COVID-19, better known as the Coronavirus, is spreading throughout the world right now and has a lot of people concerned. This has led to scammers incorporating the virus into their phishing attacks to trick people out of their private information and money.
Phishing has alway been a major threat because only one employee needs to be tricked for the whole network to be vulnerable. This is incredibly concerning for small and medium businesses because 60% of SMBs fold 6 months after falling victim to a cyber attack. The average phishing attack for a mid-sized business inflicts over $1 million in damage.
Fortunately, there are solutions out there to prevent email phishing scams from succeeding, like encrypting your email, which we will cover below.
Coronavirus Phishing Attacks
The outbreak of the coronavirus has created a new social engineering vector for phishing scammers by taking advantage of everyone working from home and needing to communicate through emails and webinar meetings.
Here are a couple of examples:
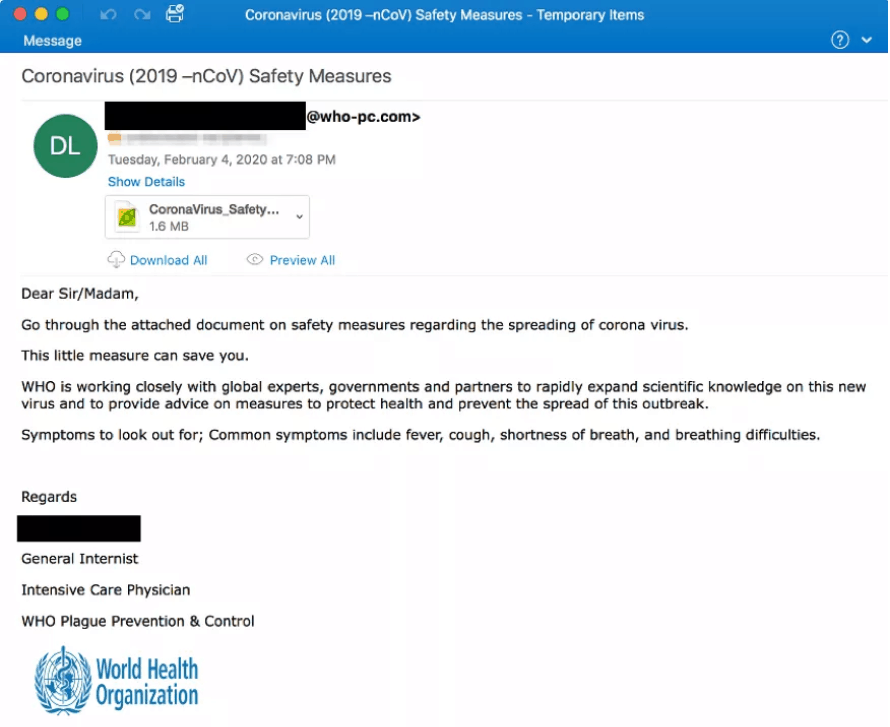
Phishing email impersonating the World Health Organization.
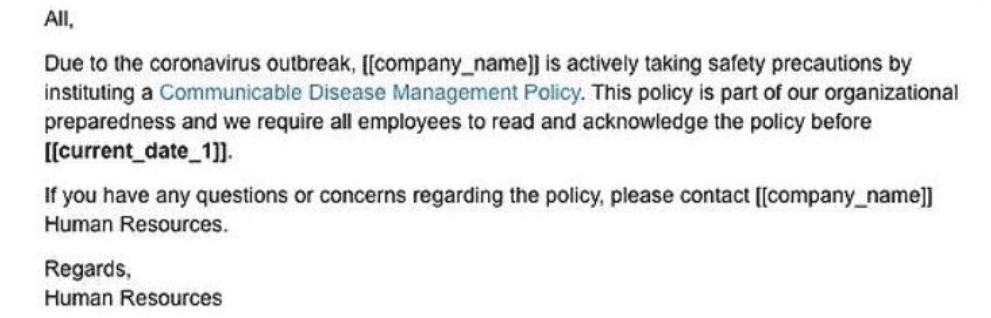
Phishing scam attempting to impersonate a company’s Human Resources department.
But these coronavirus scams don’t stop with phishing. There have also been reports of a coronavirus tracking app for Androids that is infecting devices with ransomware. The device is then locked and the user is required to pay a $100 ransom to unlock.
What makes these attacks particularly effective is that they capitalize on the confusion surrounding the virus. Phishing attempts count on people to make poor judgement choices in an effort to stay safe.
This vulnerability can be extra risky for SMBs who have their employees working from home as many don’t have a proper recovery plan for cyber attacks, increasing their odds of going under.
Can Your Remote MFA Setup Handle The Traffic?
As nonessential businesses phase into primarily remote work, authentication security must face unprecedented challenges and traffic. Of utmost importance is how securely users can access VPN and reduce the risk of an over-the-air attack.
Allowing authentication using only credentials is simply not a secure option for remote workers. Credentials are famously weak in security and can be easily exploited by a number of attacks. In response, many organizations utilize Multi-Factor Authentication (MFA) to add an extra layer of security to their authentication process. But is your MFA vendor prepared for the massive increase in remote traffic?
In the midst of the uncertain event, opting to employ a new MFA vendor isn’t feasible. The process is far too involved to be completed rapidly. What it involves:
- Purchasing and licensing processes
- Integrating into the network and identity databases
- Training employees to connect
- Applying the measure to all applications
That’s just naming a few. So how can you effectively prepare for potential disruptions in your MFA service?
The first thing to do is analyze the most used apps and most important users and ensure redundancy is in place for these particular apps and users. If the vendor begins to waver, you want to guarantee access in these places. Get written assurances from your vendor that they will be able to handle the uptick in activity, which will help to cover your organization and provide a level of confidence.
Lastly, inquire with your vendor about cloud-based MFA. In all aspects, on-premise infrastructure is more expensive and involved to manage, whereas cloud-based infrastructure requires no additional infrastructure or personnel and is easily scalable.
Certificate Security For Email
Phishing emails can do real damage to a business, so the best course of action is implementing a solution to prevent any kind of cyber attack. That solution is configuring email clients with digital certificates.
Setting up a certificate-based network will allow you to create a web of network trust for safe email communication. Many phishing attacks succeed by posing as an IT official and getting a random employee to download malware because they think it is an official IT communication.
Certificate-based networks are able to run S/MIME, which guarantees authoritative trust so the recipient of the email knows for sure they are communicating with the right person.
The Capabilities of S/MIME
Secure/Multipurpose Internet Mail Extensions (S/MIME) are designed for email encryption. SecureW2 offers S/MIME onboarding by leveraging your certificate authorities (which we can provide as well) to deliver certificates in S/MIME to the end points and guaranteeing email client security. Setting up our PKI in your environment isn’t a hassle as our software can integrate into your current infrastructure.
S/MIME’s feature is implementing an additional network of trust by signing each email with an identifier which proves you’re a legitimate sender. When your employees receive an email from you, they know it’s really you. Any type of email without this identification marker will be tagged with a warning.
How Can I Get A Certificate on Every Device?
While certificates have more than proven their security capabilities, many IT admins are caught up in the logistics of getting a certificate onto every device. When done manually, this is a grueling task, but there are solutions to make the process completely automated.
For environments with MDMs, gateway APIs can be set up to connect managed devices to their servers to distribute certificate payloads. SecureW2 is able to work with any major MDM to deliver certificates to every device. Click here for more information on Managed Devices.
You can use onboarding software to have BYODs request a certificate and network access. SecureW2’s JoinNow Suite streamlines the BYOD onboarding process by automating certificate enrollment requests.
Distributing Certificates To Your Devices
SecureW2 offers cloud PKI solutions for your business to run certificate-based digital networks. Our services include S/MIME compatibility, so you’ll be able to encrypt your email client and eliminate the risk of phishing attacks.
The infallible authentication security of certificates makes it an excellent addition to an MFA network. They can be used to authenticate to VPN and ensure all remote employees are protected from the increase in over-the-air attacks.
SecureW2 can be integrated with your current environment, so there’s no need for drastic infrastructure overhaul. Enjoy the strength of Enterprise S/MIME email protection at an affordable cost.


