The cross section of organizations that use Azure AD (Microsoft Entra ID) for identity management and Yubikeys for MFA is already sizable and growing by the day. Recent advancements in authentication security technology has expanded the versatility of Yubikeys, allowing them to be used not just for passwordless authentication to the network but for a great many services.
Read on to learn about how Yubikeys can be enhanced to authenticate Wi-Fi, VPN, desktop login, and most web apps while using your Azure AD directory for authorization.
Passwordless Azure AD (Microsoft Entra ID) Login with Yubikey
Back in February, Microsoft announced support for FIDO2 in hybrid Azure environments, opening the door to passwordless Azure AD authentication with Yubikeys. It was an important step towards the elimination of passwords in enterprise web security.
Early adopters of this joint solution have been able to use their Yubikeys to sign in to Azure AD, replacing their password with a PIN and a tap on the security key. The requirement for physical touch in authentication is what makes physical security tokens like the Yubikey so effective at preventing over-the-air attacks and phishing.
Protect Azure AD Against Phishing
At first glance, the strength of the Yubikey appears to be in its use of digital certificates for asymmetric cryptography, or perhaps the fact that authentication can’t occur unless you physically possess the device. While both contribute to its remarkable record of success, they also address the true pain point that is the preferred method of exploitation by hackers: user experience.
People crave convenience and efficiency, even at the price of security. No one wants to remember a long, complicated password – and certainly no one wants to commit a new one to memory every few months. The hassle of password reset policies and the general confusion surrounding passwords ties up an enormous amount of IT resources. And, despite all that effort, modern processors and password dictionaries make it a simple task to brute force or password spray your way into the network.
Passwords and password management are hard, so hackers trick people into using easier methods that compromise their credentials. Most hacking isn’t done with clever code – it’s done with clever words and manipulative psychology and we call it phishing.
Security keys pull the rug out from under hackers by offering an even easier way to authenticate – just tap on the device.
Enterprise Yubikey Management for Passwordless Azure AD
The current iteration of passwordless authentication for Azure AD is a big improvement over passwords, but it has one significant obstacle to wide-scale implementation – scalability.
Azure AD is valued because it can scale infinitely and it remains easily manageable. Unfortunately, Yubikeys cannot claim the same thing. They’re a pain to set up because each one has to be manually configured via command line interface with the correct certificates to enable the Azure integration. That task is too complicated to be left to the end user, which means that deploying pre-configured Yubikeys to an organization becomes a huge task for IT.
Given the repetitive nature of the task and the inevitability of mistakes, manually configuring an enterprise fleet of security keys will likely create some unnoticed vulnerabilities in your network perimeter. In our capacity as an official Yubico Partner, SecureW2 has developed a smart card management solution (SCMS) for Yubikey that enables enterprise-level Yubikey configuration and management.
By pushing a payload that includes an automatic configuration package, Yubikeys can be induced to self-enroll for certificates upon first-time setup. Our customizable onboarding client walks end users through a foolproof setup process that ties their identity and existing Azure AD credentials to the Yubikey, with optional PIN/PUK complexity requirements.
Here’s a quick .gif that shows the enrollment process for end users:
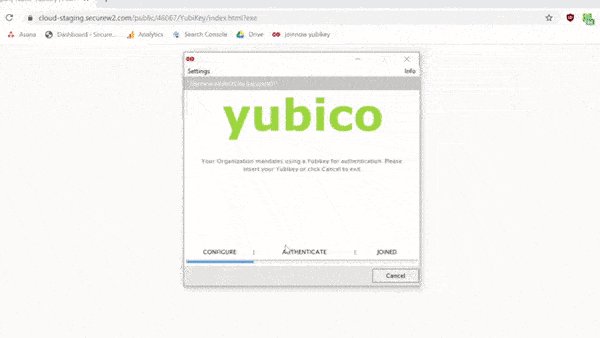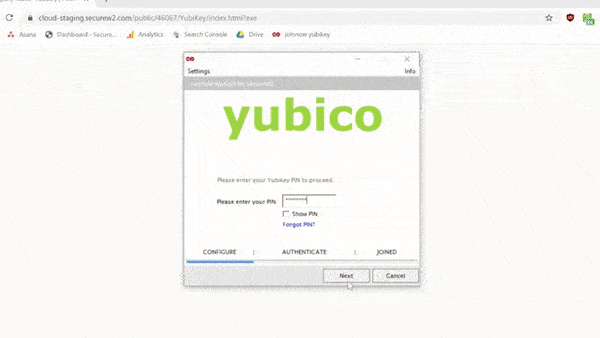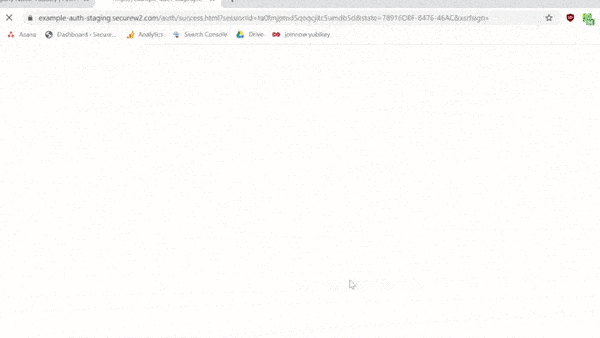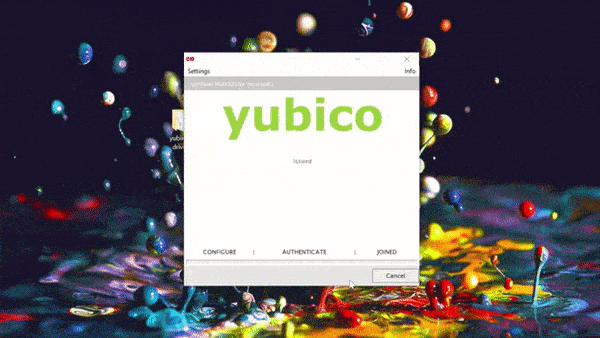
Additionally, SecureW2 uses a newer feature where the management key is randomized and stored in the Yubikey itself. You will have to authenticate using the four-digit PIN to access the management key. This solves the problem of remembering or storing the relatively long management key.
The management key is needed to perform particular tasks, such as onboarding a new certificate or storing the private key in the Yubikey. Since the management key cannot be used for identity theft and is used for limited functions, it does not have the three-authentication attempt lock-out feature, and anyone with access to the four-digit PIN can potentially figure out the management key and become a potential security risk that may sometimes get ignored.
By randomizing the management key and storing it in the Yubikey, the security risk is mitigated to a greater degree. Using this feature does add a few additional steps for the IT in that they will have to ask the end user for the PIN and authenticate using it to access the management key. However, for the end user, there is no difference in the user experience, and they are not involved in this back-end activity.
Use Azure AD for Wi-Fi, VPN, and Desktop Login via Yubikey
If ease-of-use weren’t compelling enough, our Yubikey SCMS solution for Azure AD also expands the reach of both products. By integrating our product into your PKI, or by tying your Azure directory into our own industry-leading Cloud PKI, you can use x.509 digital certificates to authenticate several new types of requests.
Using certificates for facets of your network perimeter is the easiest way to significantly enhance the strength of your network security. Storing those certificates on a Yubikey adds an invaluable MFA element to your security, allowing you to be confident that you are protected from over-the-air attacks and phishing.
You already have Yubikeys and Azure AD, why not use them for more? Easier and more secure Wi-Fi, VPN, and desktop login is only the tip of the iceberg – you can use it for most any web application or service that supports SSO or OAuth. We have affordable options for organizations of all sizes, click here to see our pricing page.