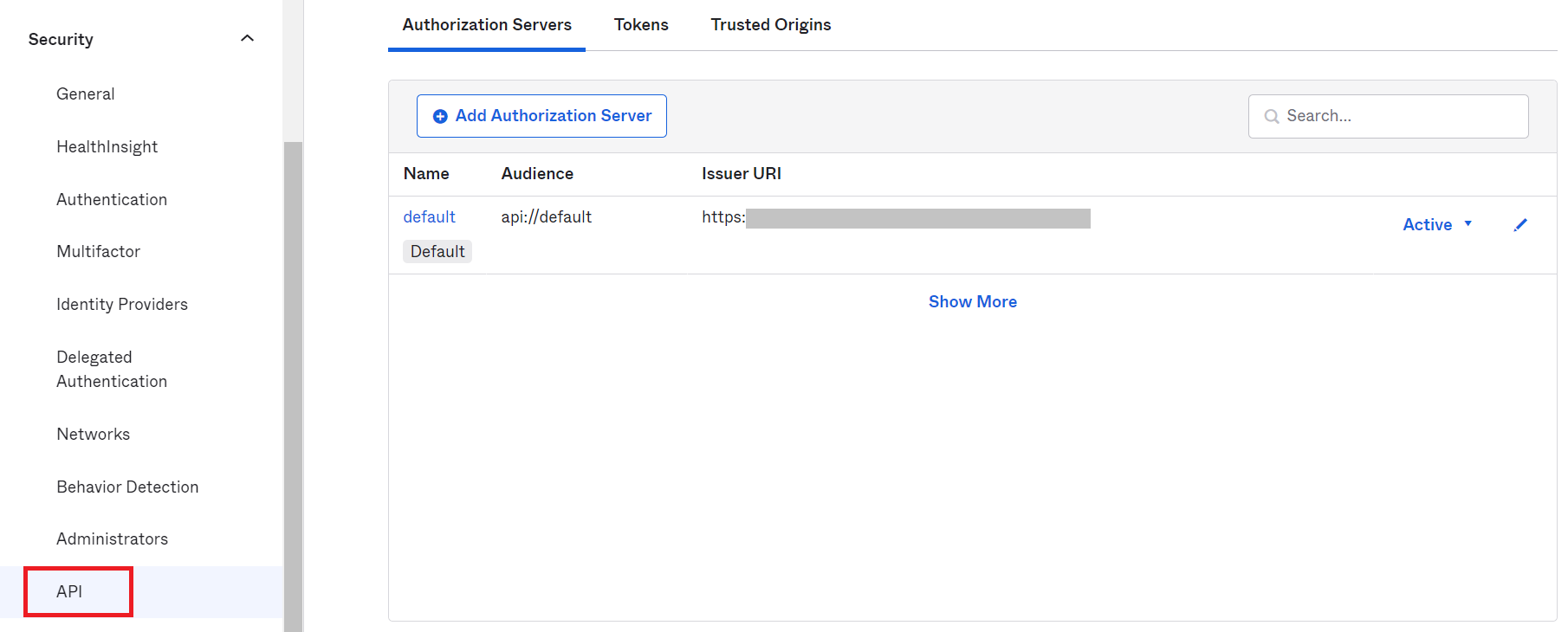
- Click Tokens and on the displayed screen, click the Create Token button.
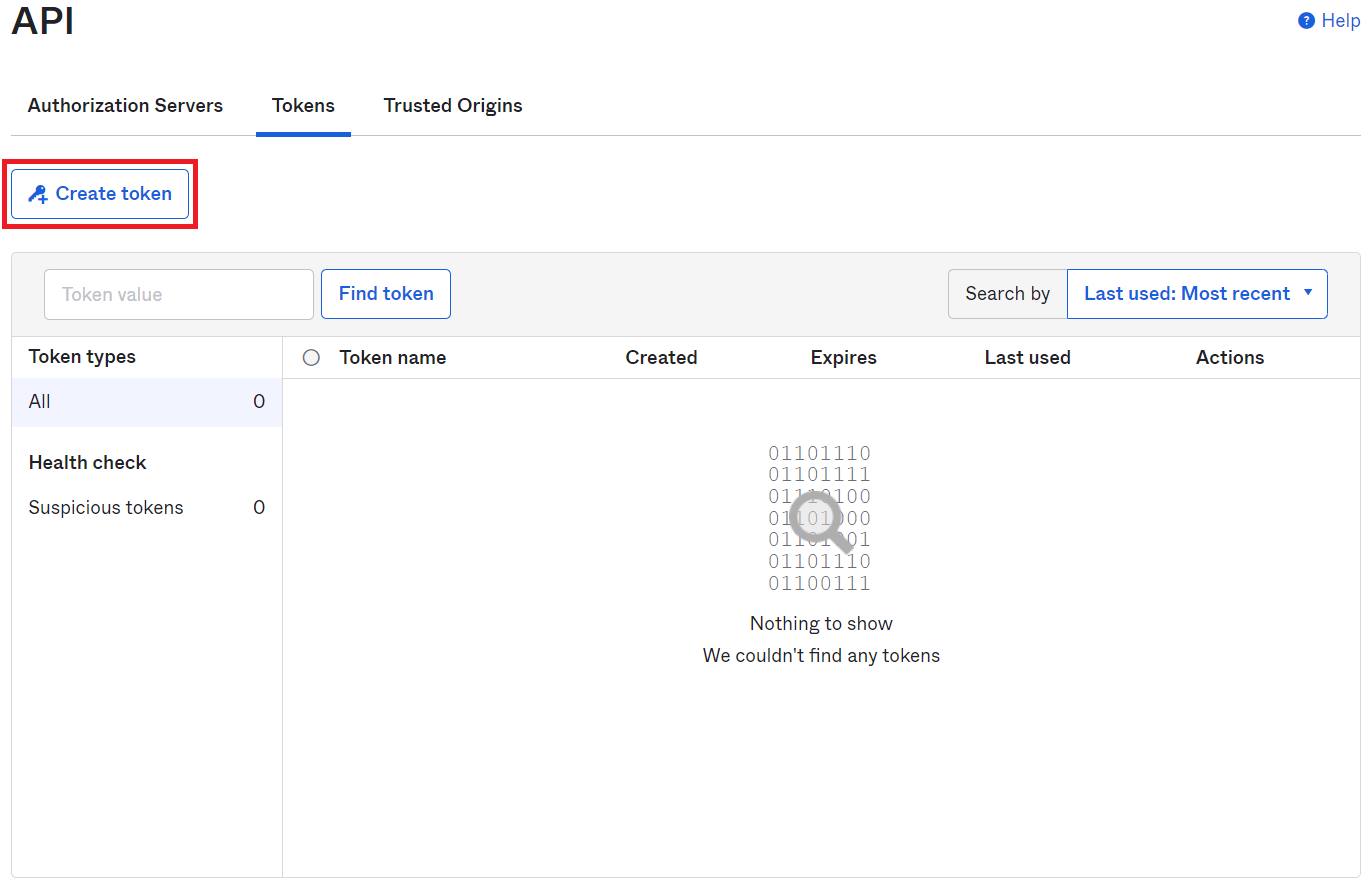
- In the Create token dialog box, enter a name for the token and click Create Token.
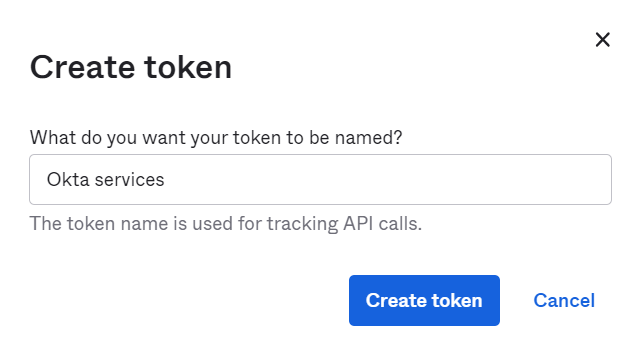
- On the displayed screen, copy the token value on your console.
NOTE: Ensure that you save the token value on your console.
Getting Started
After creating an API token in Okta, you need to run the Getting Started wizard, create an Identity Lookup Provider in SecureW2 to communicate with Okta, and finally create user and group policies to implement network authentication.
The Getting Started Wizard creates everything you need for 802.1x. It will generate a RADIUS Server, Network Profiles, a Landing Page for Device Onboarding, and all the default network settings you will need for 802.1x.
NOTE: If you have already configured SecureW2 for your network, you may skip this step.
- Navigate to Device Onboarding > Getting Started.
- From the Profile Type drop-down list, select the network profile type.
- In the SSID text box, type a name for the SSID.
- From the Security Type drop-down list, select WPA2-Enterprise.
- From the EAP Method drop-down list, select EAP-TLS.
- From the Policy drop-down list, select DEFAULT.
- From the Wireless Vendor drop-down list, select a wireless provider.
- From the RADIUS Vendor drop-down list, select a RADIUS vendor.
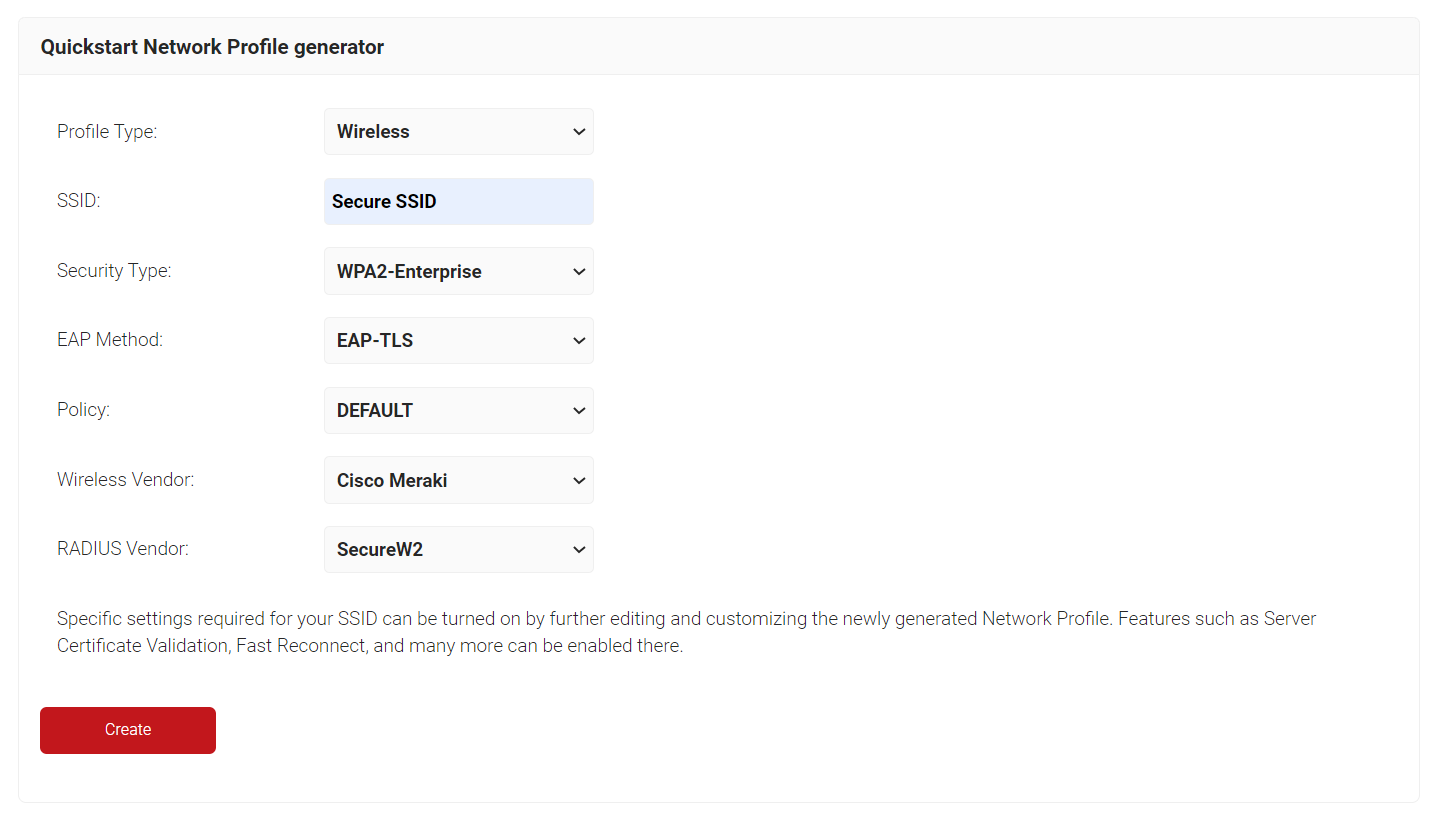
- Click Create. Your network profile is generated.
NOTE: The Getting Started wizard typically takes 60-90 seconds to create everything required. Wait for the process to complete before moving to the next steps.
Creating Identity Lookup Provider
An identity provider (IDP) is the system that proves the identity of a user/device. Creating an IDP in SecureW2 tells the Cloud Connector system how to connect to your Okta user database, verify user credentials, and issue certificates.
During the authentication process, identity lookup validates that a user is active within the organization by checking the identifying information against the existing users in the Identity Provider.
- Navigate to Identity Management > Identity Providers.
- Click Add Identity Provider.
- On the displayed screen, enter a Name and Description of the Identity Provider.
- From the Type drop-down list, select Okta Identity Lookup.
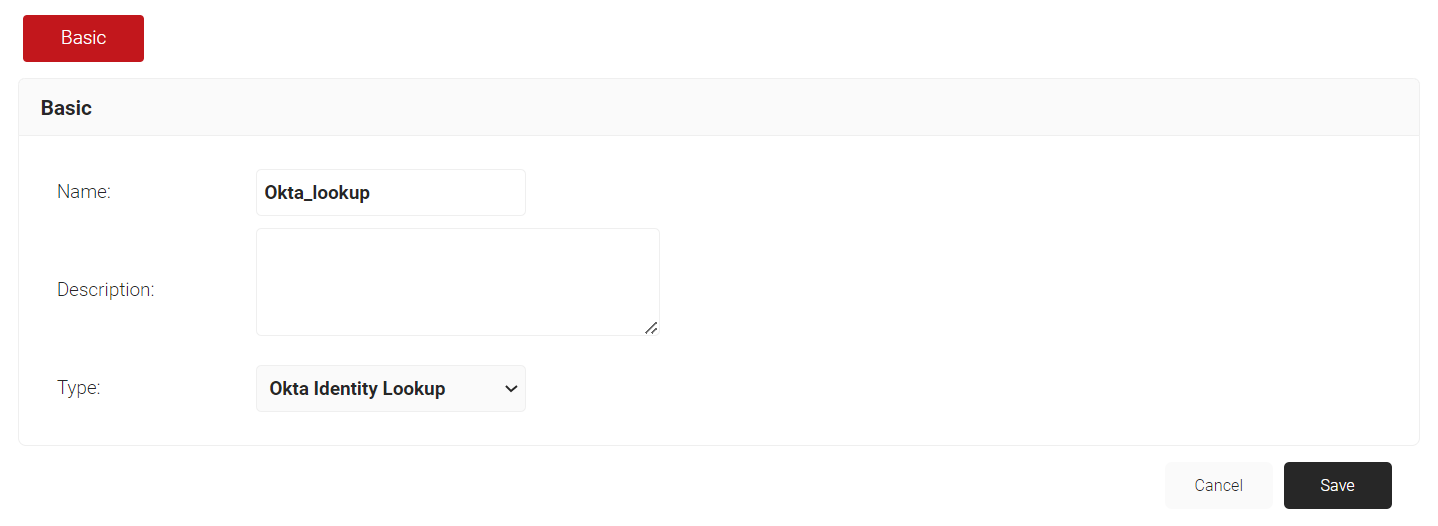
- Click Save.
- On the displayed screen, click the Configuration tab.
- In the Provider URL field, enter your Okta organization URL. For example, https: /dev- 123456.okta.com/.
NOTE: Do not use "admin" in the organization URL as lookup fails.
- In the API Token field, enter the token you obtained from the Okta portal (see the Creating API Token section).
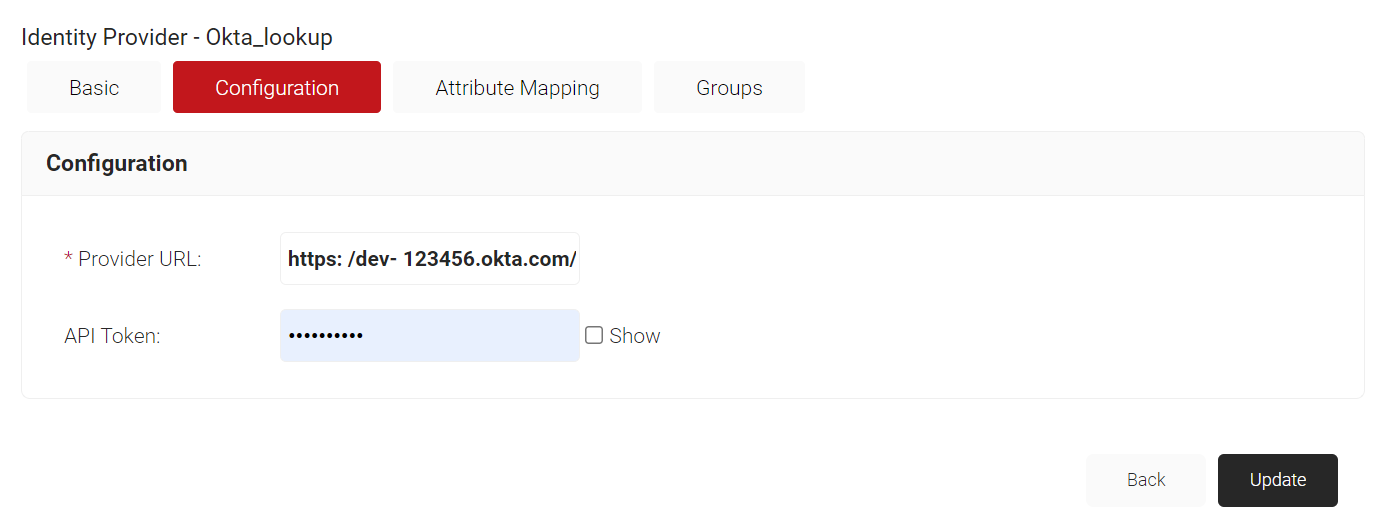
- Click Update.
- In the Provider URL field, enter your Okta organization URL. For example, https: /dev- 123456.okta.com/.
The Identity Lookup Provider is displayed on the Identity Providers page.
NOTE: If the Identity Lookup Provider is deleted in the JoinNow MultiOS Management Portal, the app in the Okta portal is also deleted.
Adding Attributes
To add a custom attribute to the identity lookup provider, follow the given steps.
- Navigate to the Attribute Mapping tab.
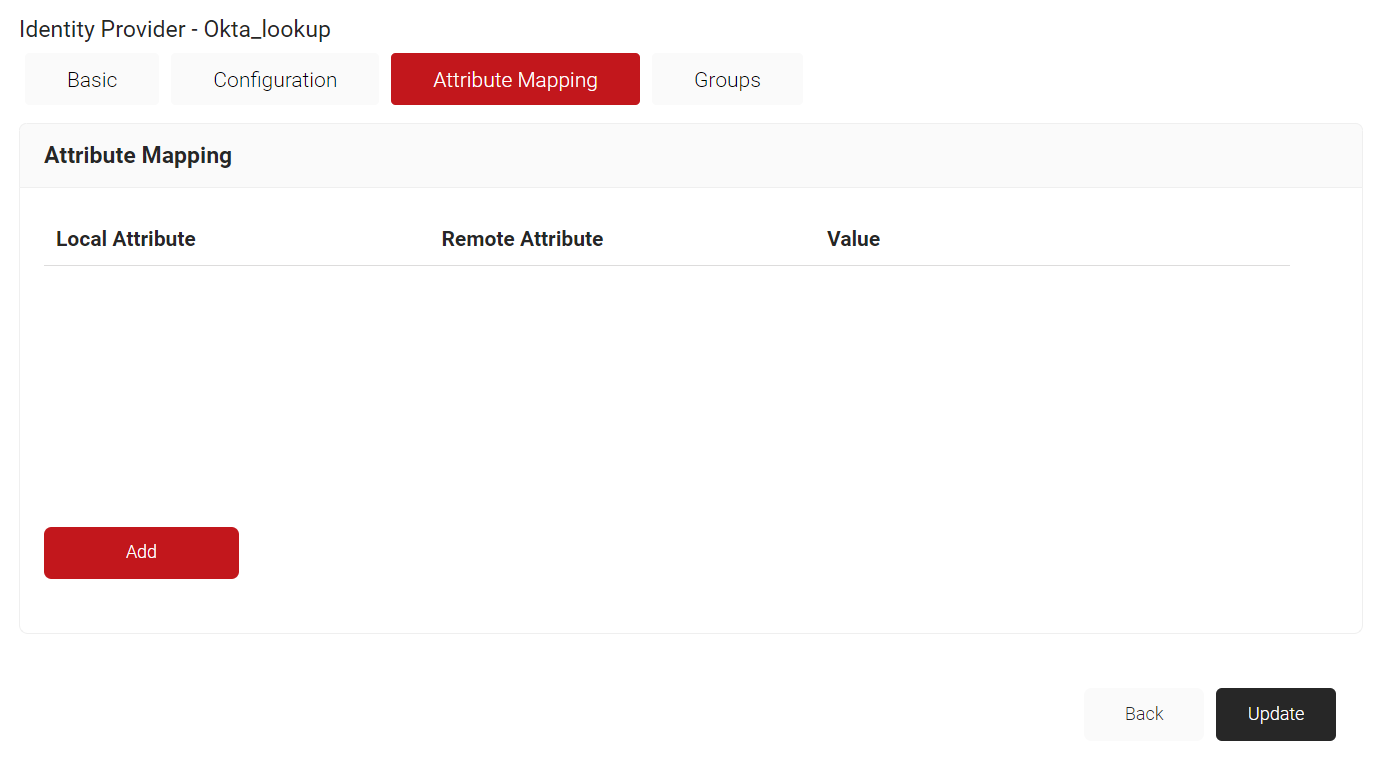
- Click Add.
- In the Local Attribute field, enter a name for the attribute.
- In the Remote Attribute field, select the attribute to be mapped to the Local Attribute. If you select User Defined, enter a value to be mapped.
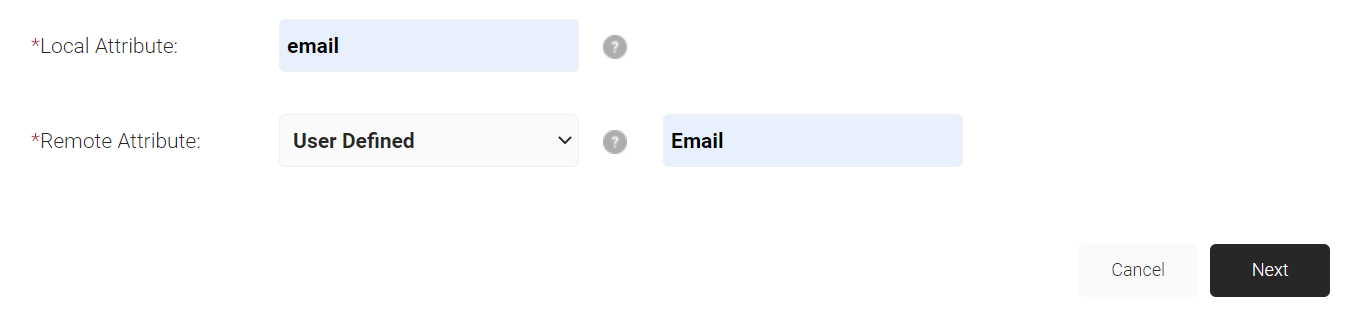
- Click Next to create the custom attribute with the appropriate mapping.
- Click Update.
Configuring Groups
Cloud RADIUS can perform a User Group Lookup. So, we can create network access policies based on the groups a user is in.
- Navigate to the Groups tab.
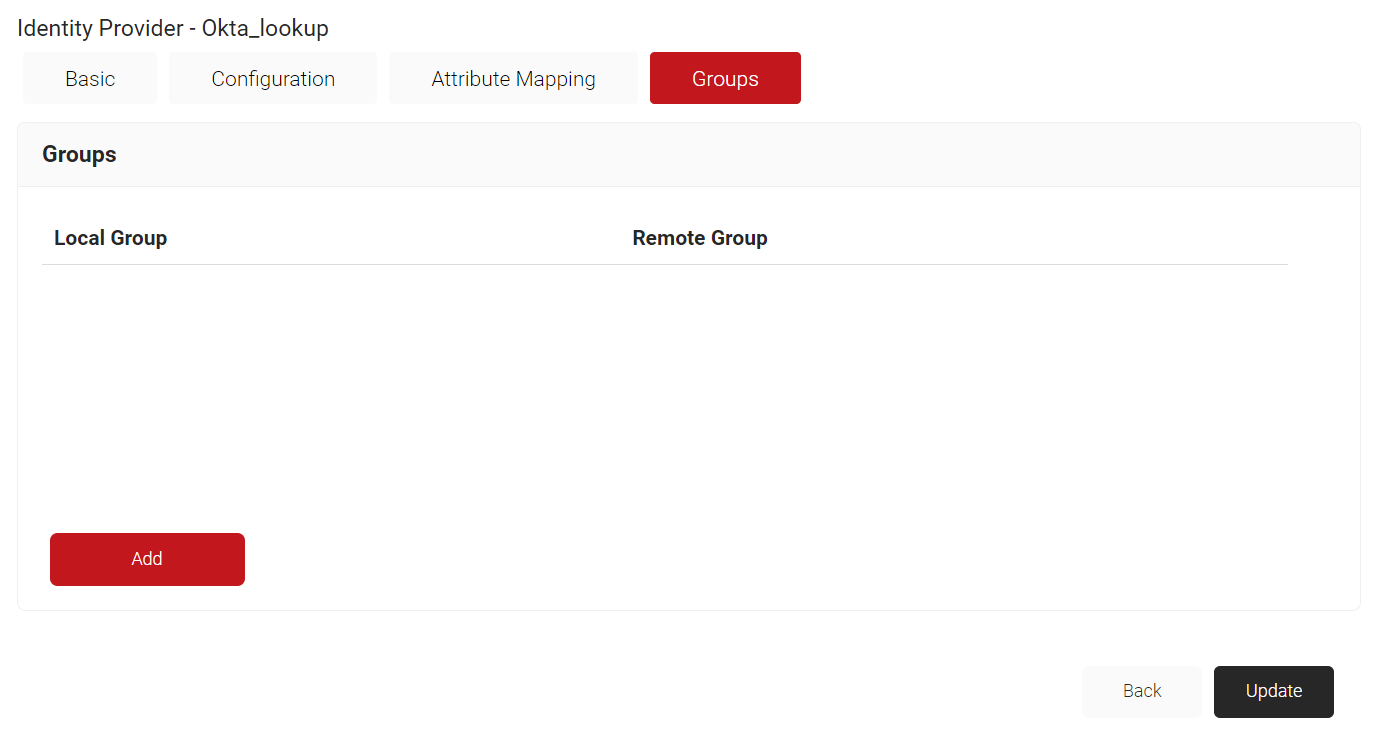
- Click Add.
- In the Local Group field, enter a name for the group. This name will be displayed as your 'Group' in the JoinNow MultiOS Management Portal when you configure policies.
- In the Remote Group field, enter the name of your group as it is configured in the Okta portal.

- Click Create.
NOTE: Repeat the process as required for the groups you wish to create network policies around.
Configuring Policies
By integrating Dynamic RADIUS with Okta, the RADIUS can segment users and determine access levels for each user based on their stored directory information. Better yet, enforcement occurs at runtime, meaning the changes you make to a user’s permissions will be implemented immediately instead of taking a day or two to complete.
The following policies need to be configured:
Account Lookup Policy
Lookup Policies are how we tie our new Identity Lookup Provider to domains. Here we will create a condition that ties our domain to the new Identity Lookup Provider we just created in the previous section.
- Navigate to Policy Management > Account Lookup Policies.
- Click Add Account Lookup Policy.
- On the displayed screen, enter a Name and Display Description of the Account Lookup Policy.
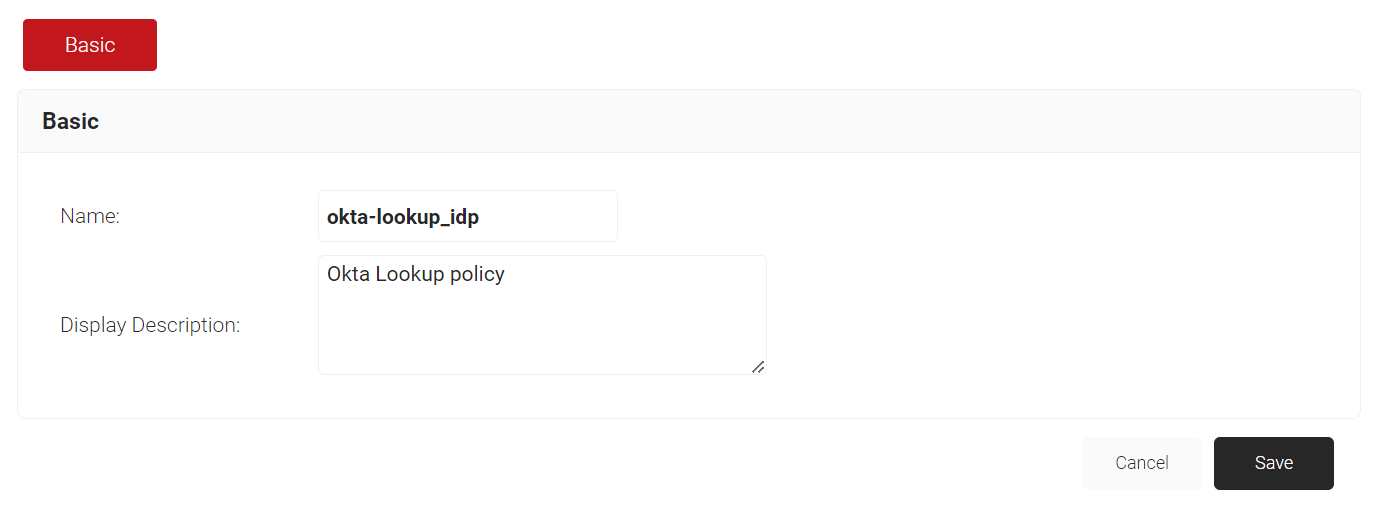
- Click Save.
- Click the Conditions tab.
- From the Identity drop-down list, select an option from the following:
- Username
- Certificate-CommonName
- Certificate-SAN-UPN
- Certificate-SAN-Email
- In the Regex field, enter the value you want to match.
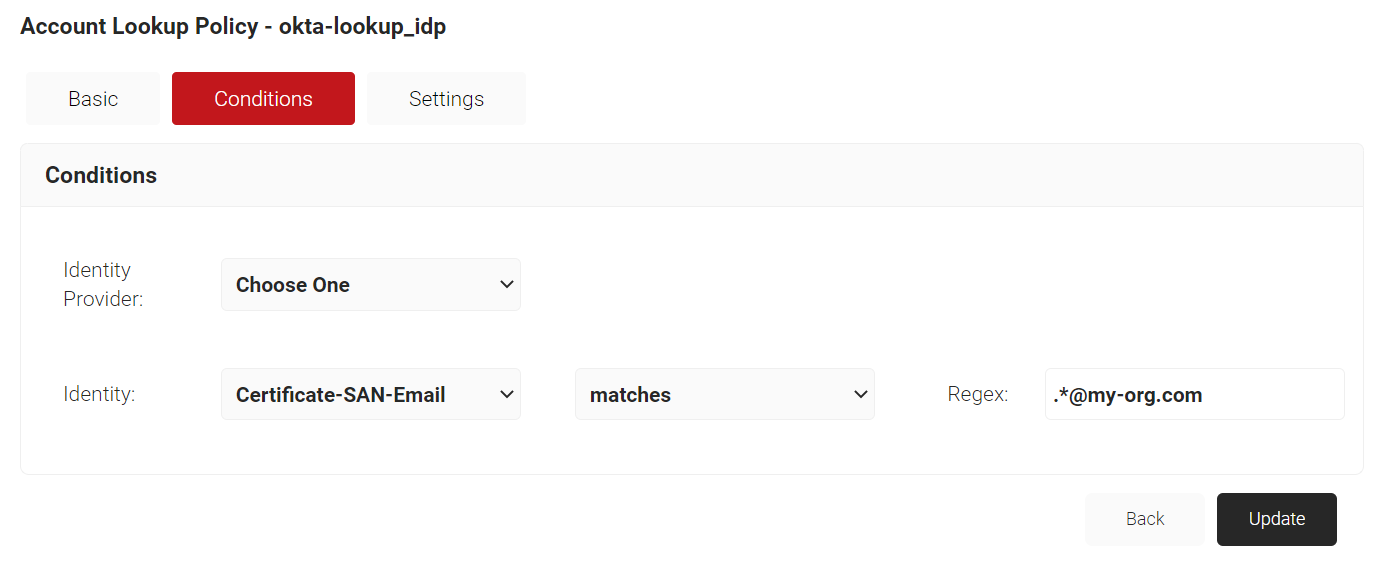
- Click Update.
- Click the Settings tab.
- From the Identity Provider Lookup drop-down list, select the Lookup Identity Provider created earlier (see the Creating Identity Lookup Provider section).
- From the Lookup Type drop-down list, select the lookup type: Auto or Custom.
- From the Identity drop-down list, select an option from the following:
- Username
- Certificate-CommonName
- Certificate-SAN-UPN
- Certificate-SAN-Email
- Certificate-SAN-DNS
- Client ID
- Computer Identity
- Select the Revoke On Failure checkbox.
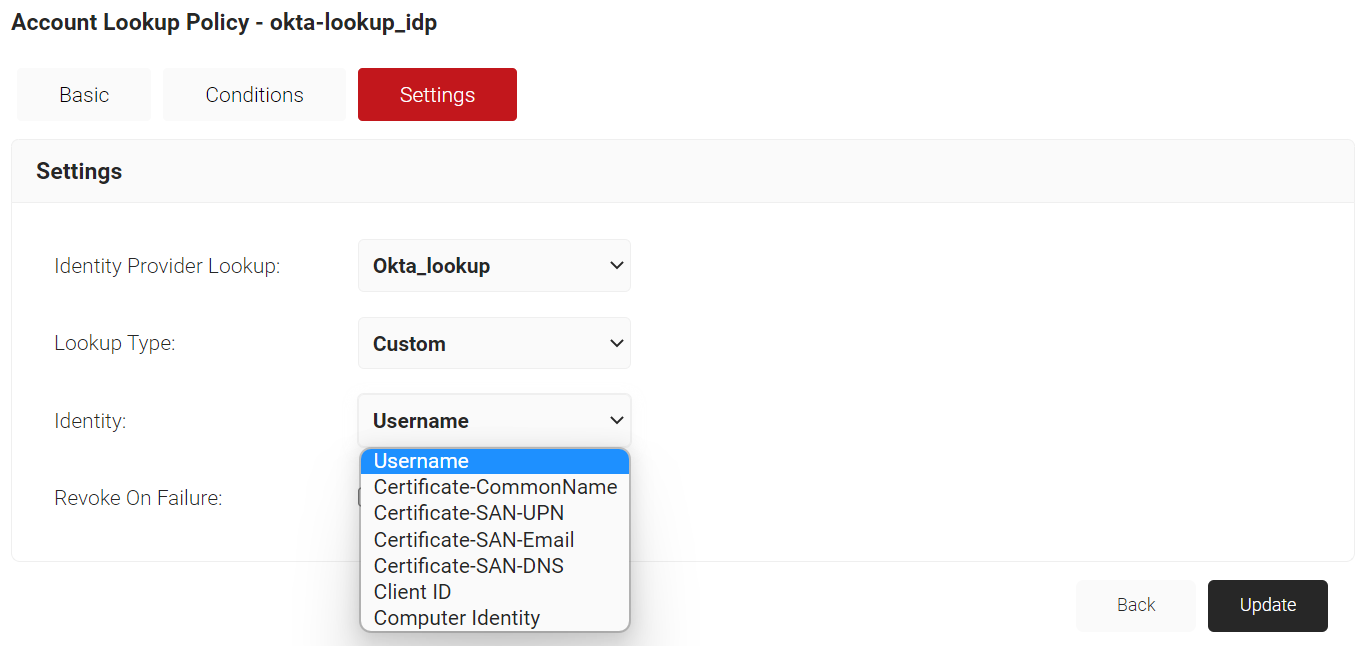
- Click Update.
User Role Policy
User Role Policy for Network Authentication
First, create a role policy for network authentication. This policy is used by Cloud RADIUS Dynamic Policy Engine to lookup the status of a user during authentication. Then Cloud RADIUS can dynamically apply network policies, which you will configure next.
- Navigate to Policy Management > Roles Policies.
- On the Role Policies page, click Add Role.
- On the displayed screen, enter a Name and Display Description for the Role policy.
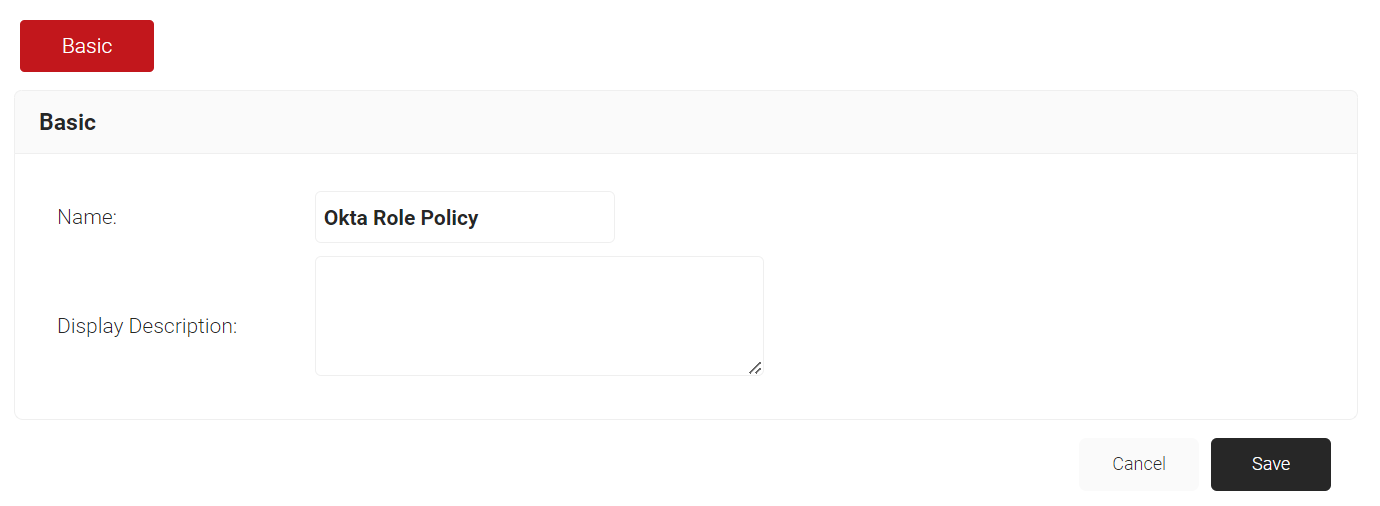 NOTE: Ensure that you create a separate role policy for authentication.
NOTE: Ensure that you create a separate role policy for authentication. - Click Save.
- Click the Conditions tab.
- From the Identity Provider drop-down list, select the Identity Provider you created earlier.
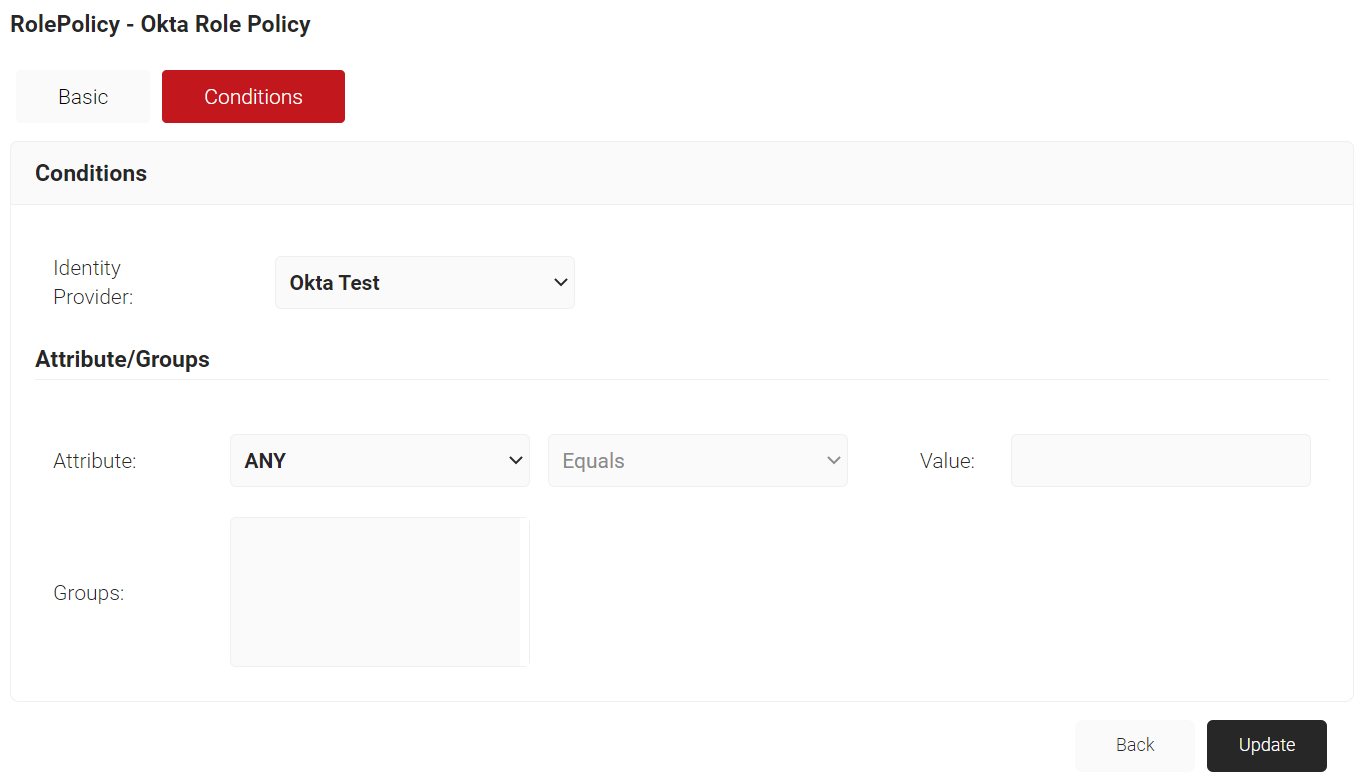
- Click Update.
Group Role Policy for Network Authentication
Next, create role policies for groups that you want to give differentiated network access. We can then leverage Cloud RADIUS' Dynamic Policy Engine to send unique RADIUS attributes based on the users' group with the network policies.
- Navigate to Policy Management > Roles Policies.
- On the Role Policies page, click Add Role.
- On the displayed screen, enter a Name and Display Description for the group role policy.
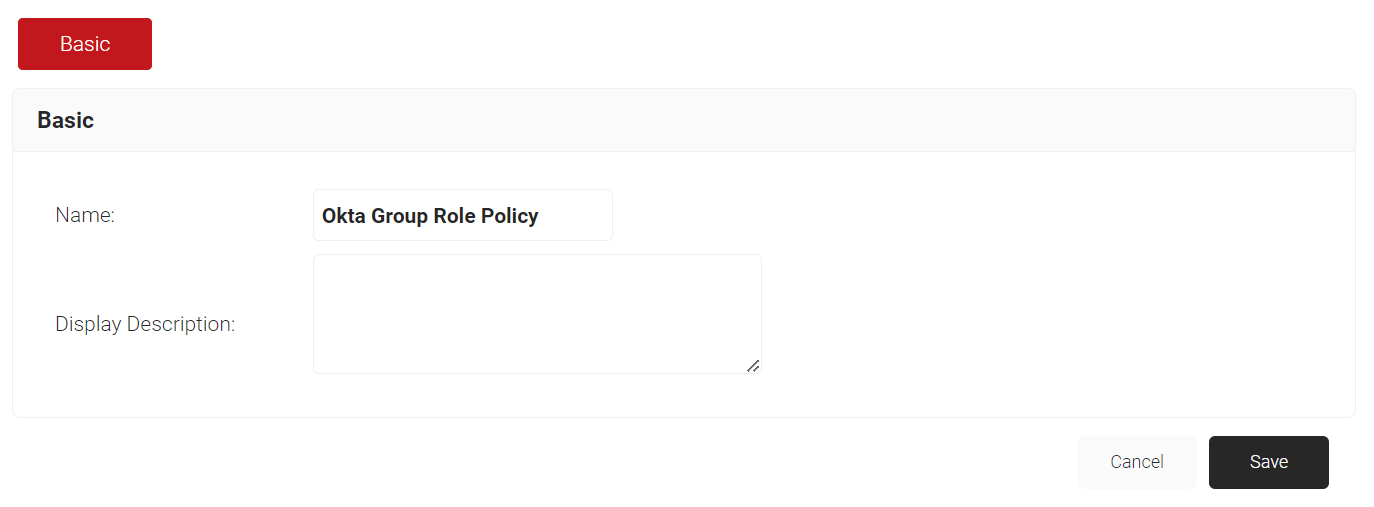
- Click Save.
- Click the Conditions tab.
- From the Identity Provider drop-down-list, select the Okta Identity Lookup Provider you created (see the Creating Identity Lookup Provider section).
- In the Groups field, select the group you want to apply this role to.
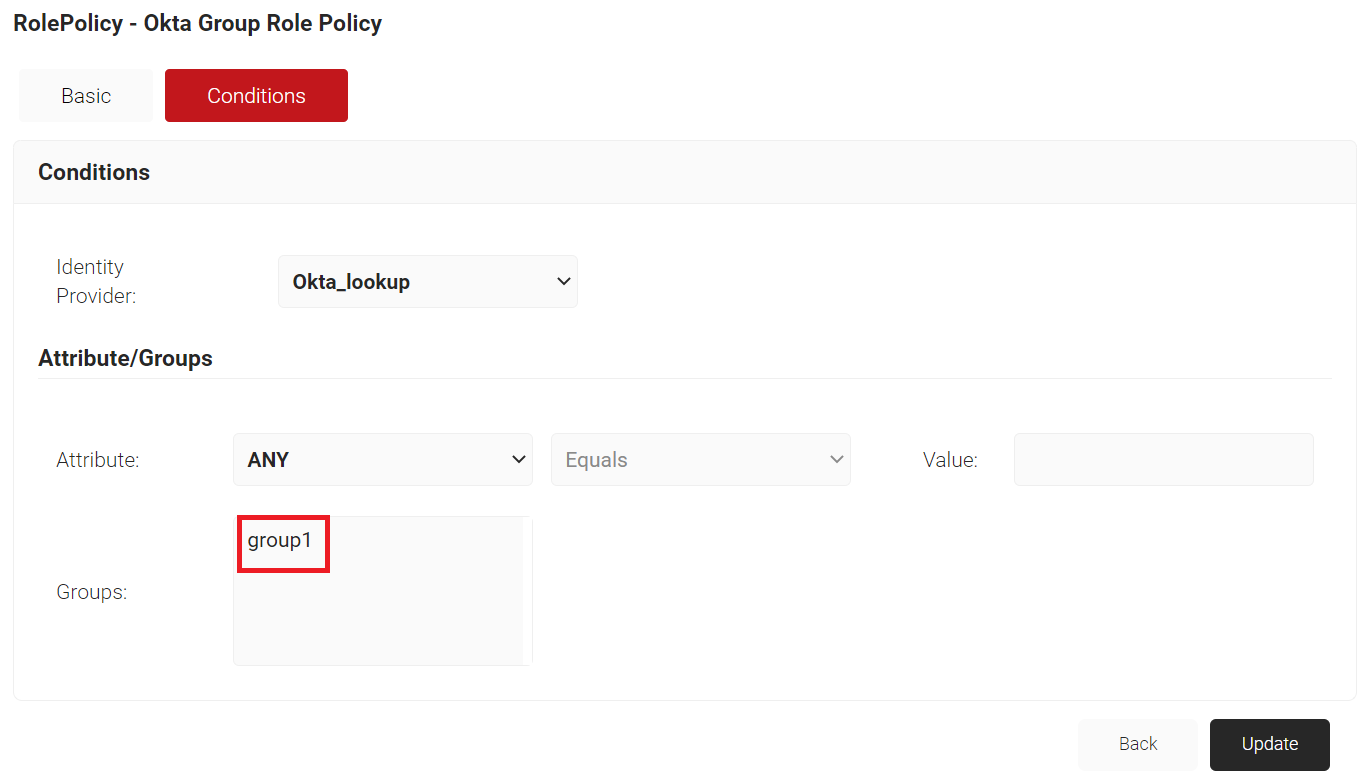 NOTE: The displayed group names are the Local Groups you configured in the Identity Lookup Provider.
NOTE: The displayed group names are the Local Groups you configured in the Identity Lookup Provider. - Click Update.
Default Fallback Role Policy
You may notice that there is a “DEFAULT FALLBACK ROLE POLICY” in your User Role policies after you create a Identity Lookup Provider.
The purpose of this policy is: If the Identity Lookup fails, allow the user to still authenticate to the network but assign them a unique role.
This ensures that both users don’t experience disconnects if there’s a small hiccup in the connection between Okta and Cloud RADIUS, but your network can remain secure and you can have those users auto-assigned into a Guest VLAN.
Note: DEFAULT FALLBACK ROLE POLICY is by default assigned the DEFAULT NETWORK POLICY
Network Policy
The purpose of a Network Policy is to specify how Cloud RADIUS will authorize access to a particular User Role.
A typical Network Policy would say something like: “If User Role = Staff, authorize access and assign them to VLAN 2”.
You can configure any RADIUS Attribute to be sent to the wireless controller. If you leave the attribute section blank, it will just send Access Accept. To create and configure the Network Policy, follow the steps below:
- Navigate to Policy Management > Network Policies.
- On the Network Policies page, click Add Network Policy.
- On the displayed screen, enter a Name and Displayed Description for the network policy in the corresponding fields.
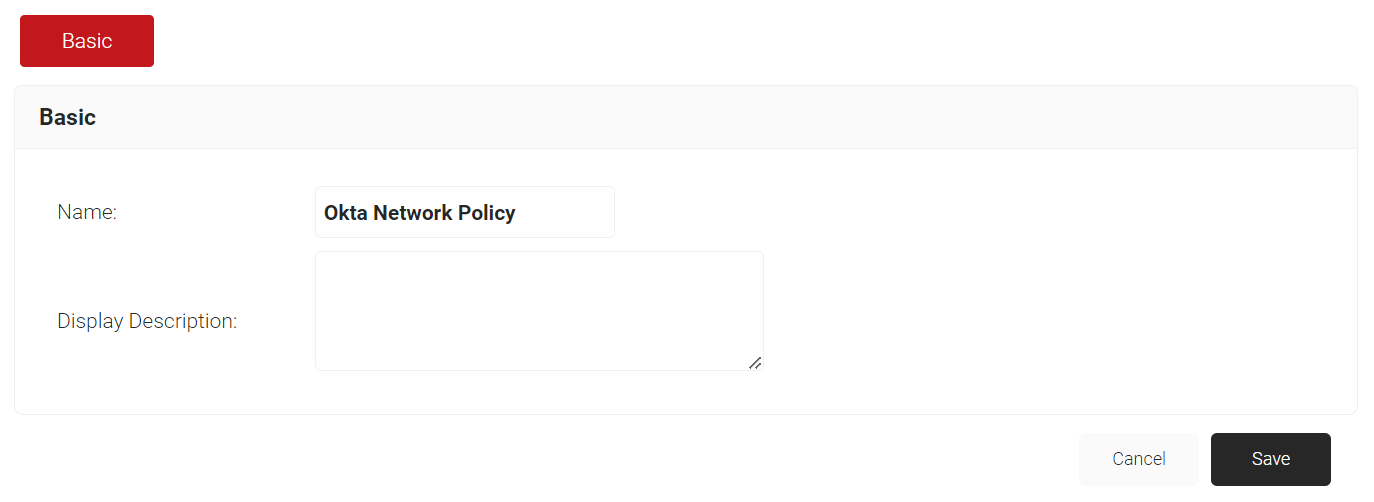
- Click Save.
- Click the Conditions tab.
- Click Add group and select the user role you want to assign to this network policy.
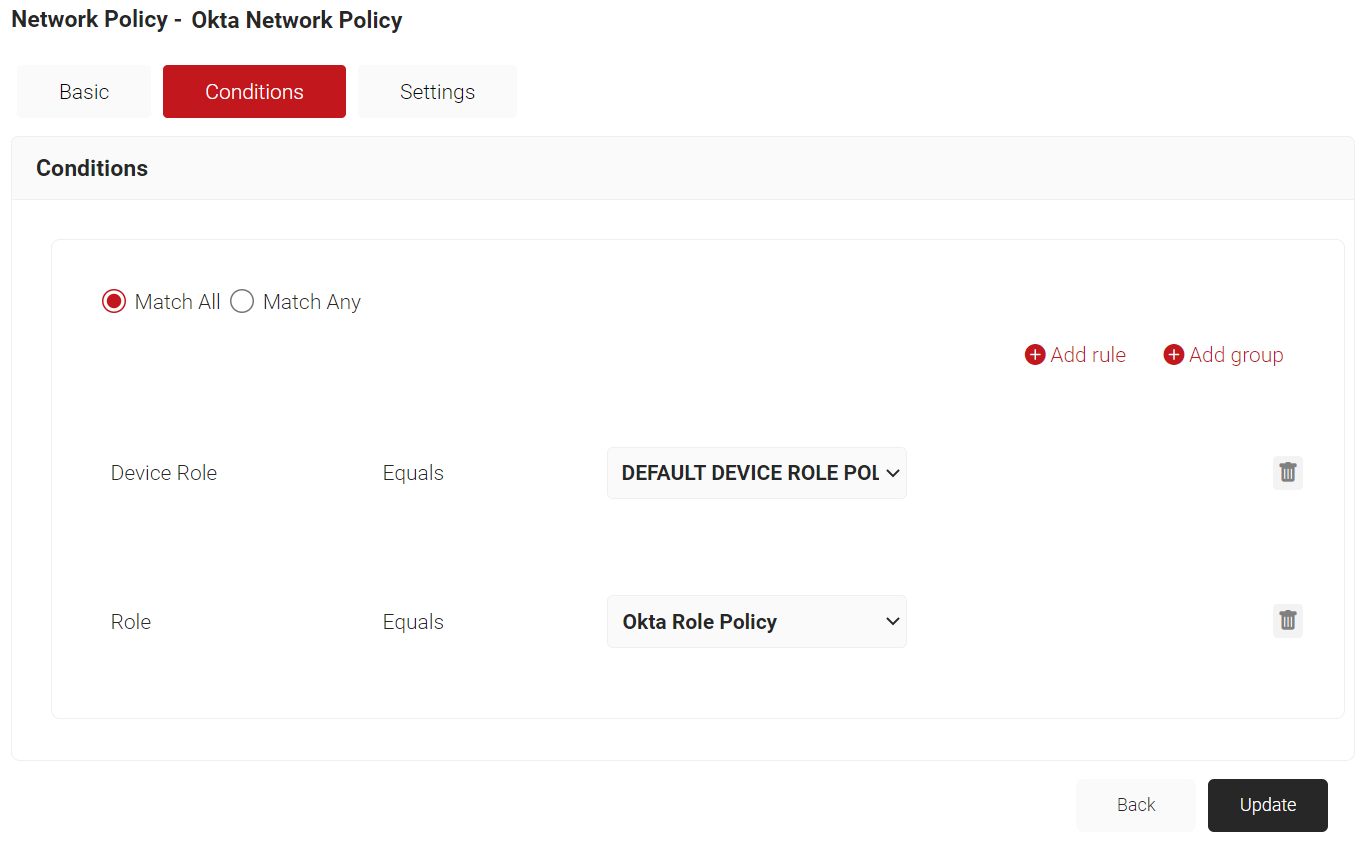 NOTE: You can assign a network policy to multiple user roles.
NOTE: You can assign a network policy to multiple user roles. - Click the Settings tab.
- Click Add Attribute.
- From the Dictionary drop-down-list, select an option: Radius:IETF or Custom.
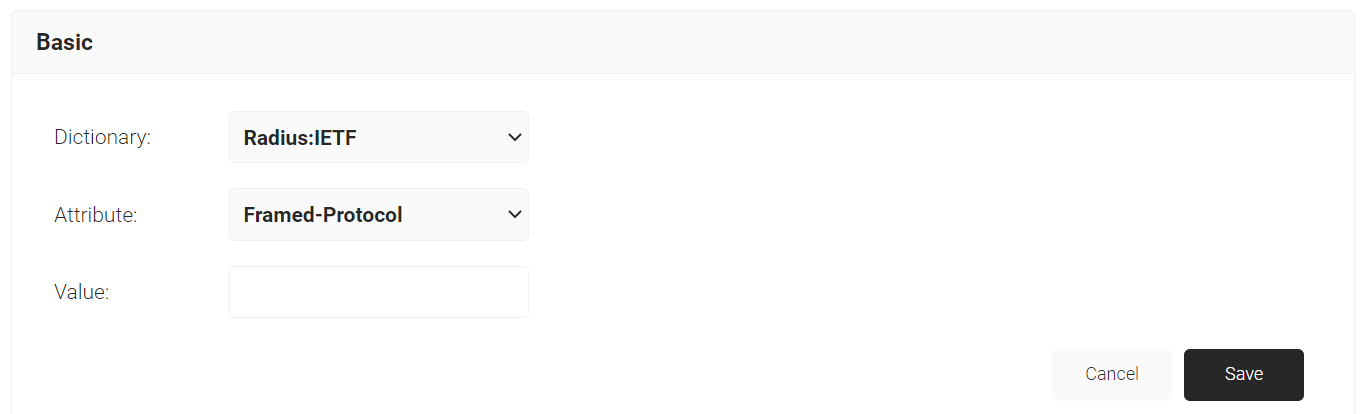
- From the Attribute drop-down-list, select an option.
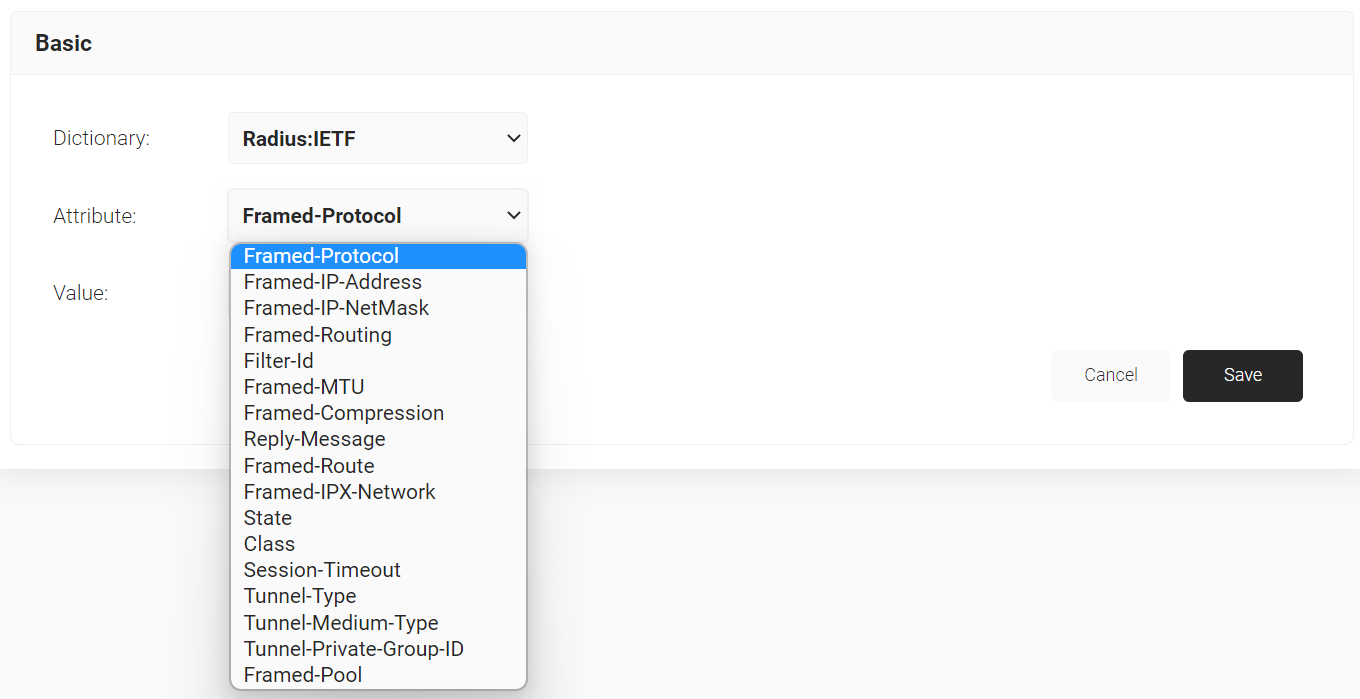
- In the Value field, enter the appropriate value for the attribute.
- Click Save.
- Click Update.
- From the Dictionary drop-down-list, select an option: Radius:IETF or Custom.
NOTE: Repeat the process for all the attributes you want to send to the User Role.
Conclusion
Dynamic RADIUS will revolutionize the way certificate-based WPA2-Enterprise networks are run. It eliminates all traces of security weaknesses and makes it easier to manage certificates and users. SecureW2 has affordable options for organizations of all sizes. Click here to see our pricing.
Schedule a Demo
Sign up for a quick demonstration and see how SecureW2 can make your organization simpler, faster, and more secure.
Schedule NowPricing Information
Our solutions scale to fit you. We have affordable options for organizations of any size. Click here to see our pricing.
Check Pricing
